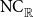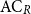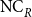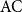1. Introduction
Boolean circuits as a computational model are a fundamental concept in the study of theoretical computer science. Mainly in computational complexity, Boolean circuits play a central part in the analysis of parallel algorithms and the corresponding complexity classes, enabling a finer view and providing new proof methods, especially for subpolynomial complexity classes. An obvious generalization of Boolean circuits is that instead of dealing with truth values as inputs – or the field
![]() ${\mathbb{Z}}_2$
for the algebraically minded – we consider elements from some other algebraic structure. This approach has its roots in the works of Blum, Shub and Smale, whose model of the BSS-machine is able to describe computations over real numbers. Following this, Blum, Shub, Smale and Cucker (Blum et al., Reference Blum, Cucker, Shub and Smale1998) also give a generalization to algebraic circuits over the reals.
${\mathbb{Z}}_2$
for the algebraically minded – we consider elements from some other algebraic structure. This approach has its roots in the works of Blum, Shub and Smale, whose model of the BSS-machine is able to describe computations over real numbers. Following this, Blum, Shub, Smale and Cucker (Blum et al., Reference Blum, Cucker, Shub and Smale1998) also give a generalization to algebraic circuits over the reals.
1.1 Our contribution
In this article, we provide logical characterizations of circuit complexity classes over integral domains. In particular, we define natural extensions of the classical circuit complexity hierarchies
![]() $\mathrm{AC}^{i}$
and
$\mathrm{AC}^{i}$
and
![]() $\mathrm{NC}^{i}$
over arbitrary integral domains. The resulting classes are denoted as
$\mathrm{NC}^{i}$
over arbitrary integral domains. The resulting classes are denoted as
![]() $\mathrm{AC}_{R}^{i}$
and
$\mathrm{AC}_{R}^{i}$
and
![]() $\mathrm{NC}_R^{i}$
, respectively. We adapt the framework of metafinite model theory to define various extensions of first-order logic, which capture these new complexity classes.
$\mathrm{NC}_R^{i}$
, respectively. We adapt the framework of metafinite model theory to define various extensions of first-order logic, which capture these new complexity classes.
We establish a Immerman-style theorem stating that
![]() $\mathrm{FO}_{R} ={\mathrm{AC}_R^{0}}$
and provide a framework to establish complexity-theoretic comparisons of classes with different underlying integral domains and give examples over which integral domain the
$\mathrm{FO}_{R} ={\mathrm{AC}_R^{0}}$
and provide a framework to establish complexity-theoretic comparisons of classes with different underlying integral domains and give examples over which integral domain the
![]() $\mathrm{AC}^{0}$
classes are equal.
$\mathrm{AC}^{0}$
classes are equal.
We adapt the
![]() $\mathrm{GPR}$
operator, which Durand, Haak and Vollmer use to provide logical characterizations of
$\mathrm{GPR}$
operator, which Durand, Haak and Vollmer use to provide logical characterizations of
![]() $\mathrm{AC}^{1}$
and
$\mathrm{AC}^{1}$
and
![]() $\mathrm{NC}^{1}$
(Durand et al., Reference Durand, Haak and Vollmer2018) to logics over metafinite structures and extend it to be able to characterize the whole
$\mathrm{NC}^{1}$
(Durand et al., Reference Durand, Haak and Vollmer2018) to logics over metafinite structures and extend it to be able to characterize the whole
![]() $\mathrm{AC}_{R}$
and
$\mathrm{AC}_{R}$
and
![]() $\mathrm{NC}_R^{}$
hierarchies.
$\mathrm{NC}_R^{}$
hierarchies.
Finally, we define a formalism suitable for comparing complexity classes with different underlying integral domains and we show that a hierarchy of sets of complexity classes emerges, such that each set is able to “simulate” the complexity classes from the sets lower in the hierarchy.
1.2 Related work
Another model of computation that is commonly known under the name “algebraic circuit” are Valiant circuits (Valiant, Reference Valiant1979), which are the foundational model in the emerging subfields of algebraic and geometric complexity theory. They differ from the model we analyse in this work in the way that we use
![]() $\lt$
gates, which are not available in the Valiant setting. This difference is of complexity-theoretical significance, since for our model, we have that
$\lt$
gates, which are not available in the Valiant setting. This difference is of complexity-theoretical significance, since for our model, we have that
![]() $\mathrm{NC}_{\mathbb{R}}^{i} \subsetneq \mathrm{NC}_{\mathbb{R}}^{i + 1}$
(Cucker, Reference Cucker1992) but we have that
$\mathrm{NC}_{\mathbb{R}}^{i} \subsetneq \mathrm{NC}_{\mathbb{R}}^{i + 1}$
(Cucker, Reference Cucker1992) but we have that
![]() $\mathrm{VNC^2} =\mathrm{VNC^3} = \ldots = \mathrm{VP}$
(Bürgisser, Reference Bürgisser2013) in the Valiant setting for every field, in particular over the reals.
$\mathrm{VNC^2} =\mathrm{VNC^3} = \ldots = \mathrm{VP}$
(Bürgisser, Reference Bürgisser2013) in the Valiant setting for every field, in particular over the reals.
1.3 Outline of the paper
We start with an overview of some central concepts from algebra and circuit complexity, which are needed for the definition of our model. We then establish our model of algebraic circuits for arbitrary integral domains and the analogous complexity classes induced by them in analogy to the Boolean case. Afterwards, we give a logical characterization of the presented circuit classes inspired by classical descriptive complexity. However, since our models now have an infinite component, we build on the foundations of metafinite model theory.
We then go on to define first-order logic over
![]() $R$
and show that, like in the classical case, we have that
$R$
and show that, like in the classical case, we have that
![]() ${\mathrm{AC}_{R}^{0}} = \mathrm{FO}_{R}[{\mathrm{Arb}_{R}}]+\mathrm{SUM}_{R} + \mathrm{PROD}_{R}$
.
${\mathrm{AC}_{R}^{0}} = \mathrm{FO}_{R}[{\mathrm{Arb}_{R}}]+\mathrm{SUM}_{R} + \mathrm{PROD}_{R}$
.
In Section 4, we give logical characterizations of
![]() $\mathrm{AC}^{i}$
and
$\mathrm{AC}^{i}$
and
![]() $\mathrm{NC}^{i}$
. The tool of our choice is an adaptation of the guarded predicative logic of Durand et al. (Reference Durand, Haak and Vollmer2018).
$\mathrm{NC}^{i}$
. The tool of our choice is an adaptation of the guarded predicative logic of Durand et al. (Reference Durand, Haak and Vollmer2018).
In Section 5, we discuss connections between
![]() $\mathrm{AC}_{R}^{0}$
classes over different integral domains.
$\mathrm{AC}_{R}^{0}$
classes over different integral domains.
2. Preliminaries
First, we discuss the theoretical background of this paper. We give the basic definitions and remarks on the notation used in this paper. We denote the set of natural numbers with
![]() $0$
as
$0$
as
![]() $\mathbb{N}$
and the set of natural numbers without
$\mathbb{N}$
and the set of natural numbers without
![]() $0$
as
$0$
as
![]() ${\mathbb{N}}_{\gt 0}$
.
${\mathbb{N}}_{\gt 0}$
.
Notation 1.
In this paper, we will generally use overlined letters (e. g.
![]() $\overline{x}$
) to denote tuples.
$\overline{x}$
) to denote tuples.
As the name suggests, algebraic circuit classes make use of concepts originating from abstract algebra. We assume the reader has basic knowledge of algebra, especially rings, integral domains and fields, polynomials and adjoining elements to rings. For an introduction to abstract algebra, the reader may refer to the books by Aluffi (Reference Aluffi2009) or Lang (Reference Lang2002).
Our considered rings are always assumed to be a commutative ring with unit. Throughout the paper, whenever not otherwise specified, we use
![]() $R$
to denote an infinite integral domain.
$R$
to denote an infinite integral domain.
Remark 2. In particular, we require that for every
![]() $r \in R$
the equations
$r \in R$
the equations
hold.
Example 3.
Popular examples of rings include
![]() ${\mathbb{Z}},{\mathbb{Q}},{\mathbb{R}}$
and
${\mathbb{Z}},{\mathbb{Q}},{\mathbb{R}}$
and
![]() $\mathbb{C}$
, as well as sets with adjoined elements like
$\mathbb{C}$
, as well as sets with adjoined elements like
![]() ${\mathbb{Z}}[j],{\mathbb{Z}}[\sqrt [p]{-1}],{\mathbb{Z}}[\sqrt{p},\sqrt{q},\ldots ]$
,
${\mathbb{Z}}[j],{\mathbb{Z}}[\sqrt [p]{-1}],{\mathbb{Z}}[\sqrt{p},\sqrt{q},\ldots ]$
,
![]() ${\mathbb{R}}[j_{k}],{\mathbb{Z}}[j_{k}], \ldots$
, where
${\mathbb{R}}[j_{k}],{\mathbb{Z}}[j_{k}], \ldots$
, where
![]() $k\in \mathbb{N}$
,
$k\in \mathbb{N}$
,
![]() $p \neq q$
are primes and
$p \neq q$
are primes and
![]() $j_{k}$
denotes the
$j_{k}$
denotes the
![]() $k$
th root of
$k$
th root of
![]() $-1$
, that is
$-1$
, that is
![]() $i_{k}^k = -1$
. Alternatively, we can adjoin
$i_{k}^k = -1$
. Alternatively, we can adjoin
![]() $\ell$
algebraic independent prime root elements with
$\ell$
algebraic independent prime root elements with
![]() $2^\ell = k$
and get an analogous construction.
$2^\ell = k$
and get an analogous construction.
Remark 4. The denotation of
![]() ${\mathbb{R}}[j_{k}]$
resp.
${\mathbb{R}}[j_{k}]$
resp.
![]() ${\mathbb{Z}}[j_{k}]$
is not unique but the constructions of the circuit over the underlying rings are analogous except for the placeholders for the adjoined numbers. For example,
${\mathbb{Z}}[j_{k}]$
is not unique but the constructions of the circuit over the underlying rings are analogous except for the placeholders for the adjoined numbers. For example,
![]() ${\mathbb{Z}}^4$
can denote
${\mathbb{Z}}^4$
can denote
![]() ${\mathbb{Z}}[j_4]={\mathbb{Z}}[j_4,j_4^2,j_4^3]$
or
${\mathbb{Z}}[j_4]={\mathbb{Z}}[j_4,j_4^2,j_4^3]$
or
![]() ${\mathbb{Z}}[\sqrt{2},\sqrt{5}]={\mathbb{Z}}[\sqrt{2},\sqrt{5},\sqrt{10}]$
or many other rings. Since we only focus on the structure of the tuples, that is the coefficients of adjoint elements, or later the underlying circuits, our short notation for
${\mathbb{Z}}[\sqrt{2},\sqrt{5}]={\mathbb{Z}}[\sqrt{2},\sqrt{5},\sqrt{10}]$
or many other rings. Since we only focus on the structure of the tuples, that is the coefficients of adjoint elements, or later the underlying circuits, our short notation for
![]() ${\mathbb{Z}}^k$
for arbitrary
${\mathbb{Z}}^k$
for arbitrary
![]() $k\gt 1$
is not unique and may differ, for example
$k\gt 1$
is not unique and may differ, for example
![]() ${\mathbb{Z}}^2$
may denote
${\mathbb{Z}}^2$
may denote
![]() ${\mathbb{Z}}[j]$
or may denote
${\mathbb{Z}}[j]$
or may denote
![]() $\mathbb{Q}$
. In the context of the placeholder notation, the arithmetic of the specific ring must be clear, if it is important.
$\mathbb{Q}$
. In the context of the placeholder notation, the arithmetic of the specific ring must be clear, if it is important.
We need some ordering
![]() $\lt$
on our integral domain
$\lt$
on our integral domain
![]() $R$
. In some cases, like
$R$
. In some cases, like
![]() $\mathbb{R}$
and
$\mathbb{R}$
and
![]() $\mathbb{Z}$
, we have some natural ordering that we want to use. In other cases, like
$\mathbb{Z}$
, we have some natural ordering that we want to use. In other cases, like
![]() $\mathbb{C}$
, we have to construct some ordering. This ordering does not have to be closed under multiplication, and we only have to distinguish different numbers from each other. So an ordering on tuples (
$\mathbb{C}$
, we have to construct some ordering. This ordering does not have to be closed under multiplication, and we only have to distinguish different numbers from each other. So an ordering on tuples (
![]() $z_1=a_1+b_1i, z_2=a_2+b_2i \in{\mathbb{C}}: (a_1,b_1) \lt _{\mathbb{C}} (a_2,b_2) \iff a_1 \lt _{\mathbb{R}} a_2 \text{ or }a_1 = a_2 \text{ and } b_1 \lt _{\mathbb{R}} b_2$
) is possible.
$z_1=a_1+b_1i, z_2=a_2+b_2i \in{\mathbb{C}}: (a_1,b_1) \lt _{\mathbb{C}} (a_2,b_2) \iff a_1 \lt _{\mathbb{R}} a_2 \text{ or }a_1 = a_2 \text{ and } b_1 \lt _{\mathbb{R}} b_2$
) is possible.
Definition 5.
A strict total order on a set
![]() $S$
is a binary relation
$S$
is a binary relation
![]() $\lt$
on
$\lt$
on
![]() $S$
which is irreflexive, transitive and total.
$S$
which is irreflexive, transitive and total.
Example 6.
For some field
![]() $\mathbb{F}_{p^k}$
for some prime
$\mathbb{F}_{p^k}$
for some prime
![]() $p$
and a natural number
$p$
and a natural number
![]() $k$
, we write the finitely many elements in a list and then use the lexicographical on this list. For example, let
$k$
, we write the finitely many elements in a list and then use the lexicographical on this list. For example, let
![]() $R={\mathbb{Z}}_3$
. Then, we define
$R={\mathbb{Z}}_3$
. Then, we define
![]() $\lt _{{\mathbb{Z}}_3}$
as
$\lt _{{\mathbb{Z}}_3}$
as
![]() $0\lt 1\lt 2$
.
$0\lt 1\lt 2$
.
There are multiple possibilities for such a
![]() $\lt$
over the field of complex numbers. Let
$\lt$
over the field of complex numbers. Let
![]() $z = a+bj \in{\mathbb{C}}$
and let
$z = a+bj \in{\mathbb{C}}$
and let
![]() $\lt _1$
be the lexicographic order on pairs
$\lt _1$
be the lexicographic order on pairs
![]() $(\sqrt{a^2+b^2},a)$
. Furthermore, let
$(\sqrt{a^2+b^2},a)$
. Furthermore, let
![]() $\lt _2$
be the lexicographic order on pairs of the form
$\lt _2$
be the lexicographic order on pairs of the form
![]() $(a,b)$
. Then, both variants are possible since both distinguish different complex numbers.
$(a,b)$
. Then, both variants are possible since both distinguish different complex numbers.
Definition 7.
A strict total order
![]() $\lt$
over a ring
$\lt$
over a ring
![]() $R$
induces a
$R$
induces a
![]() $\textrm{sign}$
function as follows:
$\textrm{sign}$
function as follows:
 \begin{equation*} \textrm {sign}_{(R,\lt )}(x) = \begin {cases} 1 & \text {if } x \gt 0\\[5pt] 0 & \text {otherwise.} \end {cases} \end{equation*}
\begin{equation*} \textrm {sign}_{(R,\lt )}(x) = \begin {cases} 1 & \text {if } x \gt 0\\[5pt] 0 & \text {otherwise.} \end {cases} \end{equation*}
In the following, unless explicitly otherwise specified, the symbol
![]() $R$
denotes an infinite integral domain with a strict total order
$R$
denotes an infinite integral domain with a strict total order
![]() $\lt$
on
$\lt$
on
![]() $R$
. Most of the rings we consider have a natural ordering. In this case, we omit the ordering symbol.
$R$
. Most of the rings we consider have a natural ordering. In this case, we omit the ordering symbol.
2.1 Algebraic circuits over
 $R$
$R$
As this work is a generalization of the well established Boolean circuits, some background in circuit complexity is assumed. Standard literature which introduces this topic is the book by Vollmer (Reference Vollmer1999). The generalization to algebraic circuits over real numbers were first introduced by Cucker (Reference Cucker1992). In analogy to them, Barlag and Vollmer defined an unbounded fan-in version of algebraic circuits (Barlag and Vollmer, Reference Barlag and Vollmer2021).
Definition 8.
We define an algebraic circuit
![]() $C$
over an integral domain
$C$
over an integral domain
![]() $R$
with a strict total order
$R$
with a strict total order
![]() $\lt$
, or
$\lt$
, or
![]() $R$
circuit for short, as a directed acyclic graph. It has gates of the following types:
$R$
circuit for short, as a directed acyclic graph. It has gates of the following types:
Input nodes have indegree
![]() $0$
and contain the respective input values of the circuit.
$0$
and contain the respective input values of the circuit.
Constant nodes have indegree
![]() $0$
and are labelled with elements of
$0$
and are labelled with elements of
![]() $R$
$R$
Arithmetic nodes have an arbitrary indegree
![]() $\ge 1$
, bounded by the number of nodes in the circuit and are labelled with either
$\ge 1$
, bounded by the number of nodes in the circuit and are labelled with either
![]() $+$
or
$+$
or
![]() $\times$
.
$\times$
.
Comparison (
![]() $\lt$
) nodes have indegree
$\lt$
) nodes have indegree
![]() $2$
.
$2$
.
Output nodes have indegree
![]() $1$
and contain the output value after the computation of the circuit.
$1$
and contain the output value after the computation of the circuit.
Nodes cannot be predecessors of the same node more than once, and thus, the outdegree of nodes in these algebraic circuits is bounded by the number of gates in the circuit.
During the computation of an algebraic circuit, the arithmetic gates compute their respective functions with the values of their predecessor gates being taken as the function arguments and the comparison gates compute the characteristic function of
![]() $\lt$
in the same way. The values of the output gates at the end of the computation are the result of the computation.
$\lt$
in the same way. The values of the output gates at the end of the computation are the result of the computation.
In contrast to the classical setting, where we consider words over an alphabet
![]() $\Sigma$
as inputs, and where languages are thus defined to be subsets of the Kleene closure of the alphabet (in symbols,
$\Sigma$
as inputs, and where languages are thus defined to be subsets of the Kleene closure of the alphabet (in symbols,
![]() $L\subseteq \Sigma ^*$
), we consider vectors of integral domain elements as input. In analogy to
$L\subseteq \Sigma ^*$
), we consider vectors of integral domain elements as input. In analogy to
![]() $\Sigma ^*$
, we denote for an integral domain
$\Sigma ^*$
, we denote for an integral domain
![]() $R$
:
$R$
:
With
![]() $\lvert x\rvert$
, we denote the length of
$\lvert x\rvert$
, we denote the length of
![]() $x$
, i. e., if
$x$
, i. e., if
![]() $x \in R^k$
then
$x \in R^k$
then
![]() $\lvert x\rvert = k$
.
$\lvert x\rvert = k$
.
Remark 9. We will use the term algebraic circuit to describe circuits in the sense of Blum et al. (Reference Blum, Cucker, Shub and Smale1998) rather than arithmetic circuits as for example in Barlag and Vollmer (Reference Barlag and Vollmer2021) to distinguish them from arithmetic circuits in the sense of Valiant, see for example (Bürgisser et al., Reference Bürgisser, Clausen and Shokrollahi1997). Valiant circuits are essentially algebraic circuits without
![]() $\textrm{sign}$
or comparison gates (Blum et al., Reference Blum, Cucker, Shub and Smale1998, page 350).
$\textrm{sign}$
or comparison gates (Blum et al., Reference Blum, Cucker, Shub and Smale1998, page 350).
Remark 10. In the special case
![]() $R ={\mathbb{Z}}_2$
, the definition above yields exactly the Boolean circuits.
$R ={\mathbb{Z}}_2$
, the definition above yields exactly the Boolean circuits.
Definition 11. We call the number of gates in a circuit the size of the circuit and the longest path from an input gate to an output gate the depth of the circuit.
Remark 12. Unlike the way algebraic circuits with unbounded fan-in gates were introduced previously (Barlag and Vollmer, Reference Barlag and Vollmer2021), algebraic circuits in this context have comparison gates instead of
![]() $\textrm{sign}$
gates. This stems from the fact that when dealing with real or complex numbers, we can construct a
$\textrm{sign}$
gates. This stems from the fact that when dealing with real or complex numbers, we can construct a
![]() $\textrm{sign}$
function from
$\textrm{sign}$
function from
![]() $\lt$
via Definition 7 and the order relation from the
$\lt$
via Definition 7 and the order relation from the
![]() $\textrm{sign}$
function via
$\textrm{sign}$
function via
If we consider finite integral domains, however, suddenly it becomes less clear how to construct the
![]() $\lt$
relation from the
$\lt$
relation from the
![]() $\textrm{sign}$
function, while the other way around still works by Definition 7.
$\textrm{sign}$
function, while the other way around still works by Definition 7.
Given that we define circuits and logic fragments relative to an ordering, it is natural for both to have access to this ordering. Therefore, we choose to use
![]() $\lt$
gates rather than
$\lt$
gates rather than
![]() $\textrm{sign}$
gates. So in the following, all usages of
$\textrm{sign}$
gates. So in the following, all usages of
![]() $\textrm{sign}$
are implicit uses of the order relation as by Definition 7.
$\textrm{sign}$
are implicit uses of the order relation as by Definition 7.
In the cases which are considered in other literature (
![]() $\mathbb R$
or
$\mathbb R$
or
![]() $\mathbb F_2$
), this has no complexity-theoretic impact, since in the emulation of one formalism using the other, we get a linear overhead in the size and constant overhead in the depth of the circuit.
$\mathbb F_2$
), this has no complexity-theoretic impact, since in the emulation of one formalism using the other, we get a linear overhead in the size and constant overhead in the depth of the circuit.
In order to define complexity classes with respect to algebraic circuits, we have to define the function calculated by such a circuit and define the term of circuit families.
Definition 13.
The (
![]() $n$
ary) function
$n$
ary) function
![]() $f_C\colon R^n \to R^m$
computed by an
$f_C\colon R^n \to R^m$
computed by an
![]() $R$
circuit
$R$
circuit
![]() $C$
(with
$C$
(with
![]() $n$
input gates and
$n$
input gates and
![]() $m$
output gates) is defined by
$m$
output gates) is defined by
where
![]() $y_1, \dots, y_m$
are the values of the output gates of
$y_1, \dots, y_m$
are the values of the output gates of
![]() $C$
, when given
$C$
, when given
![]() $x_1, \ldots, x_n$
as its inputs.
$x_1, \ldots, x_n$
as its inputs.
Definition 14.
A family of
![]() $R$
circuits
$R$
circuits
![]() ${\mathcal{C}} ={(C_n)}_{n \in{\mathbb{N}}}$
is a sequence of circuits which contains one circuit for every input length
${\mathcal{C}} ={(C_n)}_{n \in{\mathbb{N}}}$
is a sequence of circuits which contains one circuit for every input length
![]() $n \in{\mathbb{N}}$
. The function
$n \in{\mathbb{N}}$
. The function
![]() $f_{\mathcal{C}}\colon R^*\to R^*$
computed by a circuit family
$f_{\mathcal{C}}\colon R^*\to R^*$
computed by a circuit family
![]() $\mathcal{C}$
is defined by
$\mathcal{C}$
is defined by
The size (resp. depth) of a circuit family
![]() ${(C_n)}_{n \in{\mathbb{N}}}$
is defined as a function mapping
${(C_n)}_{n \in{\mathbb{N}}}$
is defined as a function mapping
![]() $n \in{\mathbb{N}}$
to the size (resp. depth) of
$n \in{\mathbb{N}}$
to the size (resp. depth) of
![]() $C_n$
.
$C_n$
.
Analogously to the classical case, we say that a set
![]() $S\subseteq R^*$
can be decided by a circuit family
$S\subseteq R^*$
can be decided by a circuit family
![]() $\mathcal C$
, if
$\mathcal C$
, if
![]() $\mathcal C$
can compute the characteristic function of
$\mathcal C$
can compute the characteristic function of
![]() $S$
.
$S$
.
Definition 15.
Let
![]() $f_1, f_2 \colon{\mathbb{N}} \to{\mathbb{N}}$
be two functions. We then write
$f_1, f_2 \colon{\mathbb{N}} \to{\mathbb{N}}$
be two functions. We then write
![]() ${\boldsymbol{UnbSizeDepth}_{R}}(f_1, f_2)$
to denote the class of sets decidable by
${\boldsymbol{UnbSizeDepth}_{R}}(f_1, f_2)$
to denote the class of sets decidable by
![]() $R$
circuit families of size
$R$
circuit families of size
![]() ${\mathcal{O}}(f_1(n))$
and depth
${\mathcal{O}}(f_1(n))$
and depth
![]() ${\mathcal{O}}(f_2(n))$
. We write
${\mathcal{O}}(f_2(n))$
. We write
![]() ${\boldsymbol{SizeDepth}_{R}}(f_1, f_2)$
to denote the class of sets decidable by
${\boldsymbol{SizeDepth}_{R}}(f_1, f_2)$
to denote the class of sets decidable by
![]() $R$
circuit families of size
$R$
circuit families of size
![]() ${\mathcal{O}}(f_1(n))$
and depth
${\mathcal{O}}(f_1(n))$
and depth
![]() ${\mathcal{O}}(f_2(n))$
, where each arithmetic gate has indegree bounded by
${\mathcal{O}}(f_2(n))$
, where each arithmetic gate has indegree bounded by
![]() $2$
(we call this bounded fan-in).
$2$
(we call this bounded fan-in).
Definition 16.
![]() ${\mathrm{AC}_{R}^{i}} \;:=\;{\boldsymbol{UnbSizeDepth}_{R}}(n^{{\mathcal{O}}(1)}, (\log _2 n)^i)$
${\mathrm{AC}_{R}^{i}} \;:=\;{\boldsymbol{UnbSizeDepth}_{R}}(n^{{\mathcal{O}}(1)}, (\log _2 n)^i)$
Definition 17.
![]() $\mathrm{NC}_R^{i} \;:=\;{\boldsymbol{SizeDepth}_{R}}(n^{{\mathcal{O}}(1)}, (\log _2 n)^i)$
$\mathrm{NC}_R^{i} \;:=\;{\boldsymbol{SizeDepth}_{R}}(n^{{\mathcal{O}}(1)}, (\log _2 n)^i)$
Remark 18. The circuit families we have just introduced do not have any restrictions on the difficulty of constructing any individual circuit given the input length. If it is important to know how hard obtaining a particular circuit is, one can consider so-called uniform circuit families. These families require their circuits to meet restrictions on the difficulties of obtaining them. For more information on uniformity, cf. (Vollmer, Reference Vollmer1999).
Uniformity criteria can be defined for algebraic circuit classes in a similar way. See for example (Blum et al., Reference Blum, Cucker, Shub and Smale1998, Section 18.5).
2.2 Structures and first-order logic over integral domains
As we want to characterize circuit complexity classes with logical fragments, this work falls broadly under the umbrella of finite model theory and, in particular, descriptive complexity. Foundational knowledge of these topics is assumed and can be found in the books by Grädel et al. (Reference Grädel, Kolaitis, Libkin, Marx, Spencer, Vardi, Venema and Weinstein2007); Immerman (Reference Immerman1999); and Libkin (Reference Libkin2004). Traditionally, descriptive complexity is viewed as a subdiscipline of finite model theory. In our setting, however, we want to (carefully) introduce infinite structures to our reasoning. For this, we use metafinite model theory, an extension of the finite model formalism first introduced by (Grädel and Gurevich, Reference Grädel and Gurevich1998). A short introduction to metafinite model theory is also featured in the book by Grädel et al. Reference Grädel, Kolaitis, Libkin, Marx, Spencer, Vardi, Venema and Weinstein2007, page 210). The approach was taken by Grädel and Meer (Reference Grädel and Meer1995) to describe some essential complexity classes over real numbers. These descriptions were later extended by Cucker and Meer (Reference Cucker and Meer1999), where, among other things, the
![]() $\mathrm{NC}$
hierarchy over real numbers was defined. For their logical characterizations, these papers introduce a so-called first-order logic with arithmetics, which we will adapt to be used in our setting.
$\mathrm{NC}$
hierarchy over real numbers was defined. For their logical characterizations, these papers introduce a so-called first-order logic with arithmetics, which we will adapt to be used in our setting.
To make proofs easier, we will make use of the well-known trick that any predicate can be emulated by its characteristic function. Thus we only consider predicates, when convenient. We can furthermore emulate constants in the usual way by
![]() $0$
ary functions.
$0$
ary functions.
Definition 19.
Let
![]() $L_s$
,
$L_s$
,
![]() $L_f$
be finite vocabularies which only contain function symbols. An
$L_f$
be finite vocabularies which only contain function symbols. An
![]() $R$
structure of signature
$R$
structure of signature
![]() $\sigma = (L_s, L_f)$
is a pair
$\sigma = (L_s, L_f)$
is a pair
![]() ${\mathcal{D}} = ({\mathcal{A}}, F)$
where
${\mathcal{D}} = ({\mathcal{A}}, F)$
where
-
1.
 $\mathcal{A}$
is a finite structure of vocabulary
$\mathcal{A}$
is a finite structure of vocabulary
 $L_s$
which we call the skeleton of
$L_s$
which we call the skeleton of
 $\mathcal{D}$
whose universe
$\mathcal{D}$
whose universe
 $A$
we will refer to as the universe of
$A$
we will refer to as the universe of
 $\mathcal{D}$
and whose cardinality we will refer to by
$\mathcal{D}$
and whose cardinality we will refer to by
 $\lvert A\rvert$
$\lvert A\rvert$
-
2. and
 $F$
is a finite set which contains functions of the form
$F$
is a finite set which contains functions of the form
 $X \colon A^k \rightarrow R$
for
$X \colon A^k \rightarrow R$
for
 $k \in{\mathbb{N}}$
which interpret the function symbols in
$k \in{\mathbb{N}}$
which interpret the function symbols in
 $L_f$
.
$L_f$
.
We will use
![]() ${{STRUC}_{R}}(\sigma )$
to refer to the set of all
${{STRUC}_{R}}(\sigma )$
to refer to the set of all
![]() $R$
structures of signature
$R$
structures of signature
![]() $\sigma$
, and we will assume that for any signature
$\sigma$
, and we will assume that for any signature
![]() $\sigma = (L_s, L_f)$
, the symbols in
$\sigma = (L_s, L_f)$
, the symbols in
![]() $L_s$
and
$L_s$
and
![]() $L_f$
are ordered.
$L_f$
are ordered.
Remark 20. In this paper, we only consider ranked structures, that is structures, in which the skeleton is ordered.
It often comes in handy to be able to encode an
![]() $R$
structure
$R$
structure
![]() $\mathcal{D}$
over a signature
$\mathcal{D}$
over a signature
![]() $\sigma$
as an element of
$\sigma$
as an element of
![]() $R^*$
. We do so by simply concatenating the function values of all functions of
$R^*$
. We do so by simply concatenating the function values of all functions of
![]() $\mathcal{D}$
in lexicographical order with respect to the function arguments.
$\mathcal{D}$
in lexicographical order with respect to the function arguments.
Example 21.
Let
![]() $A = \{\diamondsuit, \spadesuit \}$
,
$A = \{\diamondsuit, \spadesuit \}$
,
![]() $f_1 = \{\diamondsuit \mapsto 1, \spadesuit \mapsto 0\}$
,
$f_1 = \{\diamondsuit \mapsto 1, \spadesuit \mapsto 0\}$
,
![]() $f_2 = \{\diamondsuit \mapsto \pi, \spadesuit \mapsto 42\}$
and let
$f_2 = \{\diamondsuit \mapsto \pi, \spadesuit \mapsto 42\}$
and let
![]() ${\mathcal{D}} = ({\mathcal{A}}, F)$
be an
${\mathcal{D}} = ({\mathcal{A}}, F)$
be an
![]() $R$
structure with universe
$R$
structure with universe
![]() $A$
,
$A$
,
![]() $\diamondsuit$
being ranked below
$\diamondsuit$
being ranked below
![]() $\spadesuit$
and
$\spadesuit$
and
![]() $F = \{f_1, f_2\}$
. Then,
$F = \{f_1, f_2\}$
. Then,
![]() $\mathcal{D}$
gets encoded as
$\mathcal{D}$
gets encoded as
![]() $(1, 0, \pi, 42)$
.
$(1, 0, \pi, 42)$
.
Definition 22 (First-order logic over
![]() $R$
). The language of first-order logic over an integral domain
$R$
). The language of first-order logic over an integral domain
![]() $R$
contains for each signature
$R$
contains for each signature
![]() $\sigma = (L_s, L_f)$
a set of formulae and terms. The terms are divided into index terms which take values in universe of the skeleton and number terms which take values in
$\sigma = (L_s, L_f)$
a set of formulae and terms. The terms are divided into index terms which take values in universe of the skeleton and number terms which take values in
![]() $R$
. These terms are inductively defined as follows:
$R$
. These terms are inductively defined as follows:
-
1. The set of index terms is defined as the closure of the set of variables
 $V$
under applications of the function symbols of
$V$
under applications of the function symbols of
 $L_s$
.
$L_s$
. -
2. Any element of
 $R$
is a number term.
$R$
is a number term.
-
3. For index terms
 $h_1, \ldots, h_k$
and a
$h_1, \ldots, h_k$
and a
 $k$
ary function symbol
$k$
ary function symbol
 $X \in L_f$
,
$X \in L_f$
,
 $X(h_1, \ldots, h_k)$
is a number term.
$X(h_1, \ldots, h_k)$
is a number term.
-
4. If
 $t_1$
,
$t_1$
,
 $t_2$
are number terms, then so are
$t_2$
are number terms, then so are
 $t_1 + t_2$
,
$t_1 + t_2$
,
 $t_1 \times t_2$
and
$t_1 \times t_2$
and
 $\textrm{sign}(t_1)$
.
$\textrm{sign}(t_1)$
.
Atomic formulae are equalities of index terms
![]() $h_1 = h_2$
and number terms
$h_1 = h_2$
and number terms
![]() $t_1 = t_2$
, inequalities of number terms
$t_1 = t_2$
, inequalities of number terms
![]() $t_1 \lt t_2$
and expressions of the form
$t_1 \lt t_2$
and expressions of the form
![]() $P(h_1, \ldots, h_k)$
, where
$P(h_1, \ldots, h_k)$
, where
![]() $P \in L_s$
is a k-ary predicate symbol and
$P \in L_s$
is a k-ary predicate symbol and
![]() $h_1, .., h_k$
are index terms.
$h_1, .., h_k$
are index terms.
The set
![]() $\mathrm{FO}_{R}$
is the smallest set which contains the closure of atomic formulae under the logical connectives
$\mathrm{FO}_{R}$
is the smallest set which contains the closure of atomic formulae under the logical connectives
![]() $\{\land, \lor, \neg, \to, \leftrightarrow \}$
and quantification
$\{\land, \lor, \neg, \to, \leftrightarrow \}$
and quantification
![]() $\exists v \psi$
and
$\exists v \psi$
and
![]() $\forall v \psi$
where
$\forall v \psi$
where
![]() $v$
ranges over
$v$
ranges over
![]() $\mathcal{A}$
.
$\mathcal{A}$
.
For better readability, we will use inequalities of the form
![]() $x \leq y$
and the extensions of equalities
$x \leq y$
and the extensions of equalities
![]() ${\overline{x}} ={\overline{y}}$
and the inequalities
${\overline{x}} ={\overline{y}}$
and the inequalities
![]() ${\overline{x}} \lt{\overline{y}}$
and
${\overline{x}} \lt{\overline{y}}$
and
![]() ${\overline{x}} \leq{\overline{y}}$
to tuples throughout this paper. Note that these extensions are easily definable from
${\overline{x}} \leq{\overline{y}}$
to tuples throughout this paper. Note that these extensions are easily definable from
![]() $=$
and
$=$
and
![]() $\lt$
in first-order logic.
$\lt$
in first-order logic.
Remark 23. We call any element of
![]() $R$
a number term even though some integral domains can contain elements like
$R$
a number term even though some integral domains can contain elements like
![]() $\zeta$
,
$\zeta$
,
![]() $\aleph$
or
$\aleph$
or
![]() $\circledast$
which are not numbers.
$\circledast$
which are not numbers.
Equivalence of
![]() $\mathrm{FO}_{R}$
formulae and sets defined by
$\mathrm{FO}_{R}$
formulae and sets defined by
![]() $\mathrm{FO}_{R}$
formulae are done in the usual way, that is a formula
$\mathrm{FO}_{R}$
formulae are done in the usual way, that is a formula
![]() $\varphi$
defines a set
$\varphi$
defines a set
![]() $S$
if and only if the elements of
$S$
if and only if the elements of
![]() $S$
are exactly the encodings of
$S$
are exactly the encodings of
![]() $R$
structures under which
$R$
structures under which
![]() $\varphi$
holds and two such formulae are said to be equivalent if and only if they define the same set.
$\varphi$
holds and two such formulae are said to be equivalent if and only if they define the same set.
With the goal in mind to create a logic which can define sets decided by circuits with unbounded fan-in, we introduce new rules for building number terms: the sum and the product rule. We will also define a further rule, which we call the maximization rule. This one is, however, already definable in
![]() $\mathrm{FO}_{R}$
, and we thus do not gain any expressive power by using it. We will use it to show that we can represent characteristic functions in
$\mathrm{FO}_{R}$
, and we thus do not gain any expressive power by using it. We will use it to show that we can represent characteristic functions in
![]() $\mathrm{FO}_{R}$
.
$\mathrm{FO}_{R}$
.
Definition 24 (Sum, product and maximization rule). Let
![]() $t$
be a number term in which the variables
$t$
be a number term in which the variables
![]() $\overline{x}$
and the variables
$\overline{x}$
and the variables
![]() $\overline{w}$
occur freely and let
$\overline{w}$
occur freely and let
![]() $A$
denote the universe of the given input structure. Then,
$A$
denote the universe of the given input structure. Then,
is also a number term which is interpreted as
![]() $\sum _{{\overline{x}} \in A^{\lvert{\overline{x}}\rvert }}t({\overline{x}},{\overline{w}})$
. The number terms
$\sum _{{\overline{x}} \in A^{\lvert{\overline{x}}\rvert }}t({\overline{x}},{\overline{w}})$
. The number terms
![]() $\textbf{prod}_{\overline{x}}(t({\overline{x}},{\overline{w}}))$
and
$\textbf{prod}_{\overline{x}}(t({\overline{x}},{\overline{w}}))$
and
![]() $\textbf{max}_{{\overline{x}}}(t({\overline{x}},{\overline{w}}))$
are defined analogously.
$\textbf{max}_{{\overline{x}}}(t({\overline{x}},{\overline{w}}))$
are defined analogously.
We call these operators aggregators, and for any formula
![]() $\varphi$
containing aggregators of the above form, the variables in
$\varphi$
containing aggregators of the above form, the variables in
![]() $\overline{x}$
are considered bound in
$\overline{x}$
are considered bound in
![]() $\varphi$
.
$\varphi$
.
Example 25.
Let
![]() $\sigma = (\{\}, \{f_E^2\})$
be the signature of weighted graphs, that is
$\sigma = (\{\}, \{f_E^2\})$
be the signature of weighted graphs, that is
![]() $L_s$
is empty and
$L_s$
is empty and
![]() $L_f$
contains the single function symbol
$L_f$
contains the single function symbol
![]() $f_E$
which is interpreted such that
$f_E$
which is interpreted such that
![]() $f_E(x, y)$
gives the weight of the edge from
$f_E(x, y)$
gives the weight of the edge from
![]() $x$
to
$x$
to
![]() $y$
or
$y$
or
![]() $0$
if there is none. Let
$0$
if there is none. Let
![]() $\mathcal{G}$
be a (graph) structure over
$\mathcal{G}$
be a (graph) structure over
![]() $\sigma$
. Then, the following
$\sigma$
. Then, the following
![]() $\mathrm{FO}_{R} +{\textrm{SUM}_{R}}$
sentence
$\mathrm{FO}_{R} +{\textrm{SUM}_{R}}$
sentence
![]() $\varphi$
states that there is a node in the skeleton of
$\varphi$
states that there is a node in the skeleton of
![]() $\mathcal{G}$
, for which the sum of its outgoing edges is more than double the sum of the outgoing edges of any other node.
$\mathcal{G}$
, for which the sum of its outgoing edges is more than double the sum of the outgoing edges of any other node.
Observation 26.
![]() $\mathrm{FO}_{R} = \mathrm{FO}_{R} +{\textrm{MAX}_{R}}$
.
$\mathrm{FO}_{R} = \mathrm{FO}_{R} +{\textrm{MAX}_{R}}$
.
Proof.
An occurrence of
![]() $\textbf{max}_{i}(F(i))$
essentially assures that there exists an element
$\textbf{max}_{i}(F(i))$
essentially assures that there exists an element
![]() $x$
, such that for all elements
$x$
, such that for all elements
![]() $y$
,
$y$
,
![]() $F(x) \geq F(y)$
and takes the value of
$F(x) \geq F(y)$
and takes the value of
![]() $F(x)$
. Clearly, this can be defined in fist order logic by a formula of the form
$F(x)$
. Clearly, this can be defined in fist order logic by a formula of the form
![]() $\forall x \exists y F(x) \geq F(y)$
.
$\forall x \exists y F(x) \geq F(y)$
.
Furthermore, any characteristic function of a logical formula can be described in
![]() $\mathrm{FO}_{R}$
. The proof for this runs analogously to that of Cucker and Meer Reference Cucker and Meer1999, Proposition 2), since this proof does not make any use of special properties of the reals.
$\mathrm{FO}_{R}$
. The proof for this runs analogously to that of Cucker and Meer Reference Cucker and Meer1999, Proposition 2), since this proof does not make any use of special properties of the reals.
3.
 $\textrm{AC}^{0}_{R} = \textrm{FO}_{R}$
$\textrm{AC}^{0}_{R} = \textrm{FO}_{R}$
In this section, we present a proof that
![]() $\mathrm{FO}_{R}$
captures the class
$\mathrm{FO}_{R}$
captures the class
![]() $\mathrm{AC}_{{R}}^{0}$
. The proof idea is similar to the proof of the established result by Immerman which characterizes
$\mathrm{AC}_{{R}}^{0}$
. The proof idea is similar to the proof of the established result by Immerman which characterizes
![]() $\mathrm{AC}^{0}$
via
$\mathrm{AC}^{0}$
via
![]() $\mathrm{FO}$
.
$\mathrm{FO}$
.
When using logics to check, whether a given
![]() $R$
tuple would be accepted by a
$R$
tuple would be accepted by a
![]() $R$
circuit, one needs to think about how this
$R$
circuit, one needs to think about how this
![]() $R$
tuple would be interpreted as an
$R$
tuple would be interpreted as an
![]() $R$
structure
$R$
structure
![]() $\mathcal{A}$
. This can be done by interpreting it as the set of the circuit’s input gates along with a single unary function
$\mathcal{A}$
. This can be done by interpreting it as the set of the circuit’s input gates along with a single unary function
![]() $f_{\mathrm{element}} \colon A \to R$
mapping the
$f_{\mathrm{element}} \colon A \to R$
mapping the
![]() $i$
th input gate to the
$i$
th input gate to the
![]() $i$
th input of the circuit. We call this kind of structure a circuit structure.
$i$
th input of the circuit. We call this kind of structure a circuit structure.
In the following, we would like to extend
![]() $\mathrm{FO}_{R}$
by additional functions and relations that are not given in the input structure. To that end, we make a small addition to Definition 19 where we defined
$\mathrm{FO}_{R}$
by additional functions and relations that are not given in the input structure. To that end, we make a small addition to Definition 19 where we defined
![]() $R$
structures. Whenever we talk about
$R$
structures. Whenever we talk about
![]() $R$
structures over a signature
$R$
structures over a signature
![]() $(L_s, L_f)$
, we now also consider structures over signatures of the form
$(L_s, L_f)$
, we now also consider structures over signatures of the form
![]() $(L_s, L_f, L_a)$
. The additional (also ordered) vocabulary
$(L_s, L_f, L_a)$
. The additional (also ordered) vocabulary
![]() $L_a$
does not have any effect on the
$L_a$
does not have any effect on the
![]() $R$
structure, but it contains function symbols, which can be used in a logical formula with this signature. This means that any
$R$
structure, but it contains function symbols, which can be used in a logical formula with this signature. This means that any
![]() $R$
structure of signature
$R$
structure of signature
![]() $(L_s, L_f)$
is also an
$(L_s, L_f)$
is also an
![]() $R$
structure of signature
$R$
structure of signature
![]() $(L_s, L_f, L_a)$
for any vocabulary
$(L_s, L_f, L_a)$
for any vocabulary
![]() $L_a$
. The symbols in
$L_a$
. The symbols in
![]() $L_a$
stand for functions that we will use to extend the expressive power of
$L_a$
stand for functions that we will use to extend the expressive power of
![]() $\mathrm{FO}_{R}$
to capture various complexity classes.
$\mathrm{FO}_{R}$
to capture various complexity classes.
Definition 27.
Let
![]() $F$
be a set of finitary functions. We will write
$F$
be a set of finitary functions. We will write
![]() $\mathrm{FO}_{R}[F]$
to denote the class of sets that can be defined by
$\mathrm{FO}_{R}[F]$
to denote the class of sets that can be defined by
![]() $\mathrm{FO}_{R}$
sentences which can make use of the functions in
$\mathrm{FO}_{R}$
sentences which can make use of the functions in
![]() $F$
in addition to what they are given in their structure.
$F$
in addition to what they are given in their structure.
Formally, this means that
![]() $\mathrm{FO}_{R}[F]$
describes exactly those sets
$\mathrm{FO}_{R}[F]$
describes exactly those sets
![]() $S \subseteq R^*$
for which there exists an
$S \subseteq R^*$
for which there exists an
![]() $\mathrm{FO}_{R}$
sentence
$\mathrm{FO}_{R}$
sentence
![]() $\varphi$
over a signature
$\varphi$
over a signature
![]() $\sigma = (L_s, L_f, L_a)$
such that for each length
$\sigma = (L_s, L_f, L_a)$
such that for each length
![]() $n$
, there is an interpretation
$n$
, there is an interpretation
![]() $I_n$
interpreting the symbols in
$I_n$
interpreting the symbols in
![]() $L_a$
as elements of
$L_a$
as elements of
![]() $F$
such that for all
$F$
such that for all
![]() $R^*$
tuples
$R^*$
tuples
![]() $s$
of length
$s$
of length
![]() $n$
it holds that
$n$
it holds that
![]() $s \in S$
if and only if
$s \in S$
if and only if
![]() $s$
encodes an
$s$
encodes an
![]() $R$
structure over
$R$
structure over
![]() $(L_s, L_f, L_a)$
which models
$(L_s, L_f, L_a)$
which models
![]() $\varphi$
when using
$\varphi$
when using
![]() $I_n$
.
$I_n$
.
Example 28.
Let us take as an example the scenario where we are given a graph as a structure but want to make use of additional functions to interpret that graph as a circuit, by having those functions determine the gate types of the nodes in the graph. We will use the signature
![]() $\sigma = (\{E^2\}, \{\}, \{f_{\textit{out}}^1, f_{\textit{add}}^1, f_{\textit{in}}^1\})$
, and we will use a set of functions
$\sigma = (\{E^2\}, \{\}, \{f_{\textit{out}}^1, f_{\textit{add}}^1, f_{\textit{in}}^1\})$
, and we will use a set of functions
![]() $F = \{F_{\textit{out,1}}, F_{\textit{out,2}}, \dots, F_{\textit{add,1}}, F_{\textit{add,2}}, \dots, F_{\textit{in,1}}, F_{\textit{in,2}}, \dots \}$
, where each function is a characteristic function which maps the nodes of the graph to
$F = \{F_{\textit{out,1}}, F_{\textit{out,2}}, \dots, F_{\textit{add,1}}, F_{\textit{add,2}}, \dots, F_{\textit{in,1}}, F_{\textit{in,2}}, \dots \}$
, where each function is a characteristic function which maps the nodes of the graph to
![]() $1$
, if the gate type matches and
$1$
, if the gate type matches and
![]() $0$
, otherwise. Hence, if a node
$0$
, otherwise. Hence, if a node
![]() $v$
is an addition gate, we have
$v$
is an addition gate, we have
![]() $F_{\textit{add,1}}(v) = 1$
and
$F_{\textit{add,1}}(v) = 1$
and
![]() $F_{\textit{out,1}}(v) = 0$
. The number in the subscript of the functions of
$F_{\textit{out,1}}(v) = 0$
. The number in the subscript of the functions of
![]() $F$
refers to the size of the encoding of the structure, for which the functions should be used. For example,
$F$
refers to the size of the encoding of the structure, for which the functions should be used. For example,
![]() $F_{\textit{add,4}}$
is used for structures that are encoded as elements of
$F_{\textit{add,4}}$
is used for structures that are encoded as elements of
![]() $R^4$
. Now suppose we are interested in those circuits where there exists an input gate that has an addition gate as a successor. A fitting
$R^4$
. Now suppose we are interested in those circuits where there exists an input gate that has an addition gate as a successor. A fitting
![]() $\mathrm{FO}_{R}[F]$
sentence would be
$\mathrm{FO}_{R}[F]$
sentence would be
The reason why
![]() $\varphi$
works is that for each
$\varphi$
works is that for each
![]() $n \in{\mathbb{N}}$
, there exists an interpretation
$n \in{\mathbb{N}}$
, there exists an interpretation
![]() $I_n$
which maps the symbols used in
$I_n$
which maps the symbols used in
![]() $\varphi$
to functions in
$\varphi$
to functions in
![]() $F$
. This interpretation just maps
$F$
. This interpretation just maps
![]() $f_{\textit{in}}$
to
$f_{\textit{in}}$
to
![]() $F_{\textit{in,n}}$
and
$F_{\textit{in,n}}$
and
![]() $f_{\textit{add}}$
to
$f_{\textit{add}}$
to
![]() $F_{\textit{add,n}}$
.
$F_{\textit{add,n}}$
.
If we are now given a graph structure of a graph such as the first one in Figure 1, encoded as its adjacency matrix
 \begin{equation*} \begin {pmatrix} 0\;\;\;\;\; & 0\;\;\;\;\; & 0\;\;\;\;\; & 0\\[5pt] 1\;\;\;\;\; & 0\;\;\;\;\; & 0\;\;\;\;\; & 0\\[5pt] 0\;\;\;\;\; & 1\;\;\;\;\; & 0\;\;\;\;\; & 0\\[5pt] 0\;\;\;\;\; & 1\;\;\;\;\; & 0\;\;\;\;\; & 0 \end {pmatrix} \end{equation*}
\begin{equation*} \begin {pmatrix} 0\;\;\;\;\; & 0\;\;\;\;\; & 0\;\;\;\;\; & 0\\[5pt] 1\;\;\;\;\; & 0\;\;\;\;\; & 0\;\;\;\;\; & 0\\[5pt] 0\;\;\;\;\; & 1\;\;\;\;\; & 0\;\;\;\;\; & 0\\[5pt] 0\;\;\;\;\; & 1\;\;\;\;\; & 0\;\;\;\;\; & 0 \end {pmatrix} \end{equation*}
which would amount to the
![]() $R^{16}$
tuple
$R^{16}$
tuple
![]() $(0,0,0,0,1,0,0,0,0,1,0,0,0,1,0,0)$
, then our interpretation
$(0,0,0,0,1,0,0,0,0,1,0,0,0,1,0,0)$
, then our interpretation
![]() $I_{16}$
would map
$I_{16}$
would map
![]() $f_{\textit{in}}$
to
$f_{\textit{in}}$
to
![]() $F_{\textit{in,16}}$
and
$F_{\textit{in,16}}$
and
![]() $f_{\textit{add}}$
to
$f_{\textit{add}}$
to
![]() $F_{\textit{add,16}}$
. This means that the set of encodings of circuits which have gate types according to
$F_{\textit{add,16}}$
. This means that the set of encodings of circuits which have gate types according to
![]() $F$
that contain at least one input gate followed by an addition gate is definable in
$F$
that contain at least one input gate followed by an addition gate is definable in
![]() $\mathrm{FO}_{R}[F]$
. This is because
$\mathrm{FO}_{R}[F]$
. This is because
![]() $\varphi$
is a
$\varphi$
is a
![]() $\mathrm{FO}_{R}[F]$
sentence over
$\mathrm{FO}_{R}[F]$
sentence over
![]() $\sigma$
such that for each
$\sigma$
such that for each
![]() $n$
, the interpretation
$n$
, the interpretation
![]() $I_n$
interprets the symbols
$I_n$
interprets the symbols
![]() $f_{\textit{in}}$
and
$f_{\textit{in}}$
and
![]() $f_{\textit{add}}$
as elements of
$f_{\textit{add}}$
as elements of
![]() $F$
, such that for all
$F$
, such that for all
![]() $s \in R^*$
it holds that
$s \in R^*$
it holds that
![]() $s$
is an encoding of such a circuit if and only if the graph structure encoded by
$s$
is an encoding of such a circuit if and only if the graph structure encoded by
![]() $s$
satisfies
$s$
satisfies
![]() $\varphi$
.
$\varphi$
.

Figure 1. Example graphs that satisfy the imposed conditions of Example 28.
Definition 29.
We write
![]() $\mathrm{Arb}_{R}$
to denote the set of all functions
$\mathrm{Arb}_{R}$
to denote the set of all functions
![]() $f \colon R^k \to R$
, where
$f \colon R^k \to R$
, where
![]() $k \in{\mathbb{N}}$
.
$k \in{\mathbb{N}}$
.
Theorem 30.
Let R be an infinite integral domain. Then,
![]() ${\mathrm{AC}_{R}^{0}} = \mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}}$
.
${\mathrm{AC}_{R}^{0}} = \mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}}$
.
Proof.
The proof for this theorem works similarly to the construction for
![]() $\mathrm{FO}_{{\mathbb{R}}}[{\mathrm{Arb}_{{\mathbb{R}}}}] +{\textrm{SUM}_{{\mathbb{R}}}} +{\textrm{PROD}_{{\mathbb{R}}}} ={\mathrm{AC}_{\mathbb{R}}^{0}}$
(Barlag and Vollmer, Reference Barlag and Vollmer2021), since this construction does not make use of any special properties of the real numbers.
$\mathrm{FO}_{{\mathbb{R}}}[{\mathrm{Arb}_{{\mathbb{R}}}}] +{\textrm{SUM}_{{\mathbb{R}}}} +{\textrm{PROD}_{{\mathbb{R}}}} ={\mathrm{AC}_{\mathbb{R}}^{0}}$
(Barlag and Vollmer, Reference Barlag and Vollmer2021), since this construction does not make use of any special properties of the real numbers.
The basic idea for this proof is that we first show that for any
![]() $\mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}}$
sentence
$\mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}}$
sentence
![]() $\varphi$
, we can construct a circuit family which accepts its input if and only if the input encodes an
$\varphi$
, we can construct a circuit family which accepts its input if and only if the input encodes an
![]() $R$
structure that satisfies
$R$
structure that satisfies
![]() $\varphi$
. This is basically done by mimicking the behaviour of the logical operators of
$\varphi$
. This is basically done by mimicking the behaviour of the logical operators of
![]() $\varphi$
using the available gate types and evaluating the formula level by level. A universal quantifier as in
$\varphi$
using the available gate types and evaluating the formula level by level. A universal quantifier as in
![]() $\forall x \varphi (x)$
, for instance, is implemented by using a
$\forall x \varphi (x)$
, for instance, is implemented by using a
![]() $\textrm{sign}$
gate (obtained from
$\textrm{sign}$
gate (obtained from
![]() $\lt$
as per Definition 7) on top of a multiplication gate, which has the circuits for
$\lt$
as per Definition 7) on top of a multiplication gate, which has the circuits for
![]() $\varphi (a)$
for each
$\varphi (a)$
for each
![]() $a$
in the skeleton of the encoded structure as its predecessors.
$a$
in the skeleton of the encoded structure as its predecessors.
To translate the semantics of
![]() $\mathrm{FO}_{R}$
into a circuit, we can mostly use the same translations as in the proof for the real case, as for the most part only properties of integral domains are used. We need ring properties for most of these translations and in particular for universal quantifiers, we also need commutativity of multiplication and no zero dividers, hence we require integral domains.
$\mathrm{FO}_{R}$
into a circuit, we can mostly use the same translations as in the proof for the real case, as for the most part only properties of integral domains are used. We need ring properties for most of these translations and in particular for universal quantifiers, we also need commutativity of multiplication and no zero dividers, hence we require integral domains.
We do need to change the translation for existential quantifiers and
![]() $\lor$
, however. In the real case, the circuit for
$\lor$
, however. In the real case, the circuit for
![]() $\exists x \varphi (x)$
is constructed similarly to the universal case with a
$\exists x \varphi (x)$
is constructed similarly to the universal case with a
![]() $\textrm{sign}$
gate followed by an addition gate with the circuits for
$\textrm{sign}$
gate followed by an addition gate with the circuits for
![]() $\varphi (a)$
for each
$\varphi (a)$
for each
![]() $a$
in the skeleton as its predecessors. Since there are infinite integral domains with characteristic greater than
$a$
in the skeleton as its predecessors. Since there are infinite integral domains with characteristic greater than
![]() $0$
, that is where adding a positive amount of
$0$
, that is where adding a positive amount of
![]() $1$
elements can yield
$1$
elements can yield
![]() $0$
, this would not always produce the desired result. However, we can overcome this easily by translating
$0$
, this would not always produce the desired result. However, we can overcome this easily by translating
![]() $\exists x \varphi (x)$
to
$\exists x \varphi (x)$
to
![]() $\neg \forall x \neg \varphi (x)$
and
$\neg \forall x \neg \varphi (x)$
and
![]() $x \lor y$
to
$x \lor y$
to
![]() $\neg (\neg x \land \neg y)$
, as negation, universal quantifiers and
$\neg (\neg x \land \neg y)$
, as negation, universal quantifiers and
![]() $\land$
are constructible with integral domain properties.
$\land$
are constructible with integral domain properties.
For the converse inclusion, a number term
![]() $\textrm{val}_d(g)$
is created which, when given a circuit family
$\textrm{val}_d(g)$
is created which, when given a circuit family
![]() $(C_n)_{n \in{\mathbb{N}}}$
, evaluates to the value of gate
$(C_n)_{n \in{\mathbb{N}}}$
, evaluates to the value of gate
![]() $g$
if
$g$
if
![]() $g$
is on the
$g$
is on the
![]() $d$
th level of the respective circuit
$d$
th level of the respective circuit
![]() $C_n$
. For this purpose, functions encoding the structure of these circuits are given by the
$C_n$
. For this purpose, functions encoding the structure of these circuits are given by the
![]() $\mathrm{Arb}_{R}$
extension of the logic. These functions provide information about the gate type of each gate, their constant values if they are constant gates, their index if they are input gates and the edge relation of the circuit. For this construction, with integral domain properties no changes need to be made to the formula in the real setting.
$\mathrm{Arb}_{R}$
extension of the logic. These functions provide information about the gate type of each gate, their constant values if they are constant gates, their index if they are input gates and the edge relation of the circuit. For this construction, with integral domain properties no changes need to be made to the formula in the real setting.
4. Algebraic Circuits and Guarded Functional Recursion
In this section, we generalize the logical characterizations of
![]() ${\mathrm{NC}}^1$
and
${\mathrm{NC}}^1$
and
![]() ${\mathrm{AC}}^1$
by Durand et al. (Reference Durand, Haak and Vollmer2018) to the respective complexity classes over integral domains
${\mathrm{AC}}^1$
by Durand et al. (Reference Durand, Haak and Vollmer2018) to the respective complexity classes over integral domains
![]() $\mathrm{NC}_R^{1}$
and
$\mathrm{NC}_R^{1}$
and
![]() $\mathrm{AC}_{R}^{1}$
. We furthermore extend this method to capture the entire
$\mathrm{AC}_{R}^{1}$
. We furthermore extend this method to capture the entire
![]() $\mathrm{NC}_R^{}$
and
$\mathrm{NC}_R^{}$
and
![]() $\mathrm{AC}_{R}$
hierarchies.
$\mathrm{AC}_{R}$
hierarchies.
In their paper, Durand, Haak and Vollmer use what they call guarded predicative recursion to extend first-order logic in order to capture the logarithmic depth circuit complexity classes
![]() ${\mathrm{NC}}^1$
and
${\mathrm{NC}}^1$
and
![]() ${\mathrm{AC}}^1$
. This essentially amounts to a recursion operator, which halves a tuple of variables (in their numerical interpretation) which is handed down in each recursion step. This ensures that the total recursion depth is at most logarithmic. The halving of the variable tuple is performed by using the fact that addition is expressible in
${\mathrm{AC}}^1$
. This essentially amounts to a recursion operator, which halves a tuple of variables (in their numerical interpretation) which is handed down in each recursion step. This ensures that the total recursion depth is at most logarithmic. The halving of the variable tuple is performed by using the fact that addition is expressible in
![]() $\mathrm{FO}$
if
$\mathrm{FO}$
if
![]() $\mathrm{BIT}$
and
$\mathrm{BIT}$
and
![]() $\lt$
are expressible (Immerman, Reference Immerman1999) in the following way
$\lt$
are expressible (Immerman, Reference Immerman1999) in the following way
Note that we do not define the formula of the halving to be equality, since this is not possible for odd numbers. However, this is not an issue since we only want to bound the worst case recursion depth. In order to capture classes of polylogarithmic depth, we would like to find a suitable factor to replace
![]() $\frac{1}{2}$
with, so that the recursion process has polylogarithmic depth as well. As it turns out, for any
$\frac{1}{2}$
with, so that the recursion process has polylogarithmic depth as well. As it turns out, for any
![]() $i \in{\mathbb{N}}$
, we can assure a recursion depth of
$i \in{\mathbb{N}}$
, we can assure a recursion depth of
![]() ${\mathcal{O}}((\log _2 n)^i)$
by using the factor
${\mathcal{O}}((\log _2 n)^i)$
by using the factor
![]() $2^{-\frac{\log _2 n}{(\log _2 n)^i}}$
.
$2^{-\frac{\log _2 n}{(\log _2 n)^i}}$
.
Observation 31.
Any number
![]() $n \in{\mathbb{N}}$
can be multiplied by the factor
$n \in{\mathbb{N}}$
can be multiplied by the factor
![]() $2^{-\frac{\log _2 n}{(\log _2 n)^i}}$
exactly
$2^{-\frac{\log _2 n}{(\log _2 n)^i}}$
exactly
![]() $(\log _2 n)^i$
times, before reaching
$(\log _2 n)^i$
times, before reaching
![]() $1$
.
$1$
.
A more general version of this observation can be found in Lemma 58 in the appendix. Unfortunately, while it is simple to divide by
![]() $2$
when the
$2$
when the
![]() $\mathrm{BIT}$
predicate is available, it is not at all clear if multiplying by a factor such as
$\mathrm{BIT}$
predicate is available, it is not at all clear if multiplying by a factor such as
![]() $2^{-\frac{\log _2 n}{(\log _2 n)^i}}$
can be done in first-order logic.
$2^{-\frac{\log _2 n}{(\log _2 n)^i}}$
can be done in first-order logic.
We can, however, make use of the ability to divide by
![]() $2$
in order to achieve polylogarithmic recursion depth, by instead of dividing a number, essentially dividing the digits of a base
$2$
in order to achieve polylogarithmic recursion depth, by instead of dividing a number, essentially dividing the digits of a base
![]() $n$
number individually and carrying over once
$n$
number individually and carrying over once
![]() $0$
is reached.
$0$
is reached.
Let us take for example the base
![]() $5$
number
$5$
number
![]() $444$
. The previously mentioned process is illustrated in Table 1. The table is supposed to be read from top to bottom and then from left to right.
$444$
. The previously mentioned process is illustrated in Table 1. The table is supposed to be read from top to bottom and then from left to right.
We divide the digits of
![]() $444$
from the least to most the significant digit until
$444$
from the least to most the significant digit until
![]() $0$
is reached. So, the first step is dividing the rightmost digit of
$0$
is reached. So, the first step is dividing the rightmost digit of
![]() $444$
by
$444$
by
![]() $2$
, getting from
$2$
, getting from
![]() $444$
to
$444$
to
![]() $442$
. After two more divisions of that kind, we reach
$442$
. After two more divisions of that kind, we reach
![]() $0$
and in the subsequent step we reset the rightmost digit and divide the second digit once. This works in a similar way to counting down, where instead of taking away
$0$
and in the subsequent step we reset the rightmost digit and divide the second digit once. This works in a similar way to counting down, where instead of taking away
![]() $1$
in each step, we divide by
$1$
in each step, we divide by
![]() $2$
and carry over in an analogous way. Notably, reaching
$2$
and carry over in an analogous way. Notably, reaching
![]() $000$
from
$000$
from
![]() $444$
takes
$444$
takes
![]() $63 = (\lfloor \log _2 5 \rfloor + 2)^3 - 1$
steps. This is no coincidence: It can easily be shown that for any base
$63 = (\lfloor \log _2 5 \rfloor + 2)^3 - 1$
steps. This is no coincidence: It can easily be shown that for any base
![]() $n$
number of
$n$
number of
![]() $i$
digits, this sort of process reaches the smallest possible element after less than
$i$
digits, this sort of process reaches the smallest possible element after less than
![]() $(\lfloor \log _2 n-1 \rfloor + 2)^i-1$
steps.
$(\lfloor \log _2 n-1 \rfloor + 2)^i-1$
steps.
Since we wish to logically characterize languages decided by circuit families, it is useful to briefly talk about representation of numbers. In descriptive complexity, tuples of elements from a finite, ordered domain
![]() $A$
are often associated with numbers. This is frequently done by interpreting the tuple as a base
$A$
are often associated with numbers. This is frequently done by interpreting the tuple as a base
![]() $\lvert A\rvert$
number with each element of the tuple representing its position in the ordering of
$\lvert A\rvert$
number with each element of the tuple representing its position in the ordering of
![]() $A$
.
$A$
.
Example 32.
For example, let
![]() $D = \{a, b, c, d\}$
be ordered such that
$D = \{a, b, c, d\}$
be ordered such that
![]() $a \lt b \lt c \lt d$
. Then, the tuple
$a \lt b \lt c \lt d$
. Then, the tuple
![]() $(b,d,c,a) = (1,3,2,0)$
would be interpreted as the base
$(b,d,c,a) = (1,3,2,0)$
would be interpreted as the base
![]() $4$
number
$4$
number
![]() $1320$
, which would correspond to
$1320$
, which would correspond to
![]() $60$
in decimal.
$60$
in decimal.
Whenever we talk about the numerical interpretation of a tuple, we refer to this sort of interpretation. With this interpretation in mind, we now want to define a
![]() $\mathrm{BIT}$
predicate, which is needed to express divisions in our logic. In our definition, we assume that the most significant bit of
$\mathrm{BIT}$
predicate, which is needed to express divisions in our logic. In our definition, we assume that the most significant bit of
![]() $j$
’s binary representation is the bit at index
$j$
’s binary representation is the bit at index
![]() $1$
:
$1$
:
Table 1. Illustration of digit-wise division until
![]() $0$
of the base
$0$
of the base
![]() $5$
number
$5$
number
![]() $444$
which takes
$444$
which takes
![]() $63 = (\lfloor \log _2 5 \rfloor + 2)^3 - 1$
steps
$63 = (\lfloor \log _2 5 \rfloor + 2)^3 - 1$
steps

Definition 33.
For any ranked structure with universe
![]() $D$
, let the relation
$D$
, let the relation
![]() ${\mathrm{BIT}}^2 \subseteq D^* \times D^*$
be defined as follows:
${\mathrm{BIT}}^2 \subseteq D^* \times D^*$
be defined as follows:
 \begin{multline*}{\mathrm{BIT}} \;:=\; \{(i, j) \mid \textit{ when } i \textit{ and } j\; \textit{are taken as their numerical interpretations, the } \\[5pt] i\textit{th bit of the binary representation of } j\; \textit{is } 1, i, j \in D^*\} \end{multline*}
\begin{multline*}{\mathrm{BIT}} \;:=\; \{(i, j) \mid \textit{ when } i \textit{ and } j\; \textit{are taken as their numerical interpretations, the } \\[5pt] i\textit{th bit of the binary representation of } j\; \textit{is } 1, i, j \in D^*\} \end{multline*}
Note that the case
![]() $D^* = \mathbb{N}$
yields the classical
$D^* = \mathbb{N}$
yields the classical
![]() $\mathrm{BIT}$
predicate. With the
$\mathrm{BIT}$
predicate. With the
![]() $\mathrm{BIT}$
predicate and an order relation, we are now able to express division by
$\mathrm{BIT}$
predicate and an order relation, we are now able to express division by
![]() $2$
in first-order logic. We use the fact that whenever
$2$
in first-order logic. We use the fact that whenever
![]() $\mathrm{BIT}$
and an order are available, we can express multiplication and addition of numerical interpretations of tuples (Immerman, Reference Immerman1999). This result was shown for plain first-order logic, and since our two-sorted first-order logic
$\mathrm{BIT}$
and an order are available, we can express multiplication and addition of numerical interpretations of tuples (Immerman, Reference Immerman1999). This result was shown for plain first-order logic, and since our two-sorted first-order logic
![]() $\mathrm{FO}_{R}$
is equivalent to first-order logic if the secondary component is ignored, we can apply it here as well.
$\mathrm{FO}_{R}$
is equivalent to first-order logic if the secondary component is ignored, we can apply it here as well.
We express division by
![]() $2$
as follows:
$2$
as follows:
Note again that since the numerical interpretations of tuples are natural numbers, expressing
![]() ${\overline{x}} \leq{\overline{y}}/ 2$
is really as good as we can do, since
${\overline{x}} \leq{\overline{y}}/ 2$
is really as good as we can do, since
![]() ${\overline{x}} ={\overline{y}}/ 2$
would not work for odd numbers.
${\overline{x}} ={\overline{y}}/ 2$
would not work for odd numbers.
Next, we will turn to defining the recursion operator which we have alluded to in the beginning of this section. First, we need a little bit of additional notation, that is relativized aggregators. A relativization of an aggregator is a formula restricting which elements are considered for the aggregator.
Notation 34.
For a number term
![]() $t$
and an
$t$
and an
![]() $\mathrm{FO}_{R}$
formula
$\mathrm{FO}_{R}$
formula
![]() $\varphi$
, we write
$\varphi$
, we write
as a shorthand for
Analogously, we write
for
and
as a shorthand for
In all these cases, we say that the term
![]() $t({\overline{x}})$
is in the scope of the respective aggregator. For example in the first case,
$t({\overline{x}})$
is in the scope of the respective aggregator. For example in the first case,
![]() $t({\overline{x}})$
is in the scope of the relativized aggregator
$t({\overline{x}})$
is in the scope of the relativized aggregator
![]() $\textbf{max}_{{\overline{x}}}.(\varphi ({\overline{x}}))$
.
$\textbf{max}_{{\overline{x}}}.(\varphi ({\overline{x}}))$
.
We now define the
![]() ${\mathrm{GFR}_{R}^i}$
operator and logics extended by
${\mathrm{GFR}_{R}^i}$
operator and logics extended by
![]() ${\mathrm{GFR}_{R}^i}$
of the form
${\mathrm{GFR}_{R}^i}$
of the form
![]() $\mathcal{L}+{{\mathrm{GFR}_{R}^i}}$
. The idea is to mimic the behaviour demonstrated in Table 1.
$\mathcal{L}+{{\mathrm{GFR}_{R}^i}}$
. The idea is to mimic the behaviour demonstrated in Table 1.
Definition 35 (
![]() ${\mathrm{GFR}_{R}^i}$
). Let
${\mathrm{GFR}_{R}^i}$
). Let
![]() $F$
be a set of functions such that
$F$
be a set of functions such that
![]() $\mathrm{BIT}$
is definable in
$\mathrm{BIT}$
is definable in
![]() $\mathrm{FO}_{R}[F]$
and let
$\mathrm{FO}_{R}[F]$
and let
![]() $\mathcal{L}$
be
$\mathcal{L}$
be
![]() $\mathrm{FO}_{R}[F]$
or a logic obtained by extending
$\mathrm{FO}_{R}[F]$
or a logic obtained by extending
![]() $\mathrm{FO}_{R}[F]$
with some construction rules (such as the sum or the product rule as per Definition 24).
$\mathrm{FO}_{R}[F]$
with some construction rules (such as the sum or the product rule as per Definition 24).
For
![]() $i \geq 0$
, the set of
$i \geq 0$
, the set of
![]() $\mathcal{L}+{{\mathrm{GFR}_{R}^i}}$
formulae over
$\mathcal{L}+{{\mathrm{GFR}_{R}^i}}$
formulae over
![]() $\sigma = (L_s, L_f, L_a)$
is the set of formulae by the grammar for
$\sigma = (L_s, L_f, L_a)$
is the set of formulae by the grammar for
![]() $\mathcal{L}$
over
$\mathcal{L}$
over
![]() $\sigma$
extended by the rule
$\sigma$
extended by the rule
where
![]() $\psi$
is an
$\psi$
is an
![]() $\mathcal{L}$
formula,
$\mathcal{L}$
formula,
![]() $f$
is a function symbol, and
$f$
is a function symbol, and
![]() $t$
is an
$t$
is an
![]() $\mathcal{L}$
number term with free variables
$\mathcal{L}$
number term with free variables
![]() ${\overline{x}},{\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}}$
such that
${\overline{x}},{\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}}$
such that
-
1. all
 $\overline{y_j}$
for
$\overline{y_j}$
for
 $1 \leq j \leq i$
contain the same (positive) number of variables,
$1 \leq j \leq i$
contain the same (positive) number of variables,
-
2.
 $f$
only occurs in the form
$f$
only occurs in the form
 $f({\overline{a}},{\overline{z_1}}, \dots,{\overline{z_i}},{\overline{z_{i+1}}})$
, where
$f({\overline{a}},{\overline{z_1}}, \dots,{\overline{z_i}},{\overline{z_{i+1}}})$
, where
 ${\overline{z_1}}, \dots,{\overline{z_i}},{\overline{z_{i+1}}}$
are in the scope of a guarded aggregation
with
${\overline{z_1}}, \dots,{\overline{z_i}},{\overline{z_{i+1}}}$
are in the scope of a guarded aggregation
with \begin{equation*} A_{{\overline {z_1}}, \dots, {\overline {z_i}}, {\overline {z_{i+1}}}}.\left (\bigvee \limits _{j = 1}^i \left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1} {\overline {z_k}} \leq {\overline {y_k}} \right ) \land \xi ({\overline {y_1}}, \dots, {\overline {y_i}}, {\overline {y_{i+1}}}, {\overline {z_1}}, \dots, {\overline {z_i}}, {\overline {z_{i+1}}})\right ) \end{equation*}
\begin{equation*} A_{{\overline {z_1}}, \dots, {\overline {z_i}}, {\overline {z_{i+1}}}}.\left (\bigvee \limits _{j = 1}^i \left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1} {\overline {z_k}} \leq {\overline {y_k}} \right ) \land \xi ({\overline {y_1}}, \dots, {\overline {y_i}}, {\overline {y_{i+1}}}, {\overline {z_1}}, \dots, {\overline {z_i}}, {\overline {z_{i+1}}})\right ) \end{equation*}
 $A \in \{\textbf{max}, \textbf{sum}, \textbf{prod}\}$
,
$A \in \{\textbf{max}, \textbf{sum}, \textbf{prod}\}$
,
 $\xi \in \mathcal{L}$
and
$\xi \in \mathcal{L}$
and
 $\xi$
not containing any symbols of
$\xi$
not containing any symbols of
 $L_s$
or
$L_s$
or
 $L_f$
and
$L_f$
and
-
3.
 $f$
never occurs in the scope of any aggregation (or quantification) not guarded in this way.
$f$
never occurs in the scope of any aggregation (or quantification) not guarded in this way.
The function symbol
![]() $f$
is considered bound in
$f$
is considered bound in
The semantics for the
![]() ${\mathrm{GFR}_{R}}^i$
operator are defined as follows: Let
${\mathrm{GFR}_{R}}^i$
operator are defined as follows: Let
![]() $\varphi$
be an
$\varphi$
be an
![]() $\mathcal{L} +{{\mathrm{GFR}_{R}^i}}$
formula over
$\mathcal{L} +{{\mathrm{GFR}_{R}^i}}$
formula over
![]() $\sigma$
with the single
$\sigma$
with the single
![]() ${\mathrm{GFR}_{R}^i}$
occurrence
${\mathrm{GFR}_{R}^i}$
occurrence
and let
![]() ${\mathcal{D}} \in{{STRUC}_{R}}(\sigma )$
. Then, the operator which is applied to the formula
${\mathcal{D}} \in{{STRUC}_{R}}(\sigma )$
. Then, the operator which is applied to the formula
![]() $\psi$
, namely
$\psi$
, namely
![]() $[f({\overline{x}},{\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}}) \equiv t({\overline{x}},{\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}},f)]$
, defines the interpretation of
$[f({\overline{x}},{\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}}) \equiv t({\overline{x}},{\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}},f)]$
, defines the interpretation of
![]() $f$
in
$f$
in
![]() $\psi$
in the following way: For all tuples
$\psi$
in the following way: For all tuples
![]() ${\overline{a}},{\overline{b_1}}, \dots,{\overline{b_i}},{\overline{b_{i+1}}}$
of elements of the universe
${\overline{a}},{\overline{b_1}}, \dots,{\overline{b_i}},{\overline{b_{i+1}}}$
of elements of the universe
![]() $D$
of
$D$
of
![]() $\mathcal{D}$
with the same arities as
$\mathcal{D}$
with the same arities as
![]() ${\overline{x}},{\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}}$
, respectively,
${\overline{x}},{\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}}$
, respectively,
This means that the formula
![]() $[f({\overline{x}},{\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}}) \equiv t({\overline{x}},{\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}},f)] \psi ({\overline{c}}, f)$
holds for a tuple
$[f({\overline{x}},{\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}}) \equiv t({\overline{x}},{\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}},f)] \psi ({\overline{c}}, f)$
holds for a tuple
![]() ${\overline{c}} \in D^{\lvert{\overline{c}}\rvert }$
with the same arity as
${\overline{c}} \in D^{\lvert{\overline{c}}\rvert }$
with the same arity as
![]() $\overline{z}$
if and only if
$\overline{z}$
if and only if
![]() ${\mathcal{D}} \models \psi ({\overline{c}}, f_I)$
where
${\mathcal{D}} \models \psi ({\overline{c}}, f_I)$
where
![]() $f_I$
is the interpretation of
$f_I$
is the interpretation of
![]() $f$
as defined by the
$f$
as defined by the
![]() ${\mathrm{GFR}_{R}}^i$
operator. Semantics of formulae with several
${\mathrm{GFR}_{R}}^i$
operator. Semantics of formulae with several
![]() ${\mathrm{GFR}_{R}^i}$
operators are defined analogously.
${\mathrm{GFR}_{R}^i}$
operators are defined analogously.
Note that the
![]() $(i+1)$
th tuple does not get restricted by the guarded aggregation.
$(i+1)$
th tuple does not get restricted by the guarded aggregation.
An example is in order. In the following scenario, we would like to illustrate the use of the
![]() ${\mathrm{GFR}_{R}^i}$
operator. A more thorough examination of its recursion depth will follow in Lemma 37.
${\mathrm{GFR}_{R}^i}$
operator. A more thorough examination of its recursion depth will follow in Lemma 37.
Example 36.
Let us consider the scenario where we are given a graph
![]() $G$
, two nodes
$G$
, two nodes
![]() $s$
and
$s$
and
![]() $t$
of
$t$
of
![]() $G$
, and we wish to express that there is a path from
$G$
, and we wish to express that there is a path from
![]() $s$
to
$s$
to
![]() $t$
in
$t$
in
![]() $G$
. Let the graphs we consider be encoded by a structure
$G$
. Let the graphs we consider be encoded by a structure
![]() $\mathcal{D}$
, such that each node can be uniquely identified with a quadruple of values of the universe of
$\mathcal{D}$
, such that each node can be uniquely identified with a quadruple of values of the universe of
![]() $\mathcal{D}$
. The signature we will be using is
$\mathcal{D}$
. The signature we will be using is
![]() $\sigma = (\{\}, \{ f_E^8, f_{\textit{start}}^4, f_{\textit{target}}^4 \}, \{\})$
, where
$\sigma = (\{\}, \{ f_E^8, f_{\textit{start}}^4, f_{\textit{target}}^4 \}, \{\})$
, where
![]() $f_{\textit{start}}(x_1, x_2, x_3, x_4) = 1$
if
$f_{\textit{start}}(x_1, x_2, x_3, x_4) = 1$
if
![]() $(x_1, x_2, x_3, x_4)$
encodes the starting node,
$(x_1, x_2, x_3, x_4)$
encodes the starting node,
![]() $f_{\textit{target}}(x_1, x_2, x_3, x_4) = 1$
if
$f_{\textit{target}}(x_1, x_2, x_3, x_4) = 1$
if
![]() $(x_1, x_2, x_3, x_4)$
encodes the target node and
$(x_1, x_2, x_3, x_4)$
encodes the target node and
![]() $f_E(x_1, \dots, x_8) = 1$
if there is an edge in
$f_E(x_1, \dots, x_8) = 1$
if there is an edge in
![]() $G$
from the node encoded by
$G$
from the node encoded by
![]() $(x_1, x_2, x_3, x_4)$
to the node encoded by
$(x_1, x_2, x_3, x_4)$
to the node encoded by
![]() $(x_5, x_6, x_7, x_8)$
. This means that, if
$(x_5, x_6, x_7, x_8)$
. This means that, if
![]() ${\mathcal{D}} = ({\mathcal{A}}, F)$
, then the graph it encodes has size
${\mathcal{D}} = ({\mathcal{A}}, F)$
, then the graph it encodes has size
![]() $\lvert A \rvert ^4$
.
$\lvert A \rvert ^4$
.
If we are interested in finding out whether there exists a path of length bounded by
![]() $(\log n)^4$
from the start node to the target node, we can use the following
$(\log n)^4$
from the start node to the target node, we can use the following
![]() $\mathrm{FO}_{R} +{\textrm{SUM}_{{{R}}}} +{\textrm{PROD}_{{{R}}}} +{\mathrm{GFR}_{R}^4}$
sentence. (A more exact treatment of the recursion depth of the
$\mathrm{FO}_{R} +{\textrm{SUM}_{{{R}}}} +{\textrm{PROD}_{{{R}}}} +{\mathrm{GFR}_{R}^4}$
sentence. (A more exact treatment of the recursion depth of the
![]() ${\mathrm{GFR}_{R}^i}$
operator will follow this example in Lemma 37.)
${\mathrm{GFR}_{R}^i}$
operator will follow this example in Lemma 37.)
 \begin{align*} \varphi = [f&(y_1, \dots, y_8) \equiv t(y_1, \dots, y_8, f)] \\[5pt] &\ \exists x_1, x_2, x_3, x_4\, f_{\textit{start}}(x_1, x_2, x_3, x_4) = 1\ \land \\[5pt] &\ \exists m\,f(m, m, m, m, x_1, x_2, x_3, x_4) \geq 1 \end{align*}
\begin{align*} \varphi = [f&(y_1, \dots, y_8) \equiv t(y_1, \dots, y_8, f)] \\[5pt] &\ \exists x_1, x_2, x_3, x_4\, f_{\textit{start}}(x_1, x_2, x_3, x_4) = 1\ \land \\[5pt] &\ \exists m\,f(m, m, m, m, x_1, x_2, x_3, x_4) \geq 1 \end{align*}
where
 \begin{align*} t(y_1, \dots, y_8, f) = &\ f_{\textit{target}}(y_5, y_6, y_7, y_8)\ +\\[5pt] &\textbf{sum}_{{{z_1}, \dots,{z_8}}}.\left (\bigvee \limits _{j = 1}^4 \left ({z_j} \leq{y_j}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{z_k} \leq{y_k} \right )\right ) \\[5pt] &(f_E(y_5, y_6, y_7, y_8, z_5, z_6, z_7, z_8) \times f(z_1, \dots, z_8)) \end{align*}
\begin{align*} t(y_1, \dots, y_8, f) = &\ f_{\textit{target}}(y_5, y_6, y_7, y_8)\ +\\[5pt] &\textbf{sum}_{{{z_1}, \dots,{z_8}}}.\left (\bigvee \limits _{j = 1}^4 \left ({z_j} \leq{y_j}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{z_k} \leq{y_k} \right )\right ) \\[5pt] &(f_E(y_5, y_6, y_7, y_8, z_5, z_6, z_7, z_8) \times f(z_1, \dots, z_8)) \end{align*}
In
![]() $\varphi$
, we first identify the starting node and then dive into the recursion. Note first that the values
$\varphi$
, we first identify the starting node and then dive into the recursion. Note first that the values
![]() $y_5, y_6, y_7, y_8$
essentially take the place of the
$y_5, y_6, y_7, y_8$
essentially take the place of the
![]() $\overline{y_{i+1}}$
in Definition 35
. Note also that the values
$\overline{y_{i+1}}$
in Definition 35
. Note also that the values
![]() $y_1, y_2, y_3, y_4$
take the place of the
$y_1, y_2, y_3, y_4$
take the place of the
![]() ${\overline{y_1}} \dots{\overline{y_i}}$
in the aforementioned definition and are in this example essentially only used as a counter mimicking the behaviour shown in Table
1 to ensure the correct recursion depth. The point of
${\overline{y_1}} \dots{\overline{y_i}}$
in the aforementioned definition and are in this example essentially only used as a counter mimicking the behaviour shown in Table
1 to ensure the correct recursion depth. The point of
![]() $m$
in
$m$
in
![]() $\varphi$
is thus merely to essentially start this counter which will then become decreased in the recursion. We could also impose that
$\varphi$
is thus merely to essentially start this counter which will then become decreased in the recursion. We could also impose that
![]() $m$
be the maximum value of the universe of
$m$
be the maximum value of the universe of
![]() $\mathcal{D}$
, but we do not need to, as if any such
$\mathcal{D}$
, but we do not need to, as if any such
![]() $m$
exists, our requirement that a path with length bounded by
$m$
exists, our requirement that a path with length bounded by
![]() ${\mathcal{O}}((\log n)^4)$
is satisfied.
${\mathcal{O}}((\log n)^4)$
is satisfied.
In
![]() $t$
, we first check whether we have already reached the target node. Afterwards, we use a guarded sum-aggregator to decrease the counter stored in
$t$
, we first check whether we have already reached the target node. Afterwards, we use a guarded sum-aggregator to decrease the counter stored in
![]() $z_1, z_2, z_3, z_4$
, iterate over all nodes
$z_1, z_2, z_3, z_4$
, iterate over all nodes
![]() $z_5, z_6, z_7, z_8$
and jump into the recursion, zeroing out all non-neighbouring nodes of the current node.
$z_5, z_6, z_7, z_8$
and jump into the recursion, zeroing out all non-neighbouring nodes of the current node.
In total,
![]() $\varphi$
essentially describes an algorithm which traverses the given graph in a depth-first manner and which terminates after polylogarithmically many steps because of the guarded aggregations. The exact recursion depth is not obvious and will be investigated further in the following.
$\varphi$
essentially describes an algorithm which traverses the given graph in a depth-first manner and which terminates after polylogarithmically many steps because of the guarded aggregations. The exact recursion depth is not obvious and will be investigated further in the following.
Having introduced the
![]() ${\mathrm{GFR}_{R}^i}$
operator, it remains to be shown that it indeed ensures polylogarithmic recursion depth in the way that we want it to.
${\mathrm{GFR}_{R}^i}$
operator, it remains to be shown that it indeed ensures polylogarithmic recursion depth in the way that we want it to.
Lemma 37.
Let
![]() ${\mathcal{D}} \in{{STRUC}_{R}}(\sigma )$
and let
${\mathcal{D}} \in{{STRUC}_{R}}(\sigma )$
and let
![]() $\varphi$
be a formula containing a
$\varphi$
be a formula containing a
![]() ${\mathrm{GFR}_{R}^i}$
operator. Then, the recursion depth of the
${\mathrm{GFR}_{R}^i}$
operator. Then, the recursion depth of the
![]() ${\mathrm{GFR}_{R}^i}$
operator is bounded by
${\mathrm{GFR}_{R}^i}$
operator is bounded by
![]() ${\mathcal{O}}((\log _2 n)^i)$
, where
${\mathcal{O}}((\log _2 n)^i)$
, where
![]() $n$
is the size of the universe of
$n$
is the size of the universe of
![]() $\mathcal{D}$
.
$\mathcal{D}$
.
Proof.
Let
![]() $n$
be the size of the universe of the structure under which the
$n$
be the size of the universe of the structure under which the
![]() ${\mathrm{GFR}_{R}^i}$
operator is interpreted. The bound for the recursion depth of the
${\mathrm{GFR}_{R}^i}$
operator is interpreted. The bound for the recursion depth of the
![]() ${\mathrm{GFR}_{R}^i}$
operator stems from the relativization which guards the aggregated variables. Let
${\mathrm{GFR}_{R}^i}$
operator stems from the relativization which guards the aggregated variables. Let
![]() $f({\overline{x}},{\overline{z_1}}, \dots,{\overline{z_i}},{\overline{z_{i+1}}})$
be an occurrence of a
$f({\overline{x}},{\overline{z_1}}, \dots,{\overline{z_i}},{\overline{z_{i+1}}})$
be an occurrence of a
![]() ${\mathrm{GPR}}^i$
operator. Then, the variables in
${\mathrm{GPR}}^i$
operator. Then, the variables in
![]() ${\overline{z_1}}, \dots,{\overline{z_i}},{\overline{z_{i+1}}}$
are in the scope of a guarded aggregation of the form
${\overline{z_1}}, \dots,{\overline{z_i}},{\overline{z_{i+1}}}$
are in the scope of a guarded aggregation of the form
 \begin{equation*} A_{{\overline {z_1}}, \dots, {\overline {z_i}}, {\overline {z_{i+1}}}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1} {\overline {z_k}} \leq {\overline {y_k}} \right ) \land \xi ({\overline {y_1}}, \dots, {\overline {y_i}}, {\overline {y_{i+1}}}, {\overline {z_1}}, \dots, {\overline {z_i}}, {\overline {z_{i+1}}})\right ) \end{equation*}
\begin{equation*} A_{{\overline {z_1}}, \dots, {\overline {z_i}}, {\overline {z_{i+1}}}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1} {\overline {z_k}} \leq {\overline {y_k}} \right ) \land \xi ({\overline {y_1}}, \dots, {\overline {y_i}}, {\overline {y_{i+1}}}, {\overline {z_1}}, \dots, {\overline {z_i}}, {\overline {z_{i+1}}})\right ) \end{equation*}
as per Definition 35.
Let
![]() $z_j$
be the numerical interpretation of
$z_j$
be the numerical interpretation of
![]() $\overline{z_j}$
for all
$\overline{z_j}$
for all
![]() $1 \leq j \leq i$
. We interpret the tuple
$1 \leq j \leq i$
. We interpret the tuple
![]() ${\overline{z_1}}, \dots,{\overline{z_i}}$
as a natural number
${\overline{z_1}}, \dots,{\overline{z_i}}$
as a natural number
![]() $z$
of base
$z$
of base
![]() $n$
where the
$n$
where the
![]() $j$
th digit of
$j$
th digit of
![]() $z$
is
$z$
is
![]() $z_j$
.
$z_j$
.
First, observe that in this interpretation, the relativization of the variables used in the recursive call ensures that
![]() $z$
strictly decreases in each step. The big disjunction
$z$
strictly decreases in each step. The big disjunction
 $\bigvee \limits _{j = 1}^i \left ({\overline{z_j}} \leq{\overline{y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline{z_k}} \leq{\overline{y_k}} \right )$
makes sure that there is an index
$\bigvee \limits _{j = 1}^i \left ({\overline{z_j}} \leq{\overline{y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline{z_k}} \leq{\overline{y_k}} \right )$
makes sure that there is an index
![]() $j$
, such that
$j$
, such that
![]() ${\overline{z_j}} \leq{\overline{y_j}}/ 2$
, which means that the numerical interpretation of
${\overline{z_j}} \leq{\overline{y_j}}/ 2$
, which means that the numerical interpretation of
![]() $\overline{z_j}$
is at most half of the numerical interpretation of
$\overline{z_j}$
is at most half of the numerical interpretation of
![]() $\overline{y_j}$
. It also ensures that all tuples with smaller indices
$\overline{y_j}$
. It also ensures that all tuples with smaller indices
![]() $\overline{z_k}$
(i.e., the more significant tuples in the interpretation of
$\overline{z_k}$
(i.e., the more significant tuples in the interpretation of
![]() ${\overline{z_1}}, \dots,{\overline{z_i}}$
as a base
${\overline{z_1}}, \dots,{\overline{z_i}}$
as a base
![]() $n$
number) do not increase.
$n$
number) do not increase.
Since each of the tuples
![]() $\overline{z_j}$
(in their numerical interpretation) can only get halved at most
$\overline{z_j}$
(in their numerical interpretation) can only get halved at most
![]() $\lfloor \log _2 n \rfloor +1$
times before reaching
$\lfloor \log _2 n \rfloor +1$
times before reaching
![]() $0$
, it takes at most
$0$
, it takes at most
![]() $\lfloor \log _2 n \rfloor + 2$
recursion steps until a tuple other than the
$\lfloor \log _2 n \rfloor + 2$
recursion steps until a tuple other than the
![]() $i$
th has been halved, in the worst case that is the
$i$
th has been halved, in the worst case that is the
![]() $(i-1)$
th tuple. This process can then be repeated at most
$(i-1)$
th tuple. This process can then be repeated at most
![]() $\lfloor \log _2 n \rfloor + 1$
times, before the tuple at the next lower index gets halved. In total, in the worst case, it takes
$\lfloor \log _2 n \rfloor + 1$
times, before the tuple at the next lower index gets halved. In total, in the worst case, it takes
![]() $(\lfloor \log _2 n \rfloor + 2)^{j}$
recursion steps until the
$(\lfloor \log _2 n \rfloor + 2)^{j}$
recursion steps until the
![]() $i-j$
th tuple gets halved in this process.
$i-j$
th tuple gets halved in this process.
This means that after
![]() $(\lfloor \log _2 n \rfloor + 2)^{i} - 1$
recursion steps, each tuple has reached
$(\lfloor \log _2 n \rfloor + 2)^{i} - 1$
recursion steps, each tuple has reached
![]() $0$
. Therefore, the total maximum recursion depth is
$0$
. Therefore, the total maximum recursion depth is
![]() $(\lfloor \log _2 n \rfloor + 2)^{i} - 1 \in{\mathcal{O}}((\log _2 n)^i)$
.
$(\lfloor \log _2 n \rfloor + 2)^{i} - 1 \in{\mathcal{O}}((\log _2 n)^i)$
.
This process can be thought of as counting down a base
![]() $\log _2 n$
number. The idea for it has already been visualized in Table 1. It is also explicitly illustrated in Tables 3 and 4 in the appendix, for a sequence which we will define shortly in Definition 42 to make use of exactly this kind of process.
$\log _2 n$
number. The idea for it has already been visualized in Table 1. It is also explicitly illustrated in Tables 3 and 4 in the appendix, for a sequence which we will define shortly in Definition 42 to make use of exactly this kind of process.
Since our final goal is to characterize both
![]() $\mathrm{AC}_{R}^{i}$
and
$\mathrm{AC}_{R}^{i}$
and
![]() $\mathrm{NC}_R^{i}$
, we need to also define aggregators which model the properties of
$\mathrm{NC}_R^{i}$
, we need to also define aggregators which model the properties of
![]() $\mathrm{NC}_R^{}$
circuits. For this purpose, we introduce bounded aggregators, that is relativized aggregators where we only consider the two elements of maximal size meeting the condition in the relativization.
$\mathrm{NC}_R^{}$
circuits. For this purpose, we introduce bounded aggregators, that is relativized aggregators where we only consider the two elements of maximal size meeting the condition in the relativization.
Definition 38.
We define the bounded aggregators
![]() $\textbf{sum}_{{\overline{x}},\mathrm{bound}}$
and
$\textbf{sum}_{{\overline{x}},\mathrm{bound}}$
and
![]() $\textbf{prod}_{{\overline{x}},\mathrm{bound}}$
. They are used in the same way as the aggregators defined earlier in Definition 24
. The semantics are defined as follows:
$\textbf{prod}_{{\overline{x}},\mathrm{bound}}$
. They are used in the same way as the aggregators defined earlier in Definition 24
. The semantics are defined as follows:
 \begin{multline*}{\textbf{sum}_{{\overline{x}},\mathrm{bound}}}.(\varphi ({\overline{x}}))t({\overline{x}},{\overline{w}}) \equiv \\[5pt] \textbf{sum}_{{\overline{x}}}.(\varphi ({\overline{x}}) \land \forall{\overline{y}}\; \forall{\overline{z}} (({\overline{y}} \neq{\overline{z}} \land{\overline{x}} \lt{\overline{y}} \land{\overline{x}} \lt{\overline{z}}) \to (\neg \varphi ({\overline{y}}) \lor \neg \varphi ({\overline{z}}))))t({\overline{x}},{\overline{w}}) \end{multline*}
\begin{multline*}{\textbf{sum}_{{\overline{x}},\mathrm{bound}}}.(\varphi ({\overline{x}}))t({\overline{x}},{\overline{w}}) \equiv \\[5pt] \textbf{sum}_{{\overline{x}}}.(\varphi ({\overline{x}}) \land \forall{\overline{y}}\; \forall{\overline{z}} (({\overline{y}} \neq{\overline{z}} \land{\overline{x}} \lt{\overline{y}} \land{\overline{x}} \lt{\overline{z}}) \to (\neg \varphi ({\overline{y}}) \lor \neg \varphi ({\overline{z}}))))t({\overline{x}},{\overline{w}}) \end{multline*}
The bounded aggregators
![]() $\textbf{prod}_{{\overline{x}},\mathrm{bound}}$
and
$\textbf{prod}_{{\overline{x}},\mathrm{bound}}$
and
![]() $\textbf{max}_{{\overline{x}}, \mathrm{bound}}$
are defined analogously.
$\textbf{max}_{{\overline{x}}, \mathrm{bound}}$
are defined analogously.
With this bounded aggregation, we can now define a slightly weaker version of the guarded functional recursion from Definition 35, which we call bounded guarded functional recursion
![]() ${\mathrm{GFR}_{R, \mathrm{bound}}^i}$
. This allows us then to define logics of the form
${\mathrm{GFR}_{R, \mathrm{bound}}^i}$
. This allows us then to define logics of the form
![]() $\mathrm{FO}_{R}[F] +{{\mathrm{GFR}_{R}^i}}$
or
$\mathrm{FO}_{R}[F] +{{\mathrm{GFR}_{R}^i}}$
or
![]() $\mathrm{FO}_{R}[F] +{{\mathrm{GFR}_{R, \mathrm{bound}}^i}}$
.
$\mathrm{FO}_{R}[F] +{{\mathrm{GFR}_{R, \mathrm{bound}}^i}}$
.
Definition 39 (
![]() ${\mathrm{GFR}_{R, \mathrm{bound}}^i}$
). A formula is in
${\mathrm{GFR}_{R, \mathrm{bound}}^i}$
). A formula is in
![]() $\mathrm{FO}_{R}[F]+{{\mathrm{GFR}_{R, \mathrm{bound}}^i}}$
if the same conditions as in Definition 35 are met, but instead of a guarded aggregation in (2), we require a bounded guarded aggregation.
$\mathrm{FO}_{R}[F]+{{\mathrm{GFR}_{R, \mathrm{bound}}^i}}$
if the same conditions as in Definition 35 are met, but instead of a guarded aggregation in (2), we require a bounded guarded aggregation.
Our goal in the following is to characterize the
![]() $\mathrm{AC}_{{R}}$
and
$\mathrm{AC}_{{R}}$
and
![]() $\mathrm{NC}_R^{}$
hierarchies using first-order logic and guarded functional recursion. For that purpose, we now define a sequence which we will later use as part of the numbers of our gates in order to encode the gates’ depth into their numbers. The idea behind the construction of this sequence will be that for a circuit family
$\mathrm{NC}_R^{}$
hierarchies using first-order logic and guarded functional recursion. For that purpose, we now define a sequence which we will later use as part of the numbers of our gates in order to encode the gates’ depth into their numbers. The idea behind the construction of this sequence will be that for a circuit family
![]() $(C_n)_{n \in{\mathbb{N}}}$
with depth bounded by
$(C_n)_{n \in{\mathbb{N}}}$
with depth bounded by
![]() $c \cdot (\log _2 n)^i$
, each of the sequence’s elements is essentially a
$c \cdot (\log _2 n)^i$
, each of the sequence’s elements is essentially a
![]() $i$
digit base
$i$
digit base
![]() $c \cdot \lfloor \log _2 n\rfloor - 1$
number with each digit being encoded in unary and padded by zeroes. For readability purposes, we will refer to this encoding simply as a unary encoding. The sequence can then be seen as counting down to
$c \cdot \lfloor \log _2 n\rfloor - 1$
number with each digit being encoded in unary and padded by zeroes. For readability purposes, we will refer to this encoding simply as a unary encoding. The sequence can then be seen as counting down to
![]() $0$
in that interpretation. This will then result in a length of
$0$
in that interpretation. This will then result in a length of
![]() $c^i \cdot \lfloor \log _2 n\rfloor ^i \in{\mathcal{O}}((\log _2 n)^i)$
for fixed
$c^i \cdot \lfloor \log _2 n\rfloor ^i \in{\mathcal{O}}((\log _2 n)^i)$
for fixed
![]() $i$
. We begin by introducing our conventions regarding unary encodings of numbers.
$i$
. We begin by introducing our conventions regarding unary encodings of numbers.
Definition 40.
Let
![]() $n, \ell \in{\mathbb{N}}$
such that
$n, \ell \in{\mathbb{N}}$
such that
![]() $\ell \geq n$
. Then, we will refer to the function
$\ell \geq n$
. Then, we will refer to the function
![]() ${\mathrm{unary}}_\ell \colon{\mathbb{N}} \to \{0, 1\}^\ell$
defined as
${\mathrm{unary}}_\ell \colon{\mathbb{N}} \to \{0, 1\}^\ell$
defined as
as the (length
![]() $\ell$
) unary encoding of
$\ell$
) unary encoding of
![]() $n$
.
$n$
.
Definition 41.
For any binary string
![]() $\overline{a}$
of the form
$\overline{a}$
of the form
for some
![]() $k, m$
, we define the function
$k, m$
, we define the function
![]() ${\mathrm{uval}} \colon \{0, 1\}^\star \to{\mathbb{N}}$
defined as
${\mathrm{uval}} \colon \{0, 1\}^\star \to{\mathbb{N}}$
defined as
and call
![]() ${\mathrm{uval}}({\overline{a}})$
the value of the unary encoding
${\mathrm{uval}}({\overline{a}})$
the value of the unary encoding
![]() $\overline{a}$
.
$\overline{a}$
.
We now proceed to define the aforementioned sequence
![]() $d$
which we will later use to essentially encode our circuits’ gates’ depth into their gate numbers.
$d$
which we will later use to essentially encode our circuits’ gates’ depth into their gate numbers.
Definition 42.
For each
![]() $n, c, i \in{\mathbb{N}}_{\gt 0}$
, we define the sequence
$n, c, i \in{\mathbb{N}}_{\gt 0}$
, we define the sequence
![]() ${d}(n, c, i)$
as follows. For readability purposes, we leave out the arguments
${d}(n, c, i)$
as follows. For readability purposes, we leave out the arguments
![]() $(n, c, i)$
in the definition of the sequence and only write
$(n, c, i)$
in the definition of the sequence and only write
![]() $d$
instead of
$d$
instead of
![]() ${d}(n, c, i)$
.
${d}(n, c, i)$
.
-
1. Each element
 ${d}_\ell$
of
${d}_\ell$
of
 $d$
consists of
$d$
consists of
 $i$
tuples
$i$
tuples
 ${d}_{\ell, j}$
(
${d}_{\ell, j}$
(
 $1 \leq j \leq i$
), each of which is the length
$1 \leq j \leq i$
), each of which is the length
 $\lfloor c \cdot \log _2 n \rfloor - 1$
unary encoding of a number in
$\lfloor c \cdot \log _2 n \rfloor - 1$
unary encoding of a number in
 $[0, \lfloor c \cdot \log _2 n \rfloor - 1]$
.
$[0, \lfloor c \cdot \log _2 n \rfloor - 1]$
. -
2.
 ${d}_1 = 1 \dots 1$
(I. e.,
${d}_1 = 1 \dots 1$
(I. e.,
 ${d}_{1,j} ={\mathrm{unary}}_{\lfloor c \cdot \log _2 n\rfloor - 1}(c \cdot \lfloor \log _2 n \rfloor - 1) = 1 \dots 1$
for all
${d}_{1,j} ={\mathrm{unary}}_{\lfloor c \cdot \log _2 n\rfloor - 1}(c \cdot \lfloor \log _2 n \rfloor - 1) = 1 \dots 1$
for all
 $j$
with
$j$
with
 $1 \leq j \leq i$
.)
$1 \leq j \leq i$
.)
-
3.
 ${d}_{\ell + 1, i} = \begin{cases}{\mathrm{unary}}_{\lfloor c \cdot \log _2 n\rfloor -1}(\lfloor c \cdot \log _2 n\rfloor - 1 ) &\textrm{if }{\mathrm{uval}}({d}_{\ell, i}) = 0,\\[5pt] {\mathrm{unary}}_{\lfloor c \cdot \log _2 n\rfloor -1}({\mathrm{uval}}({d}_{\ell, i}) - 1) & \textrm{otherwise,} \end{cases}$
for all
${d}_{\ell + 1, i} = \begin{cases}{\mathrm{unary}}_{\lfloor c \cdot \log _2 n\rfloor -1}(\lfloor c \cdot \log _2 n\rfloor - 1 ) &\textrm{if }{\mathrm{uval}}({d}_{\ell, i}) = 0,\\[5pt] {\mathrm{unary}}_{\lfloor c \cdot \log _2 n\rfloor -1}({\mathrm{uval}}({d}_{\ell, i}) - 1) & \textrm{otherwise,} \end{cases}$
for all
 $\ell$
where
$\ell$
where
 ${d}_\ell \neq 0 \dots 0$
.
${d}_\ell \neq 0 \dots 0$
. -
4.
 ${d}_{\ell + 1, j} = \begin{cases}{\mathrm{unary}}_{\lfloor c \cdot \log _2 n\rfloor -1}({\mathrm{uval}}({d}_{\ell, j} - 1)) & \textrm{if }{\mathrm{uval}}({d}_{\ell, j+1}) = 0, \\[5pt] {d}_{\ell, j} & \textrm{otherwise,} \end{cases}$
for
${d}_{\ell + 1, j} = \begin{cases}{\mathrm{unary}}_{\lfloor c \cdot \log _2 n\rfloor -1}({\mathrm{uval}}({d}_{\ell, j} - 1)) & \textrm{if }{\mathrm{uval}}({d}_{\ell, j+1}) = 0, \\[5pt] {d}_{\ell, j} & \textrm{otherwise,} \end{cases}$
for
 $j \lt i$
.
$j \lt i$
.
Table 2 shows an abbreviated example for the sequence d. A further example as well as the full version of Table 2 can be found in the appendix as Tables 3 and 4.
Table 2. The sequence
![]() ${d}(8, 2, 2)$
${d}(8, 2, 2)$

Remark 43. Note that substracting the value
![]() $1$
in this unary encoding can be seen as an integer division by
$1$
in this unary encoding can be seen as an integer division by
![]() $2$
in binary. This will become useful later when putting this into the context of guarded functional recursion with
$2$
in binary. This will become useful later when putting this into the context of guarded functional recursion with
![]() $\mathrm{BIT}$
.
$\mathrm{BIT}$
.
Note that the length (i. e. the number of elements) of
![]() ${d}(8, 1, 2)$
is
${d}(8, 1, 2)$
is
and the length of
![]() ${d}(8, 2, 2)$
is
${d}(8, 2, 2)$
is
This is no coincidence. Next, we show that this observation holds in general.
Lemma 44.
Let
![]() $n, c, i \in{\mathbb{N}}_{\gt 0}$
. Then,
$n, c, i \in{\mathbb{N}}_{\gt 0}$
. Then,
![]() ${d}(n, c, i)$
has length
${d}(n, c, i)$
has length
![]() $c^i \cdot \lfloor \log _2 n\rfloor ^i$
.
$c^i \cdot \lfloor \log _2 n\rfloor ^i$
.
Proof.
Since for each element
![]() $e$
in
$e$
in
![]() ${d}(n, c, i)$
the successor rule can be interpreted as subtracting
${d}(n, c, i)$
the successor rule can be interpreted as subtracting
![]() $1$
from
$1$
from
![]() $e$
when
$e$
when
![]() $e$
is seen as a base
$e$
is seen as a base
![]() $c \cdot \lfloor \log _2 n \rfloor$
number with
$c \cdot \lfloor \log _2 n \rfloor$
number with
![]() $i$
digits, we are starting at the largest possible element in that sense (i. e.
$i$
digits, we are starting at the largest possible element in that sense (i. e.
![]() $1 \dots 1$
, which would correspond to
$1 \dots 1$
, which would correspond to
![]() $(c \cdot \lfloor \log _2 n \rfloor )^i - 1$
) and we are counting down to the lowest possible element (i. e.
$(c \cdot \lfloor \log _2 n \rfloor )^i - 1$
) and we are counting down to the lowest possible element (i. e.
![]() $0 \dots 0$
, corresponding to
$0 \dots 0$
, corresponding to
![]() $0$
), there are exactly
$0$
), there are exactly
![]() $(c \cdot \lfloor \log _2 n \rfloor )^i = c^i \cdot \lfloor \log _2 n\rfloor ^i$
elements in
$(c \cdot \lfloor \log _2 n \rfloor )^i = c^i \cdot \lfloor \log _2 n\rfloor ^i$
elements in
![]() ${d}(n, c, i)$
.
${d}(n, c, i)$
.
The remaining problem that stands in the way of using the sequence
![]() $d$
for the numbering of gates in descriptions for circuits is that the length of the elements in
$d$
for the numbering of gates in descriptions for circuits is that the length of the elements in
![]() $d$
depends on
$d$
depends on
![]() $n$
(which will be the number of input gates of our circuit). However, we can remedy this, since we essentially have access to base
$n$
(which will be the number of input gates of our circuit). However, we can remedy this, since we essentially have access to base
![]() $n$
numbers in the description for a circuit with
$n$
numbers in the description for a circuit with
![]() $n$
input gates (by virtue of interpreting circuit inputs as circuit structures). Combining those with the
$n$
input gates (by virtue of interpreting circuit inputs as circuit structures). Combining those with the
![]() $\mathrm{BIT}$
predicate and now interpreting the unary encoded tuples in elements of
$\mathrm{BIT}$
predicate and now interpreting the unary encoded tuples in elements of
![]() $d$
as binary numbers allows us to encode elements of
$d$
as binary numbers allows us to encode elements of
![]() $d$
using a constant number of digits.
$d$
using a constant number of digits.
Observation 45.
Let
![]() $n, c \in{\mathbb{N}}_{\gt 0}$
and
$n, c \in{\mathbb{N}}_{\gt 0}$
and
![]() $1 \leq \ell \leq c \cdot \lfloor \log _2 n \rfloor$
. The number
$1 \leq \ell \leq c \cdot \lfloor \log _2 n \rfloor$
. The number
![]() $2^\ell - 1$
can be encoded by a base
$2^\ell - 1$
can be encoded by a base
![]() $n$
number of length
$n$
number of length
![]() $c$
.
$c$
.
Proof.
The largest possible number of that form is
![]() $2^{c \cdot \lfloor \log _2 n \rfloor } - 1 \leq n^c - 1$
, which corresponds to "
$2^{c \cdot \lfloor \log _2 n \rfloor } - 1 \leq n^c - 1$
, which corresponds to "
![]() $\underbrace{{n-1} \dots{n-1}}_{c \text{ times}}$
" in base
$\underbrace{{n-1} \dots{n-1}}_{c \text{ times}}$
" in base
![]() $n$
. Therefore,
$n$
. Therefore,
![]() $2^{c \cdot \lfloor \log _2 n \rfloor } - 1$
can be encoded with
$2^{c \cdot \lfloor \log _2 n \rfloor } - 1$
can be encoded with
![]() $c$
base
$c$
base
![]() $n$
digits and thus also all smaller natural numbers can be encoded in this way.
$n$
digits and thus also all smaller natural numbers can be encoded in this way.
We can thus encode the binary valuations of tuples in elements of
![]() $d$
as base
$d$
as base
![]() $n$
numbers of length
$n$
numbers of length
![]() $c$
. Therefore, each element of
$c$
. Therefore, each element of
![]() $d$
can be encoded using
$d$
can be encoded using
![]() $i$
base
$i$
base
![]() $n$
numbers of length
$n$
numbers of length
![]() $c$
(or
$c$
(or
![]() $i \cdot c$
base
$i \cdot c$
base
![]() $n$
digits).
$n$
digits).
Before we proceed to use the sequence
![]() $d$
for circuit descriptions, we need one more lemma which provides a useful property of
$d$
for circuit descriptions, we need one more lemma which provides a useful property of
![]() $\mathrm{AC}_{\mathbb{R}}^{i}$
resp.
$\mathrm{AC}_{\mathbb{R}}^{i}$
resp.
![]() $\mathrm{NC}_R^{i}$
circuits. We would like to be able to talk about the depth of gates, that is the distance of a gate to the input gates of the circuit. For this reason, we will establish the fact that for the circuit families we investigate, circuits exist where for each gate
$\mathrm{NC}_R^{i}$
circuits. We would like to be able to talk about the depth of gates, that is the distance of a gate to the input gates of the circuit. For this reason, we will establish the fact that for the circuit families we investigate, circuits exist where for each gate
![]() $g$
, each input
$g$
, each input
![]() $g$
path has the same length.
$g$
path has the same length.
Lemma 46.
Let
![]() $L$
be in
$L$
be in
![]() $\mathrm{AC}_{R}^{i}$
or
$\mathrm{AC}_{R}^{i}$
or
![]() $\mathrm{NC}_R^{i}$
via the circuit family
$\mathrm{NC}_R^{i}$
via the circuit family
![]() ${\mathcal{C}} = (C_n)_{n \in{\mathbb{N}}}$
. Then, there exists a circuit family
${\mathcal{C}} = (C_n)_{n \in{\mathbb{N}}}$
. Then, there exists a circuit family
![]() ${\mathcal{C}}' = (C'_n)_{n \in{\mathbb{N}}}$
deciding
${\mathcal{C}}' = (C'_n)_{n \in{\mathbb{N}}}$
deciding
![]() $L$
, such that for all
$L$
, such that for all
![]() $n \in{\mathbb{N}}$
and each gate
$n \in{\mathbb{N}}$
and each gate
![]() $g$
in
$g$
in
![]() $C'_n$
, each path from an input gate to
$C'_n$
, each path from an input gate to
![]() $g$
in
$g$
in
![]() $C'_n$
has the same length. We call
$C'_n$
has the same length. We call
![]() $C'_n$
a balanced DAG.
$C'_n$
a balanced DAG.
The lemma follows from standard circuit manipulation (cf. also (Vollmer, Reference Vollmer1999, Exercise 4.35)). For convenience, a proof is provided in the appendix.
As previously mentioned, whenever we are dealing with balanced DAGs, we will refer to the unambiguous length from input gates to a gate
![]() $g$
as the depth of
$g$
as the depth of
![]() $g$
.
$g$
.
Now we will turn to a lemma which will then finally enable us to use the previously defined sequence
![]() $d$
to encode our gates’ depth into their circuit numbers. The idea is for a gate
$d$
to encode our gates’ depth into their circuit numbers. The idea is for a gate
![]() $g$
, to prepend the
$g$
, to prepend the
![]() $\textit{depth}(g)$
th element of
$\textit{depth}(g)$
th element of
![]() $d$
to the gate number of
$d$
to the gate number of
![]() $g$
. This way each path from an input gate to the output essentially contains elements of
$g$
. This way each path from an input gate to the output essentially contains elements of
![]() $d$
in order in the prefixes of its gate numbers.
$d$
in order in the prefixes of its gate numbers.
This, combined with Lemma 44, provides us with a way to logically ensure the polylogarithmic depth of a circuit given as a circuit structure.
Lemma 47.
Let
![]() $L$
be in
$L$
be in
![]() $\mathrm{AC}_{R}^{i}$
or
$\mathrm{AC}_{R}^{i}$
or
![]() $\mathrm{NC}_R^{i}$
via the circuit family
$\mathrm{NC}_R^{i}$
via the circuit family
![]() ${\mathcal{C}} = (C_n)_{n \in{\mathbb{N}}}$
. Then, there exists an
${\mathcal{C}} = (C_n)_{n \in{\mathbb{N}}}$
. Then, there exists an
![]() $\mathrm{AC}_{R}^{i}$
(resp.
$\mathrm{AC}_{R}^{i}$
(resp.
![]() $\mathrm{NC}_R^{i}$
) circuit family
$\mathrm{NC}_R^{i}$
) circuit family
![]() ${\mathcal{C}}' = (C'_n)_{n \in{\mathbb{N}}}$
deciding
${\mathcal{C}}' = (C'_n)_{n \in{\mathbb{N}}}$
deciding
![]() $L$
with depth bounded by
$L$
with depth bounded by
![]() $c \cdot (\log _2 n)^i$
, such that each circuit in
$c \cdot (\log _2 n)^i$
, such that each circuit in
![]() ${\mathcal{C}}'$
is a balanced DAG, numbered by base
${\mathcal{C}}'$
is a balanced DAG, numbered by base
![]() $n$
numbers and each gate
$n$
numbers and each gate
![]() $g$
in
$g$
in
![]() ${\mathcal{C}}'$
encodes the
${\mathcal{C}}'$
encodes the
![]() $\textit{depth}(g)$
’s element of
$\textit{depth}(g)$
’s element of
![]() $d$
in the first
$d$
in the first
![]() $c \cdot i$
digits of its gate number.
$c \cdot i$
digits of its gate number.
The numbering after the first
![]() $c \cdot i$
digits can be chosen arbitrarily.
$c \cdot i$
digits can be chosen arbitrarily.
Proof.
Let
![]() $L \in{\mathrm{AC}_{R}^{i}}$
or
$L \in{\mathrm{AC}_{R}^{i}}$
or
![]() $L \in \mathrm{NC}_R^{i}$
via the circuit family
$L \in \mathrm{NC}_R^{i}$
via the circuit family
![]() ${\mathcal{C}} = (C_n)_{n \in{\mathbb{N}}}$
the depth of which is bounded by
${\mathcal{C}} = (C_n)_{n \in{\mathbb{N}}}$
the depth of which is bounded by
![]() $c_1 \cdot (\log _2 n)^i$
. Without loss of generality, let the circuits of
$c_1 \cdot (\log _2 n)^i$
. Without loss of generality, let the circuits of
![]() $\mathcal{C}$
be balanced DAGs as per Lemma 46. That means that for each circuit
$\mathcal{C}$
be balanced DAGs as per Lemma 46. That means that for each circuit
![]() $C_n$
in
$C_n$
in
![]() $\mathcal{C}$
, for each gate
$\mathcal{C}$
, for each gate
![]() $g$
in
$g$
in
![]() $C_n$
, the length of all paths from input gates to
$C_n$
, the length of all paths from input gates to
![]() $g$
is the same. Let
$g$
is the same. Let
![]() $c \in{\mathbb{N}}_{\gt 0}$
be such that
$c \in{\mathbb{N}}_{\gt 0}$
be such that
![]() $c^i \cdot \lfloor \log _2 n\rfloor ^i$
is larger than the depth of
$c^i \cdot \lfloor \log _2 n\rfloor ^i$
is larger than the depth of
![]() $C_n$
(which is bounded by
$C_n$
(which is bounded by
![]() $c_1 \cdot (\log _2 n)^i$
). We pad each path in
$c_1 \cdot (\log _2 n)^i$
). We pad each path in
![]() $C_n$
to length
$C_n$
to length
![]() $c^i \cdot \lfloor \log _2 n\rfloor ^i$
by replacing each edge from an input gate to a gate in
$c^i \cdot \lfloor \log _2 n\rfloor ^i$
by replacing each edge from an input gate to a gate in
![]() $C_n$
by a path of dummy gates of length
$C_n$
by a path of dummy gates of length
![]() $c^i \cdot \lfloor \log _2 n\rfloor ^i - \textit{depth}(C_n)$
so that the resulting circuit has exactly depth
$c^i \cdot \lfloor \log _2 n\rfloor ^i - \textit{depth}(C_n)$
so that the resulting circuit has exactly depth
![]() $c^i \cdot \lfloor \log _2 n\rfloor ^i$
.
$c^i \cdot \lfloor \log _2 n\rfloor ^i$
.
We now use any base
![]() $n$
numbering for the gates of
$n$
numbering for the gates of
![]() $C_n$
and for each gate
$C_n$
and for each gate
![]() $g$
prepend the
$g$
prepend the
![]() $\text{depth}(g)$
th element of
$\text{depth}(g)$
th element of
![]() ${d}(n, c, i)$
to the number of
${d}(n, c, i)$
to the number of
![]() $g$
. Since we made sure that each input-output-path in
$g$
. Since we made sure that each input-output-path in
![]() $C_n$
has length exactly
$C_n$
has length exactly
![]() $c^i \cdot \lfloor \log _2 n\rfloor ^i$
, we can encode exactly the sequence
$c^i \cdot \lfloor \log _2 n\rfloor ^i$
, we can encode exactly the sequence
![]() ${d}(n, c, i)$
in the numbers of each input-output-path. So now for each input-output-path, the first
${d}(n, c, i)$
in the numbers of each input-output-path. So now for each input-output-path, the first
![]() $c \cdot i$
digits of gate numbers encode the elements of
$c \cdot i$
digits of gate numbers encode the elements of
![]() ${d}(n, c, i)$
in the order that they appear in the sequence.
${d}(n, c, i)$
in the order that they appear in the sequence.
With the normal form from Lemma 47 and the previous definitions, we can now turn to a theorem characterizing
![]() $\mathrm{AC}_{R}^{i}$
and
$\mathrm{AC}_{R}^{i}$
and
![]() $\mathrm{NC}_R^{i}$
logically by tying it all together.
$\mathrm{NC}_R^{i}$
logically by tying it all together.
Theorem 48.
-
1.
 ${\mathrm{AC}_{R}^{i}} = \mathrm{FO}_{R}[{\mathrm{Arb}_{R}}]+{\textrm{SUM}_{R}}+{\textrm{PROD}_{R}}+{{\mathrm{GFR}_{R}}^i}$
for
${\mathrm{AC}_{R}^{i}} = \mathrm{FO}_{R}[{\mathrm{Arb}_{R}}]+{\textrm{SUM}_{R}}+{\textrm{PROD}_{R}}+{{\mathrm{GFR}_{R}}^i}$
for
 $i \in{\mathbb{N}}$
$i \in{\mathbb{N}}$
-
2.
 $\mathrm{NC}_R^{i} = \mathrm{FO}_{R}[{\mathrm{Arb}_{R}}]+{\textrm{SUM}_{R}}+{\textrm{PROD}_{R}}+{{{\mathrm{GFR}_{R, \mathrm{bound}}}^i}}$
for
$\mathrm{NC}_R^{i} = \mathrm{FO}_{R}[{\mathrm{Arb}_{R}}]+{\textrm{SUM}_{R}}+{\textrm{PROD}_{R}}+{{{\mathrm{GFR}_{R, \mathrm{bound}}}^i}}$
for
 $i \in{\mathbb{N}}_{\gt 0}$
$i \in{\mathbb{N}}_{\gt 0}$
Proof. We start by showing the inclusions of the circuit classes in the respective logics and will then proceed with the converse directions.
Step 1:
![]() ${\mathrm{AC}_{R}^{i}} \subseteq \mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}} +{{\mathrm{GFR}_{R}}^i}$
:
${\mathrm{AC}_{R}^{i}} \subseteq \mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}} +{{\mathrm{GFR}_{R}}^i}$
:
Let
![]() $L \in{\mathrm{AC}_{R}^{i}}$
via the nonuniform circuit family
$L \in{\mathrm{AC}_{R}^{i}}$
via the nonuniform circuit family
![]() ${\mathcal{C}} = (C_n)_{n \in{\mathbb{N}}}$
and let the depth of
${\mathcal{C}} = (C_n)_{n \in{\mathbb{N}}}$
and let the depth of
![]() $\mathcal{C}$
be bounded by
$\mathcal{C}$
be bounded by
![]() $c \cdot (\log _2 n)^i$
. We construct an
$c \cdot (\log _2 n)^i$
. We construct an
![]() $\mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}} +{{\mathrm{GFR}_{R}^i}}$
sentence
$\mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}} +{{\mathrm{GFR}_{R}^i}}$
sentence
![]() $\varphi$
defining
$\varphi$
defining
![]() $L$
. As the circuit input is interpreted as a circuit structure, the signature
$L$
. As the circuit input is interpreted as a circuit structure, the signature
![]() $\sigma$
of
$\sigma$
of
![]() $\varphi$
contains only the single unary function symbol
$\varphi$
contains only the single unary function symbol
![]() $f_{\mathrm{element}}$
.
$f_{\mathrm{element}}$
.
We define the following additional relations and functions which will essentially encode our given circuits. We will have access to them because of the
![]() $\mathrm{Arb}_{R}$
extension of our logic and we use relations here instead of functions for ease of reading, since we essentially have access to relations in functional structures if we consider the respective characteristic functions of the relations instead.
$\mathrm{Arb}_{R}$
extension of our logic and we use relations here instead of functions for ease of reading, since we essentially have access to relations in functional structures if we consider the respective characteristic functions of the relations instead.
-
•
 $G_+({\overline{x}})\iff{\overline{x}}$
is an addition gate.
$G_+({\overline{x}})\iff{\overline{x}}$
is an addition gate. -
•
 $G_\times ({\overline{x}})\iff{\overline{x}}$
is a multiplication gate.
$G_\times ({\overline{x}})\iff{\overline{x}}$
is a multiplication gate. -
•
 $G_\lt ({\overline{x}})\iff{\overline{x}}$
is a
$G_\lt ({\overline{x}})\iff{\overline{x}}$
is a
 $\lt$
gate, the left predecessor of which is lexicographically lower than the right predecessor.
$\lt$
gate, the left predecessor of which is lexicographically lower than the right predecessor. -
•
 $G_{\mathrm{input}}({\overline{x}}) \iff$
$G_{\mathrm{input}}({\overline{x}}) \iff$
 $\overline{x}$
is an input gate.
$\overline{x}$
is an input gate. -
•
 $G_E({\overline{x}},{\overline{y}})\iff{\overline{y}}$
is a successor gate of
$G_E({\overline{x}},{\overline{y}})\iff{\overline{y}}$
is a successor gate of
 $\overline{x}$
.
$\overline{x}$
. -
•
 $G_{\mathrm{output}}({\overline{x}})\iff{\overline{x}}$
is the output gate.
$G_{\mathrm{output}}({\overline{x}})\iff{\overline{x}}$
is the output gate. -
•
 $G_{\mathrm{const}}({\overline{x}})\iff{\overline{x}}$
is a constant gate.
$G_{\mathrm{const}}({\overline{x}})\iff{\overline{x}}$
is a constant gate. -
•
 $f_{\mathrm{const\_val}}({\overline{x}}) = y \in R$
$f_{\mathrm{const\_val}}({\overline{x}}) = y \in R$
 $\iff$
$\iff$
 $y$
is the value of
$y$
is the value of
 $\overline{x}$
if
$\overline{x}$
if
 $\overline{x}$
is a constant gate and
$\overline{x}$
is a constant gate and
 $y = 0$
otherwise.
$y = 0$
otherwise.
Without loss of generality let all circuits of
![]() $\mathcal{C}$
be in the normal form of Lemma 47 and let the numbering of
$\mathcal{C}$
be in the normal form of Lemma 47 and let the numbering of
![]() $C_n$
be such that the last digit of the number of the
$C_n$
be such that the last digit of the number of the
![]() $j$
th input gate is
$j$
th input gate is
![]() $j$
for
$j$
for
![]() $1 \leq j \leq n$
. Recall that this means that for each gate number of a gate
$1 \leq j \leq n$
. Recall that this means that for each gate number of a gate
![]() $g$
represented as a tuple
$g$
represented as a tuple
![]() $\overline{g}$
, the first
$\overline{g}$
, the first
![]() $c \cdot i$
elements of
$c \cdot i$
elements of
![]() $\overline{g}$
encode the
$\overline{g}$
encode the
![]() $\textit{depth}(g)$
th element of
$\textit{depth}(g)$
th element of
![]() $d(n, c, i)$
. The following sentence
$d(n, c, i)$
. The following sentence
![]() $\varphi$
defines
$\varphi$
defines
![]() $L$
:
$L$
:
where
![]() $t$
is defined as follows (with
$t$
is defined as follows (with
![]() $\overline{z_j}$
denoting the
$\overline{z_j}$
denoting the
![]() $j$
th
$j$
th
![]() $c$
long subtuple in the
$c$
long subtuple in the
![]() $c \cdot i$
long prefix of
$c \cdot i$
long prefix of
![]() $\overline{z}$
, which, as per the normal form of Lemma 47, encodes the
$\overline{z}$
, which, as per the normal form of Lemma 47, encodes the
![]() $j$
th tuple of an element of
$j$
th tuple of an element of
![]() ${d}(n, c, i)$
):
${d}(n, c, i)$
):
 \begin{equation*} \begin {array}{r@{\quad}r@{\quad}l@{\quad}l} t({\overline {y}}, f) \;:=\; & \chi [G_+({\overline {y}})] & \times &\textbf {sum}_{{\overline {z}}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {z_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {z}})\right ) f({\overline {z}})\ +\\[5pt] & \chi [G_\times ({\overline {y}})] & \times & \textbf {prod}_{\overline {z}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {z_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {z}})\right ) f({\overline {z}})\ +\\[5pt] & \chi [G_\lt ({\overline {y}})]&\times & \textbf {max}_{{\overline {z}}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {z_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {z}})\right ) \\[5pt] & & &\Bigg (\textbf {max}_{{\overline {b}}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {b_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {b_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {b}}) \land {\overline {b}} \lt {\overline {z}})\right )\\[5pt] & & &\left ( \chi [f({\overline {b}}) \lt f({\overline {z}})]\right ) \Bigg )\ +\\[5pt] & \chi [G_{\mathrm {input}}({\overline {y}})] & \times & {f_{\mathrm {element}}(y_{\lvert {\overline {y}}\rvert })}\ +\\[5pt] & \chi [G_{\mathrm {const}}({\overline {y}})] & \times & f_{\mathrm {const\_val}}({\overline {y}})\ +\\[5pt] & \chi [G_{\mathrm {output}}({\overline {y}})] & \times & \textbf {sum}_{{\overline {z}}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {z_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {z}})\right ) f({\overline {z}}). \end {array} \end{equation*}
\begin{equation*} \begin {array}{r@{\quad}r@{\quad}l@{\quad}l} t({\overline {y}}, f) \;:=\; & \chi [G_+({\overline {y}})] & \times &\textbf {sum}_{{\overline {z}}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {z_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {z}})\right ) f({\overline {z}})\ +\\[5pt] & \chi [G_\times ({\overline {y}})] & \times & \textbf {prod}_{\overline {z}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {z_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {z}})\right ) f({\overline {z}})\ +\\[5pt] & \chi [G_\lt ({\overline {y}})]&\times & \textbf {max}_{{\overline {z}}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {z_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {z}})\right ) \\[5pt] & & &\Bigg (\textbf {max}_{{\overline {b}}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {b_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {b_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {b}}) \land {\overline {b}} \lt {\overline {z}})\right )\\[5pt] & & &\left ( \chi [f({\overline {b}}) \lt f({\overline {z}})]\right ) \Bigg )\ +\\[5pt] & \chi [G_{\mathrm {input}}({\overline {y}})] & \times & {f_{\mathrm {element}}(y_{\lvert {\overline {y}}\rvert })}\ +\\[5pt] & \chi [G_{\mathrm {const}}({\overline {y}})] & \times & f_{\mathrm {const\_val}}({\overline {y}})\ +\\[5pt] & \chi [G_{\mathrm {output}}({\overline {y}})] & \times & \textbf {sum}_{{\overline {z}}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {z_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {z}})\right ) f({\overline {z}}). \end {array} \end{equation*}
Here, the relations
![]() $G_{g}({\overline{y}})$
for
$G_{g}({\overline{y}})$
for
![]() $g \in \{+, \times, \lt, \textrm{input}, \textrm{const}, \textrm{output}\}$
give information about the gate type of the gate encoded by
$g \in \{+, \times, \lt, \textrm{input}, \textrm{const}, \textrm{output}\}$
give information about the gate type of the gate encoded by
![]() $\overline{y}$
and are provided by the
$\overline{y}$
and are provided by the
![]() $\mathrm{Arb}_{R}$
extension of
$\mathrm{Arb}_{R}$
extension of
![]() $\mathrm{FO}_{R}$
. They are interpreted as mentioned above. The
$\mathrm{FO}_{R}$
. They are interpreted as mentioned above. The
![]() $\mathrm{BIT}$
predicate is provided in the same way.
$\mathrm{BIT}$
predicate is provided in the same way.
We will now prove that
![]() $\varphi$
does indeed define
$\varphi$
does indeed define
![]() $L$
. Let
$L$
. Let
![]() ${\overline{a}} \in R^n$
be the input to
${\overline{a}} \in R^n$
be the input to
![]() $C_n$
. We will show that for all
$C_n$
. We will show that for all
![]() ${\overline{g}} \in R^l$
, where
${\overline{g}} \in R^l$
, where
![]() $l$
is the encoding length of a gate in
$l$
is the encoding length of a gate in
![]() $\mathcal{C}$
, the value of the gate encoded by
$\mathcal{C}$
, the value of the gate encoded by
![]() $\overline{g}$
in the computation of
$\overline{g}$
in the computation of
![]() $C_n$
when
$C_n$
when
![]() $C_n$
is given
$C_n$
is given
![]() $\overline{a}$
as the input is
$\overline{a}$
as the input is
![]() $f({\overline{g}})$
. Let
$f({\overline{g}})$
. Let
![]() $g$
be the gate encoded by
$g$
be the gate encoded by
![]() $\overline{g}$
. We will argue by induction on the depth of the gate
$\overline{g}$
. We will argue by induction on the depth of the gate
![]() $g$
, that is by the distance between
$g$
, that is by the distance between
![]() $g$
and an input gate.
$g$
and an input gate.
![]() $d = 0$
: If
$d = 0$
: If
![]() $d = 0$
, then
$d = 0$
, then
![]() $g$
is an input gate. Therefore, the only summand in
$g$
is an input gate. Therefore, the only summand in
![]() $t({\overline{g}}, f)$
that is not trivially
$t({\overline{g}}, f)$
that is not trivially
![]() $0$
is the fourth one, which is equal to
$0$
is the fourth one, which is equal to
![]() $f_{\mathrm{element}}(g_{\lvert{\overline{g}}\rvert })$
(which is the value of the
$f_{\mathrm{element}}(g_{\lvert{\overline{g}}\rvert })$
(which is the value of the
![]() $g_{\lvert{\overline{g}}\rvert }$
th input gate).
$g_{\lvert{\overline{g}}\rvert }$
th input gate).
![]() $d \to d+1$
: Since
$d \to d+1$
: Since
![]() $d + 1 \gt 0$
,
$d + 1 \gt 0$
,
![]() $g$
is not an input gate. This means that there are the following 5 possibilities for
$g$
is not an input gate. This means that there are the following 5 possibilities for
![]() $g$
:
$g$
:
-
1.
 $g$
is an addition gate: In that case, the only summand in
$g$
is an addition gate: In that case, the only summand in
 $t({\overline{g}}, f)$
which is not trivially
$t({\overline{g}}, f)$
which is not trivially
 $0$
is the first one. All predecessors of
$0$
is the first one. All predecessors of
 $g$
have a number, the first
$g$
have a number, the first
 $c \cdot i$
digits of which are the successor of the first
$c \cdot i$
digits of which are the successor of the first
 $c \cdot i$
digits of
$c \cdot i$
digits of
 $g$
in the sequence
$g$
in the sequence
 ${d}(n, c, i)$
because of the normal form of Lemma 47. Additionally, the relativization ensures that the gate encoded by
${d}(n, c, i)$
because of the normal form of Lemma 47. Additionally, the relativization ensures that the gate encoded by
 $\overline{z}$
in the respective summand has exactly the successor in the sequence
$\overline{z}$
in the respective summand has exactly the successor in the sequence
 ${d}(n, c, i)$
of
${d}(n, c, i)$
of
 $g$
’s first
$g$
’s first
 $c \cdot i$
digits in its first
$c \cdot i$
digits in its first
 $c \cdot i$
digits. This means that by the induction hypothesisyields exactly the sum of all the values of predecessor gates of
$c \cdot i$
digits. This means that by the induction hypothesisyields exactly the sum of all the values of predecessor gates of \begin{equation*} \textbf {sum}_{{\overline {z}}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {z_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {z}})\right ) f({\overline {z}}) \end{equation*}
\begin{equation*} \textbf {sum}_{{\overline {z}}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {z_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {z}})\right ) f({\overline {z}}) \end{equation*}
 $g$
.
$g$
.
-
2.
 $g$
is a multiplication gate: Analogously to the above case,yields exactly the product of all predecessor gates of
$g$
is a multiplication gate: Analogously to the above case,yields exactly the product of all predecessor gates of \begin{equation*} \textbf {prod}_{\overline {z}}.\left (\bigvee \limits _{j = 1}^i \left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {z_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {z}})\right ) f({\overline {z}}) \end{equation*}
\begin{equation*} \textbf {prod}_{\overline {z}}.\left (\bigvee \limits _{j = 1}^i \left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {z_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {z}})\right ) f({\overline {z}}) \end{equation*}
 $g$
.
$g$
.
-
3.
 $g$
is a
$g$
is a
 $\lt$
gate: In that case, the relativizationmakes sure that
$\lt$
gate: In that case, the relativizationmakes sure that \begin{equation*} \textbf {max}_{{\overline {z}}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {z_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {z}})\right ) \end{equation*}
\begin{equation*} \textbf {max}_{{\overline {z}}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {z_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {z}})\right ) \end{equation*}
 $\overline{z}$
is the maximum gate number of a predecessor of
$\overline{z}$
is the maximum gate number of a predecessor of
 $g$
andmakes sure that
$g$
andmakes sure that \begin{equation*} \Bigg (\textbf {max}_{{\overline {b}}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {b_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {b_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {b}}) \land {\overline {b}} \lt {\overline {z}})\right ) \left ( \chi [f({\overline {b}}) \lt f({\overline {z}})]\right ) \Bigg ) \end{equation*}
\begin{equation*} \Bigg (\textbf {max}_{{\overline {b}}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {b_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {b_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {b}}) \land {\overline {b}} \lt {\overline {z}})\right ) \left ( \chi [f({\overline {b}}) \lt f({\overline {z}})]\right ) \Bigg ) \end{equation*}
 $\overline{b}$
is the gate number of the other predecessor of
$\overline{b}$
is the gate number of the other predecessor of
 $g$
and that therefore
$g$
and that therefore
 $\chi [f({\overline{b}}) \lt f({\overline{z}})]$
is the value of
$\chi [f({\overline{b}}) \lt f({\overline{z}})]$
is the value of
 $t({\overline{g}}, f)$
, which is exactly the value of
$t({\overline{g}}, f)$
, which is exactly the value of
 $g$
in the computation of
$g$
in the computation of
 $C_n$
.
$C_n$
.
-
4.
 $g$
is a constant gate: Since
$g$
is a constant gate: Since
 $f_{\mathrm{const\_val}}({\overline{g}})$
returns exactly the constant that
$f_{\mathrm{const\_val}}({\overline{g}})$
returns exactly the constant that
 $g$
is labelled with, that value is taken by
$g$
is labelled with, that value is taken by
 $g$
.
$g$
. -
5.
 $g$
is the output gate: In that case,
$g$
is the output gate: In that case,
 $g$
only has one predecessor and thusensures that
$g$
only has one predecessor and thusensures that \begin{equation*} \textbf {sum}_{{\overline {z}}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {z_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {z}})\right ) f({\overline {z}}) \end{equation*}
\begin{equation*} \textbf {sum}_{{\overline {z}}}.\left (\bigvee \limits _{j = 1}^i\left ( {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline {z_k}} \leq {\overline {y_k}}\right ) \land G_{\mathrm {E}}({\overline {y}}, {\overline {z}})\right ) f({\overline {z}}) \end{equation*}
 $g$
takes the value of that predecessor, since there is only one element matching the relativization.
$g$
takes the value of that predecessor, since there is only one element matching the relativization.
Finally, by
we make sure that there exists an output gate which has the value
![]() $1$
at the end of the computation.
$1$
at the end of the computation.
Step 2:
![]() $\mathrm{NC}_R^{i} \subseteq \mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}} +{{\mathrm{GFR}_{R, \mathrm{bound}}^i}}$
:
$\mathrm{NC}_R^{i} \subseteq \mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}} +{{\mathrm{GFR}_{R, \mathrm{bound}}^i}}$
:
The proof for this inclusion follows in the same way as the proof for the
![]() $\mathrm{AC}_{{R}}^{i}$
case, by just replacing all guarded aggregations in the formulae by bounded guarded aggregations.
$\mathrm{AC}_{{R}}^{i}$
case, by just replacing all guarded aggregations in the formulae by bounded guarded aggregations.
Step 3:
![]() $\mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}} +{{\mathrm{GFR}_{R}^i}} \subseteq{\mathrm{AC}_{R}^{i}}$
:
$\mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}} +{{\mathrm{GFR}_{R}^i}} \subseteq{\mathrm{AC}_{R}^{i}}$
:
Let
![]() $L \in \mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}} +{{\mathrm{GFR}_{R}^i}}$
via a formula
$L \in \mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}} +{{\mathrm{GFR}_{R}^i}}$
via a formula
![]() $\varphi$
over some signature
$\varphi$
over some signature
![]() $\sigma = (L_s, L_f, L_a)$
and let there be only one occurrence of a
$\sigma = (L_s, L_f, L_a)$
and let there be only one occurrence of a
![]() ${\mathrm{GFR}_{R}^i}$
operator in
${\mathrm{GFR}_{R}^i}$
operator in
![]() $\varphi$
. This proof easily extends to the general case. This means that
$\varphi$
. This proof easily extends to the general case. This means that
![]() $\varphi$
is of the form
$\varphi$
is of the form
We now construct an
![]() $\mathrm{AC}_{R}^{i}$
circuit family
$\mathrm{AC}_{R}^{i}$
circuit family
![]() ${\mathcal{C}} = (C_n)_{n \in{\mathbb{N}}}$
deciding
${\mathcal{C}} = (C_n)_{n \in{\mathbb{N}}}$
deciding
![]() $L$
.
$L$
.
We first construct an
![]() $\mathrm{AC}_{R}^{i}$
family evaluating
$\mathrm{AC}_{R}^{i}$
family evaluating
![]() $\varphi$
without the occurrences of
$\varphi$
without the occurrences of
![]() $f$
as in Theorem 30. This is possible, since
$f$
as in Theorem 30. This is possible, since
![]() $\varphi$
is an
$\varphi$
is an
![]() $\mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}}$
formula over
$\mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}}$
formula over
![]() $(L_s, L_f, L_a \cup \{f\})$
, and by Theorem 30, there is such a circuit family for
$(L_s, L_f, L_a \cup \{f\})$
, and by Theorem 30, there is such a circuit family for
![]() $\varphi$
.
$\varphi$
.
Next, we explain how we build an
![]() $\mathrm{AC}_{R}^{i}$
circuit family for the whole formula
$\mathrm{AC}_{R}^{i}$
circuit family for the whole formula
![]() $\varphi$
from this point. For this, we need to construct an
$\varphi$
from this point. For this, we need to construct an
![]() $\mathrm{AC}_{R}^{i}$
circuit family computing the value of
$\mathrm{AC}_{R}^{i}$
circuit family computing the value of
![]() $f({\overline{x}},{\overline{y}})$
for each pair
$f({\overline{x}},{\overline{y}})$
for each pair
![]() ${\overline{a}},{\overline{b}}$
with
${\overline{a}},{\overline{b}}$
with
![]() ${\overline{a}} \in A^{\lvert{\overline{x}} \rvert }$
for some
${\overline{a}} \in A^{\lvert{\overline{x}} \rvert }$
for some
![]() $k \in{\mathbb{N}}$
and
$k \in{\mathbb{N}}$
and
![]() ${\overline{b}} \in A^{i \cdot \lvert{\overline{y_1}} \rvert + \lvert{\overline{y_{i+1}}} \rvert }$
. Notice that
${\overline{b}} \in A^{i \cdot \lvert{\overline{y_1}} \rvert + \lvert{\overline{y_{i+1}}} \rvert }$
. Notice that
![]() $t$
is an
$t$
is an
![]() $\mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}} +{{\mathrm{GFR}_{R}}^i}$
number term and can therefore be evaluated by an
$\mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}} +{{\mathrm{GFR}_{R}}^i}$
number term and can therefore be evaluated by an
![]() $\mathrm{AC}_{R}^{0}$
circuit family, except for the occurrences of
$\mathrm{AC}_{R}^{0}$
circuit family, except for the occurrences of
![]() $f$
. We now obtain
$f$
. We now obtain
![]() $C_n$
by taking the
$C_n$
by taking the
![]() $n$
th circuit of all those (polynomially many)
$n$
th circuit of all those (polynomially many)
![]() $\mathrm{AC}_{R}^{0}$
circuit families and for all
$\mathrm{AC}_{R}^{0}$
circuit families and for all
![]() ${\overline{a}},{\overline{b}}$
replacing the gate labelled
${\overline{a}},{\overline{b}}$
replacing the gate labelled
![]() $f({\overline{a}},{\overline{b}})$
by the output gate of the circuit computing
$f({\overline{a}},{\overline{b}})$
by the output gate of the circuit computing
![]() $t({\overline{a}},{\overline{b}}, f)$
.
$t({\overline{a}},{\overline{b}}, f)$
.
Since all occurrences of
![]() $f({\overline{x}},{\overline{y}})$
are in the scope of a guarded aggregation
$f({\overline{x}},{\overline{y}})$
are in the scope of a guarded aggregation
 \begin{equation*} A_{{\overline {z_1}}, \dots, {\overline {z_i}}}.\left (\bigvee \limits _{j = 1}^i {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1} {\overline {z_k}} \leq {\overline {y_k}}\right )\end{equation*}
\begin{equation*} A_{{\overline {z_1}}, \dots, {\overline {z_i}}}.\left (\bigvee \limits _{j = 1}^i {\overline {z_j}} \leq {\overline {y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1} {\overline {z_k}} \leq {\overline {y_k}}\right )\end{equation*}
the number of steps from any
![]() $f({\overline{a}},{\overline{b}})$
before reaching a function call of the form
$f({\overline{a}},{\overline{b}})$
before reaching a function call of the form
![]() $f({\overline{c}},{\overline{0}},{\overline{d}})$
, with
$f({\overline{c}},{\overline{0}},{\overline{d}})$
, with
![]() $\lvert{\overline{c}} \rvert = \lvert{\overline{x}} \rvert$
and
$\lvert{\overline{c}} \rvert = \lvert{\overline{x}} \rvert$
and
![]() $\lvert{\overline{d}} \rvert = \lvert{\overline{y_{i+1} \rvert }}$
, terminating the recursion, is bounded by
$\lvert{\overline{d}} \rvert = \lvert{\overline{y_{i+1} \rvert }}$
, terminating the recursion, is bounded by
![]() ${\mathcal{O}}((\log _2 n)^i)$
as per Lemma 37.
${\mathcal{O}}((\log _2 n)^i)$
as per Lemma 37.
Since each such step – computing
![]() $f({\overline{a_1}},{\overline{b_1}})$
, when given values of the next recursive call
$f({\overline{a_1}},{\overline{b_1}})$
, when given values of the next recursive call
![]() $f({\overline{a_2}},{\overline{b_2}})$
– is done by an
$f({\overline{a_2}},{\overline{b_2}})$
– is done by an
![]() $\mathrm{AC}_{R}^{0}$
circuit and therefore has constant depth, in total, any path from the first recursive call to the termination has length in
$\mathrm{AC}_{R}^{0}$
circuit and therefore has constant depth, in total, any path from the first recursive call to the termination has length in
![]() ${\mathcal{O}}((\log _2 n)^i)$
. Since the starting circuit deciding
${\mathcal{O}}((\log _2 n)^i)$
. Since the starting circuit deciding
![]() $\varphi$
had constant depth, the circuit we constructed now has polylogarithmic depth in total. And given that we only added polynomially many subcircuits with polynomially many gates each, the whole circuit is an
$\varphi$
had constant depth, the circuit we constructed now has polylogarithmic depth in total. And given that we only added polynomially many subcircuits with polynomially many gates each, the whole circuit is an
![]() $\mathrm{AC}_{{R}}^{i}$
circuit deciding
$\mathrm{AC}_{{R}}^{i}$
circuit deciding
![]() $\varphi$
.
$\varphi$
.
For the general case of several
![]() ${\mathrm{GFR}_{R}^i}$
operators, we construct a circuit for each operator in the same way and connect them to the circuit evaluating
${\mathrm{GFR}_{R}^i}$
operators, we construct a circuit for each operator in the same way and connect them to the circuit evaluating
![]() $\varphi$
.
$\varphi$
.
Step 4:
![]() $\mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}} +{{\mathrm{GFR}_{R, \mathrm{bound}}^i}} \subseteq \mathrm{NC}_R^{i}$
:
$\mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}} +{{\mathrm{GFR}_{R, \mathrm{bound}}^i}} \subseteq \mathrm{NC}_R^{i}$
:
This case can be proven analogously to the case for
![]() $\mathrm{AC}_{R}^{i}$
. Instead of
$\mathrm{AC}_{R}^{i}$
. Instead of
![]() $\mathrm{AC}_{R}^{0}$
families for evaluating
$\mathrm{AC}_{R}^{0}$
families for evaluating
![]() $\varphi$
and
$\varphi$
and
![]() $t$
, we now need to use
$t$
, we now need to use
![]() $\mathrm{NC}_R^{1}$
families, which is why this result only holds for
$\mathrm{NC}_R^{1}$
families, which is why this result only holds for
![]() $i \gt 0$
. With this, we have logarithmic depth for evaluating
$i \gt 0$
. With this, we have logarithmic depth for evaluating
![]() $t$
, which would generally be a problem, since repeating this
$t$
, which would generally be a problem, since repeating this
![]() $(\log _2 n)^i$
times would yield a
$(\log _2 n)^i$
times would yield a
![]() $\mathrm{NC}_R^{i+1}$
family.
$\mathrm{NC}_R^{i+1}$
family.
However, this would only be the case, if the
![]() $f$
gate (which would later be replaced by an edge to another copy of the circuit evaluating
$f$
gate (which would later be replaced by an edge to another copy of the circuit evaluating
![]() $t$
) was to occur at logarithmic depth in the circuit evaluating
$t$
) was to occur at logarithmic depth in the circuit evaluating
![]() $t$
. Fortunately, due to our requirement that
$t$
. Fortunately, due to our requirement that
![]() $f$
must never occur in the scope of any unbounded quantifier or aggregator, this is not the case, because the only cases where unbounded fan-in gates would be needed are the ones of unbounded quantifiers and aggregators.
$f$
must never occur in the scope of any unbounded quantifier or aggregator, this is not the case, because the only cases where unbounded fan-in gates would be needed are the ones of unbounded quantifiers and aggregators.
It remains to be shown that evaluating a number term without unbounded quantifiers and aggregators can be done in constant depth with bounded fan-in, that is in
![]() $\mathrm{NC}_R^{0}$
. This might seem surprising at first glance, as
$\mathrm{NC}_R^{0}$
. This might seem surprising at first glance, as
![]() $\mathrm{NC}_R^{0}$
circuits can essentially only access a constant number of their input gates. However, if no unbounded quantifiers or aggregators are present,
$\mathrm{NC}_R^{0}$
circuits can essentially only access a constant number of their input gates. However, if no unbounded quantifiers or aggregators are present,
![]() $\mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}}$
number terms only contain variables introduced by bounded aggregators or quantifiers, and their behaviour can essentially be hardwired. We will now show that the bounded aggregators do not introduce logarithmic depth, because, as mentioned above, only the unbounded quantifiers and aggregators would require unbounded fan-in gates and thus introduce logarithmic depth when being restricted to bounded fan-in. The saving grace here is that we only need to aggregate over the maximum two elements which satisfy the relativization of the bounded aggregation. The relativization only depends on the ranking of the input structure and not on the actual functions and relations given therein. Since the ranking is implicitly given to the circuit by the length of the input structure’s encoding and thus the number of input gates of the circuit, we thus essentially hard-code, which the two maximum elements satisfying the relativization are. Once we have done that we can simply use a single addition (multiplication) gate to mimic the behaviour of a bounded sum (product) construction which has as its two predecessors the circuits for the term, which is being aggregated over, with the two aforementioned maximum values satisfying the relativization.
$\mathrm{FO}_{R}[{\mathrm{Arb}_{R}}] +{\textrm{SUM}_{R}} +{\textrm{PROD}_{R}}$
number terms only contain variables introduced by bounded aggregators or quantifiers, and their behaviour can essentially be hardwired. We will now show that the bounded aggregators do not introduce logarithmic depth, because, as mentioned above, only the unbounded quantifiers and aggregators would require unbounded fan-in gates and thus introduce logarithmic depth when being restricted to bounded fan-in. The saving grace here is that we only need to aggregate over the maximum two elements which satisfy the relativization of the bounded aggregation. The relativization only depends on the ranking of the input structure and not on the actual functions and relations given therein. Since the ranking is implicitly given to the circuit by the length of the input structure’s encoding and thus the number of input gates of the circuit, we thus essentially hard-code, which the two maximum elements satisfying the relativization are. Once we have done that we can simply use a single addition (multiplication) gate to mimic the behaviour of a bounded sum (product) construction which has as its two predecessors the circuits for the term, which is being aggregated over, with the two aforementioned maximum values satisfying the relativization.
Putting this all together,
![]() $f$
gates only ever occur at constant depth in the circuit for
$f$
gates only ever occur at constant depth in the circuit for
![]() $t$
, and thus, replacing this gate by a copy of the circuit for
$t$
, and thus, replacing this gate by a copy of the circuit for
![]() $t$
and doing this iteratively
$t$
and doing this iteratively
![]() $(\log n)^i$
many times yields a circuit of depth
$(\log n)^i$
many times yields a circuit of depth
![]() ${\mathcal{O}}((\log n)^i)$
.
${\mathcal{O}}((\log n)^i)$
.
As mentioned previously, the basis of the idea for guarded functional recursion was the guarded predicative recursion used for plain first-order logic (Durand et al., Reference Durand, Haak and Vollmer2018). The same extension to polylogarithmic recursion depth that was showcased in this paper for
![]() $\mathrm{GFR}_{R}$
can be applied to
$\mathrm{GFR}_{R}$
can be applied to
![]() $\mathrm{GPR}$
. Similarly to the relativized aggregators in Notation 34, for relativized quantifiers, we write
$\mathrm{GPR}$
. Similarly to the relativized aggregators in Notation 34, for relativized quantifiers, we write
as a shorthand for
![]() $\exists x_1 \dots \exists x_k (\varphi \land \psi )$
and
$\exists x_1 \dots \exists x_k (\varphi \land \psi )$
and
as a shorthand for
![]() $\forall x_1, \dots, x_k (\varphi \to \psi )$
.
$\forall x_1, \dots, x_k (\varphi \to \psi )$
.
For an
![]() $\mathrm{FO}$
formula
$\mathrm{FO}$
formula
![]() $\varphi$
and a relation variable
$\varphi$
and a relation variable
![]() $P$
, we write
$P$
, we write
![]() $\varphi (P^+)$
if
$\varphi (P^+)$
if
![]() $P$
does not occur in the scope of a negation in
$P$
does not occur in the scope of a negation in
![]() $\varphi$
.
$\varphi$
.
Definition 49 (
![]() ${\mathrm{GPR}}^i$
). Let
${\mathrm{GPR}}^i$
). Let
![]() $\mathcal{R}$
be a set of relations such that
$\mathcal{R}$
be a set of relations such that
![]() $\mathrm{BIT}$
is definable in
$\mathrm{BIT}$
is definable in
![]() ${\mathrm{FO}}[\mathcal{R}]$
. The set of
${\mathrm{FO}}[\mathcal{R}]$
. The set of
![]() ${\mathrm{FO}}[\mathcal{R}] +{\mathrm{GPR}}^i$
formulae over
${\mathrm{FO}}[\mathcal{R}] +{\mathrm{GPR}}^i$
formulae over
![]() $\sigma$
is the set of formulae by the grammar for
$\sigma$
is the set of formulae by the grammar for
![]() ${\mathrm{FO}}[\mathcal{R}]$
formulae over
${\mathrm{FO}}[\mathcal{R}]$
formulae over
![]() $\sigma$
extended by the rule
$\sigma$
extended by the rule
where
![]() $\psi$
and
$\psi$
and
![]() $\theta$
are
$\theta$
are
![]() ${\mathrm{FO}}[\mathcal{R}]$
formulae over
${\mathrm{FO}}[\mathcal{R}]$
formulae over
![]() $\sigma$
,
$\sigma$
,
![]() ${\overline{x}},{\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}}$
are tuples of variables,
${\overline{x}},{\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}}$
are tuples of variables,
![]() $P$
is a relation variable and each atomic sub-formula involving
$P$
is a relation variable and each atomic sub-formula involving
![]() $P$
in
$P$
in
![]() $\theta$
$\theta$
-
1. is of the form
 $P({\overline{x}},{\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}})$
, the
$P({\overline{x}},{\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}})$
, the
 ${\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}}$
are in the scope of a guarded quantification
with
${\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}}$
are in the scope of a guarded quantification
with \begin{align*} Q{\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}}.\left (\bigvee \limits _{j = 1}^i \left ({\overline{z_j}} \leq{\overline{y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline{z_k}} \leq{\overline{y_k}}\right ) \land \xi ({\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}},{\overline{z_1}}, \dots,{\overline{z_i}},{\overline{z_{i+1}}}) \right ) \end{align*}
\begin{align*} Q{\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}}.\left (\bigvee \limits _{j = 1}^i \left ({\overline{z_j}} \leq{\overline{y_j}}/ 2 \land \bigwedge \limits _{k = 1}^{j - 1}{\overline{z_k}} \leq{\overline{y_k}}\right ) \land \xi ({\overline{y_1}}, \dots,{\overline{y_i}},{\overline{y_{i+1}}},{\overline{z_1}}, \dots,{\overline{z_i}},{\overline{z_{i+1}}}) \right ) \end{align*}
 $Q \in \{\forall,\exists \}$
,
$Q \in \{\forall,\exists \}$
,
 $\xi \in{\mathrm{FO}}[\mathcal{R}]$
with
$\xi \in{\mathrm{FO}}[\mathcal{R}]$
with
 $\xi$
not containing any relation symbols for relations given in the input structure and
$\xi$
not containing any relation symbols for relations given in the input structure and
-
2. never occurs in the scope of any quantification not guarded this way.
The semantics for
![]() ${\mathrm{GPR}}^i$
are defined analogously to the semantics for
${\mathrm{GPR}}^i$
are defined analogously to the semantics for
![]() ${\mathrm{GFR}_{R}^i}$
in Definition 35
.
${\mathrm{GFR}_{R}^i}$
in Definition 35
.
As stated, the proof of Theorem 48 can easily be adapted to the
![]() ${\mathrm{GPR}}^i$
operator, so we obtain the following result.
${\mathrm{GPR}}^i$
operator, so we obtain the following result.
Corollary 50.
-
1.
 ${\mathrm{FO}}[\mathrm{Arb}] +{\mathrm{GPR}}^i ={\mathrm{AC}}^i$
for
${\mathrm{FO}}[\mathrm{Arb}] +{\mathrm{GPR}}^i ={\mathrm{AC}}^i$
for
 $i \in{\mathbb{N}}$
$i \in{\mathbb{N}}$
-
2.
 ${\mathrm{FO}}[\mathrm{Arb}] +{\mathrm{GPR}}_{\mathrm{bound}}^i ={\mathrm{NC}}^i$
for
${\mathrm{FO}}[\mathrm{Arb}] +{\mathrm{GPR}}_{\mathrm{bound}}^i ={\mathrm{NC}}^i$
for
 $i \in{\mathbb{N}}_{\gt 0}$
$i \in{\mathbb{N}}_{\gt 0}$
5. Relationship Between Versions of
 $\textrm{AC}^{0}_{R}$
Over Different Integral Domains
$\textrm{AC}^{0}_{R}$
Over Different Integral Domains
Intuitively, a circuit deciding a problem in
![]() $\mathrm{AC}_{\mathbb{R}}^{0}$
should also be able to simulate circuits deciding problems in, for example,
$\mathrm{AC}_{\mathbb{R}}^{0}$
should also be able to simulate circuits deciding problems in, for example,
![]() $\mathrm{AC}_{{\mathbb{Z}}}^{0}$
and
$\mathrm{AC}_{{\mathbb{Z}}}^{0}$
and
![]() $\mathrm{AC}_{{\mathbb{Z}}_2}^{0}$
. Furthermore, we should be able to simulate an
$\mathrm{AC}_{{\mathbb{Z}}_2}^{0}$
. Furthermore, we should be able to simulate an
![]() $\mathrm{AC}_{{\mathbb{Z}}_3}^{0}$
circuit by an
$\mathrm{AC}_{{\mathbb{Z}}_3}^{0}$
circuit by an
![]() $\mathrm{AC}_{{\mathbb{Z}}_2}^{0}$
circuit by simulating the operations defined in the integral domain
$\mathrm{AC}_{{\mathbb{Z}}_2}^{0}$
circuit by simulating the operations defined in the integral domain
![]() ${\mathbb{Z}}_3$
by operations of tuples of
${\mathbb{Z}}_3$
by operations of tuples of
![]() ${\mathbb{Z}}_2$
. To formalize this intuition, we propose the notion of
${\mathbb{Z}}_2$
. To formalize this intuition, we propose the notion of
![]() $\mathfrak{C}$
simulation maps. Since the focus of this paper is on circuit complexity, we introduce simulation maps only in the context of circuit size and depth, but this formalism does not depend on specific properties of circuits and can easily be adapted to time and space complexity classes, which can, for example be defined via a suitably adapted definition of
$\mathfrak{C}$
simulation maps. Since the focus of this paper is on circuit complexity, we introduce simulation maps only in the context of circuit size and depth, but this formalism does not depend on specific properties of circuits and can easily be adapted to time and space complexity classes, which can, for example be defined via a suitably adapted definition of
![]() $R$
machines as presented in (Blum et al., Reference Blum, Cucker, Shub and Smale1998).
$R$
machines as presented in (Blum et al., Reference Blum, Cucker, Shub and Smale1998).
Definition 51.
Let
![]() $f_1, f_2 \colon{\mathbb{N}} \to{\mathbb{N}}$
be two functions and let
$f_1, f_2 \colon{\mathbb{N}} \to{\mathbb{N}}$
be two functions and let
![]() $\mathfrak{C}$
be a complexity class with
$\mathfrak{C}$
be a complexity class with
![]() $\mathfrak{C} \in \{{\boldsymbol{SizeDepth}_{}}(f_1, f_2),{\boldsymbol{UnbSizeDepth}_{}}(f_1, f_2)\}$
.
$\mathfrak{C} \in \{{\boldsymbol{SizeDepth}_{}}(f_1, f_2),{\boldsymbol{UnbSizeDepth}_{}}(f_1, f_2)\}$
.
A
![]() $\mathfrak{C}$
simulation map from an integral domain
$\mathfrak{C}$
simulation map from an integral domain
![]() $R_1$
to an integral domain
$R_1$
to an integral domain
![]() $R_2$
is an injective function
$R_2$
is an injective function
![]() $f \colon R_1^* \to R_2^*$
such that the following holds:
$f \colon R_1^* \to R_2^*$
such that the following holds:
For all
![]() $k \in{\mathbb{N}}_{\gt 0}$
and
$k \in{\mathbb{N}}_{\gt 0}$
and
![]() $A \in \mathfrak{C}_{R_1^{k}}$
, there exists an
$A \in \mathfrak{C}_{R_1^{k}}$
, there exists an
![]() $\ell \in{\mathbb{N}}_{\gt 0}$
and a language
$\ell \in{\mathbb{N}}_{\gt 0}$
and a language
![]() $B \in \mathfrak{C}_{R_2^{\ell }}$
such that for all
$B \in \mathfrak{C}_{R_2^{\ell }}$
such that for all
![]() ${\overline{x}} = (x_1, x_2, \dots, x_{\lvert{x}\rvert }$
) with
${\overline{x}} = (x_1, x_2, \dots, x_{\lvert{x}\rvert }$
) with
![]() $x_i \in R_1^k$
for all
$x_i \in R_1^k$
for all
![]() $i$
:
$i$
:
If there exists a
![]() $\mathfrak{C}$
simulation map from an integral domain
$\mathfrak{C}$
simulation map from an integral domain
![]() $R_1$
to an integral domain
$R_1$
to an integral domain
![]() $R_2$
, we also write
$R_2$
, we also write
![]() $\mathfrak{C}_{R_1}{\subseteq _{\mathrm{sim}}} \mathfrak{C}_{R_2}$
. The relations
$\mathfrak{C}_{R_1}{\subseteq _{\mathrm{sim}}} \mathfrak{C}_{R_2}$
. The relations
![]() $=_{\mathrm{sim}}$
and
$=_{\mathrm{sim}}$
and
![]() $\subsetneq _{\mathrm{sim}}$
are defined analogously.
$\subsetneq _{\mathrm{sim}}$
are defined analogously.
Similar to the formalism of reductions in classical complexity theory, the relation induced by
![]() ${\subseteq _{\mathrm{sim}}}^{\mathfrak{C}}$
is reflexive and transitive. Since in this work the main focus is on the
${\subseteq _{\mathrm{sim}}}^{\mathfrak{C}}$
is reflexive and transitive. Since in this work the main focus is on the
![]() $\mathrm{AC}_{{R}}$
and
$\mathrm{AC}_{{R}}$
and
![]() $\mathrm{NC}_R^{}$
hierarchies, we will proceed to restrict ourselves to these classes. But note that the simulation methods we show trivially extend to larger complexity classes.
$\mathrm{NC}_R^{}$
hierarchies, we will proceed to restrict ourselves to these classes. But note that the simulation methods we show trivially extend to larger complexity classes.
The formalism essentially divides our integral domains into a three-tier hierarchy. The first tier in this hierarchy consists of the complexity classes over finite integral domains, the second tier consists of the classes over integral domains which are simulatable by
![]() $\mathbb{Z}$
, and the third tier consists of classes over integral domains which are simulatable by
$\mathbb{Z}$
, and the third tier consists of classes over integral domains which are simulatable by
![]() $\mathbb{R}$
. In this setting, a complexity class over a certain integral domain is able to simulate the complexity classes over integral domains in the same tier or below. To make this explicit, we show the following three equalities:
$\mathbb{R}$
. In this setting, a complexity class over a certain integral domain is able to simulate the complexity classes over integral domains in the same tier or below. To make this explicit, we show the following three equalities:
Theorem 52. The following three equations hold:
-
1.
 $\mathrm{NC}_{{\mathbb{F}}_p}^{i}{=_{\mathrm{sim}}} \mathrm{NC}_{{\mathbb{F}}_q}^{i}$
for all prime powers
$\mathrm{NC}_{{\mathbb{F}}_p}^{i}{=_{\mathrm{sim}}} \mathrm{NC}_{{\mathbb{F}}_q}^{i}$
for all prime powers
 $p, q$
and
$p, q$
and
 $i\in \mathbb{N}$
.
$i\in \mathbb{N}$
. -
2.
 $\mathrm{NC}_{\mathbb{Z}}^{i}{=_{\mathrm{sim}}} \mathrm{NC}_{{\mathbb{Z}}[j_{k}]}^{i}$
for all
$\mathrm{NC}_{\mathbb{Z}}^{i}{=_{\mathrm{sim}}} \mathrm{NC}_{{\mathbb{Z}}[j_{k}]}^{i}$
for all
 $i\in \mathbb{N}$
.
$i\in \mathbb{N}$
. -
3.
 $\mathrm{NC}_{\mathbb{R}}^{i}{=_{\mathrm{sim}}} \mathrm{NC}_{{\mathbb{R}}[j_{k}]}^{i}$
for all
$\mathrm{NC}_{\mathbb{R}}^{i}{=_{\mathrm{sim}}} \mathrm{NC}_{{\mathbb{R}}[j_{k}]}^{i}$
for all
 $i\in \mathbb{N}$
.
$i\in \mathbb{N}$
.
Proof. We split the proof into two main parts: the finite case, in which simulations of integral domains are trivial, and the infinite case, where we have to be more careful about the new operations our simulating circuits execute to uphold that the structure of the circuits simulate are still integral domains.
The finite case. The simulation of finite integral domains is quite trivial. For
![]() $\mathrm{NC}_{{\mathbb{F}}_p}^{i}{\subseteq _{\mathrm{sim}}} \mathrm{NC}_{{\mathbb{F}}_q}^{i}$
where
$\mathrm{NC}_{{\mathbb{F}}_p}^{i}{\subseteq _{\mathrm{sim}}} \mathrm{NC}_{{\mathbb{F}}_q}^{i}$
where
![]() $p \leq q$
, the simulation is straightforward. For
$p \leq q$
, the simulation is straightforward. For
![]() $\mathrm{NC}_{{\mathbb{F}}_p}^{i}{\subseteq _{\mathrm{sim}}} \mathrm{NC}_{{\mathbb{F}}_q}^{i}$
where
$\mathrm{NC}_{{\mathbb{F}}_p}^{i}{\subseteq _{\mathrm{sim}}} \mathrm{NC}_{{\mathbb{F}}_q}^{i}$
where
![]() $p \gt q$
, choose the length of tuples that the
$p \gt q$
, choose the length of tuples that the
![]() $\mathrm{NC}_{{\mathbb{F}}_q}^{i}$
circuit uses to be the smallest
$\mathrm{NC}_{{\mathbb{F}}_q}^{i}$
circuit uses to be the smallest
![]() $k\in \mathbb{N}$
such that
$k\in \mathbb{N}$
such that
![]() $p \le q^k$
holds. Map the
$p \le q^k$
holds. Map the
![]() $p$
elements to the first
$p$
elements to the first
![]() $p$
elements in
$p$
elements in
![]() ${\mathbb{F}}_q^k$
and define addition and multiplication tables of constant size which simulate the addition and multiplication in
${\mathbb{F}}_q^k$
and define addition and multiplication tables of constant size which simulate the addition and multiplication in
![]() ${\mathbb{F}}_p$
.
${\mathbb{F}}_p$
.
The infinite case. We will prove that
![]() $\mathrm{NC}_{\mathbb{Z}}^{i}{=_{\mathrm{sim}}} \mathrm{NC}_{{\mathbb{Z}}[j_{k}]}^{i}$
for any fixed
$\mathrm{NC}_{\mathbb{Z}}^{i}{=_{\mathrm{sim}}} \mathrm{NC}_{{\mathbb{Z}}[j_{k}]}^{i}$
for any fixed
![]() $k\in \mathbb{N}$
. Note that the following proof does not depend on the countability of the set, so the proof for the uncountable case runs analogously. The direction
$k\in \mathbb{N}$
. Note that the following proof does not depend on the countability of the set, so the proof for the uncountable case runs analogously. The direction
![]() $\mathrm{NC}_{\mathbb{Z}}^{i}{\subseteq _{\mathrm{sim}}} \mathrm{NC}_{{\mathbb{Z}}[j_{k}]}^{i}$
is trivial. In the other direction, note that when simulating infinite integral domains, we can no longer hard-code the addition and multiplication tables in a trivial way. Furthermore, integral domains are not closed under cartesian products, since for two integral domains
$\mathrm{NC}_{\mathbb{Z}}^{i}{\subseteq _{\mathrm{sim}}} \mathrm{NC}_{{\mathbb{Z}}[j_{k}]}^{i}$
is trivial. In the other direction, note that when simulating infinite integral domains, we can no longer hard-code the addition and multiplication tables in a trivial way. Furthermore, integral domains are not closed under cartesian products, since for two integral domains
![]() $R_1, R_2$
, we have for
$R_1, R_2$
, we have for
![]() $R_1 \times R_2$
that
$R_1 \times R_2$
that
![]() $(1, 0)\times (0, 1) = (0, 0)$
using componentwise multiplication. We fix this by still using
$(1, 0)\times (0, 1) = (0, 0)$
using componentwise multiplication. We fix this by still using
![]() $k$
tuples to emulate the adjoint elements and using componentwise addition, but adapting multiplication so that it simulates multiplication of two elements with adjoint elements, where the
$k$
tuples to emulate the adjoint elements and using componentwise addition, but adapting multiplication so that it simulates multiplication of two elements with adjoint elements, where the
![]() $m$
th index of the tuple stands for the
$m$
th index of the tuple stands for the
![]() $m$
th power of the adjoint element, which we call
$m$
th power of the adjoint element, which we call
![]() $j$
here. Explicitly, we use the integral domain
$j$
here. Explicitly, we use the integral domain
![]() $({\mathbb{Z}}^k, +_{{\mathbb{Z}}^k}, \times _{{\mathbb{Z}}^k})$
, where
$({\mathbb{Z}}^k, +_{{\mathbb{Z}}^k}, \times _{{\mathbb{Z}}^k})$
, where
![]() $+_{{\mathbb{Z}}^k}$
is componentwise addition, and
$+_{{\mathbb{Z}}^k}$
is componentwise addition, and
![]() $\times _{{\mathbb{Z}}^k}$
is defined as follows:
$\times _{{\mathbb{Z}}^k}$
is defined as follows:
If we want to multiply two tuples of length
![]() $k$
$k$
we simulate the multiplication in the original, adjoint integral domain
by constructing the following matrix of constant size which corresponds to expanding the multiplication:
 \begin{align*} A = (a_{uv}) = \begin{pmatrix} x_1 y_1 & x_1 y_2 j & \cdots & x_1 y_k j^{k-1}\\[5pt] x_2 y_1 j & x_2 y_2 j^2 & \cdots & x_2 y_k j^k (= -x_2 y_k)\\[5pt] \vdots & \ddots & & \\[5pt] x_k y_1 j^{k-1} & x_k y_2 j^k (= -x_k y_2) & \cdots & x_k y_k j^{2k-2}\\[5pt] \end{pmatrix}. \end{align*}
\begin{align*} A = (a_{uv}) = \begin{pmatrix} x_1 y_1 & x_1 y_2 j & \cdots & x_1 y_k j^{k-1}\\[5pt] x_2 y_1 j & x_2 y_2 j^2 & \cdots & x_2 y_k j^k (= -x_2 y_k)\\[5pt] \vdots & \ddots & & \\[5pt] x_k y_1 j^{k-1} & x_k y_2 j^k (= -x_k y_2) & \cdots & x_k y_k j^{2k-2}\\[5pt] \end{pmatrix}. \end{align*}
Observe that, due to the fact that
![]() $j^k = -1$
, every entry
$j^k = -1$
, every entry
![]() $a_{uv}$
of the matrix contributes to the term at index
$a_{uv}$
of the matrix contributes to the term at index
![]() $(u + v - 2) \mod k$
in the tuple. The entry of the resulting tuple
$(u + v - 2) \mod k$
in the tuple. The entry of the resulting tuple
![]() $\overline{z}$
at index
$\overline{z}$
at index
![]() $\ell$
is thus
$\ell$
is thus
 \begin{equation*} z_\ell = \sum _{\substack {1 \le u, v\le k\\ (u + v - 2) \mod k = \ell }} a_{uv}. \end{equation*}
\begin{equation*} z_\ell = \sum _{\substack {1 \le u, v\le k\\ (u + v - 2) \mod k = \ell }} a_{uv}. \end{equation*}
Theorem 53. The following three equations hold:
-
1.
 ${\mathrm{AC}_{\mathbb{F}_p}^{i}}{=_{\mathrm{sim}}}{\mathrm{AC}_{\mathbb{F}_q}^{i}}$
for all prime powers
${\mathrm{AC}_{\mathbb{F}_p}^{i}}{=_{\mathrm{sim}}}{\mathrm{AC}_{\mathbb{F}_q}^{i}}$
for all prime powers
 $p, q$
and
$p, q$
and
 $i\in \mathbb{N}$
.
$i\in \mathbb{N}$
. -
2.
 ${\mathrm{AC}_{{\mathbb{Z}}}^{i}}{=_{\mathrm{sim}}}{\mathrm{AC}_{{\mathbb{Z}}[j_{k}]}^{k}}$
for all
${\mathrm{AC}_{{\mathbb{Z}}}^{i}}{=_{\mathrm{sim}}}{\mathrm{AC}_{{\mathbb{Z}}[j_{k}]}^{k}}$
for all
 $i\in \mathbb{N}$
.
$i\in \mathbb{N}$
. -
3.
 $\mathrm{AC}_{\mathbb{R}}^{i}{=_{\mathrm{sim}}} \mathrm{AC}_{{\mathbb{R}}_{[j_{k}]}}^{i}$
for all
$\mathrm{AC}_{\mathbb{R}}^{i}{=_{\mathrm{sim}}} \mathrm{AC}_{{\mathbb{R}}_{[j_{k}]}}^{i}$
for all
 $i\in \mathbb{N}$
.
$i\in \mathbb{N}$
.
Proof. We use the strategy from the proof of Theorem 52 and show that unbounded addition and multiplication can be realized without a significant increase in the complexity.
For
![]() $n$
given tuples of length
$n$
given tuples of length
![]() $k$
$k$
the simulation of unbounded addition by unbounded componentwise addition of tuples is straightforward. For unbounded multiplication, we extend the strategy for the bounded case by computing the matrix
![]() $A$
iteratively. That is, for a sequence of tuples
$A$
iteratively. That is, for a sequence of tuples
![]() ${\overline{x}}_1, \ldots,{\overline{x}}_n$
, first compute the matrix
${\overline{x}}_1, \ldots,{\overline{x}}_n$
, first compute the matrix
![]() $A_1$
from the tuples
$A_1$
from the tuples
![]() ${\overline{x}}_1$
and
${\overline{x}}_1$
and
![]() ${\overline{x}}_2$
, resulting in a tuple
${\overline{x}}_2$
, resulting in a tuple
![]() ${\overline{z}}_1$
. The matrix
${\overline{z}}_1$
. The matrix
![]() $A_2$
is then computed from the tuples
$A_2$
is then computed from the tuples
![]() ${\overline{z}}_1$
and
${\overline{z}}_1$
and
![]() ${\overline{x}}_3$
, and so on. In the resulting tuple
${\overline{x}}_3$
, and so on. In the resulting tuple
![]() $\overline{z}$
, the value of each tuple entry can only depend on the values
$\overline{z}$
, the value of each tuple entry can only depend on the values
![]() $x_{i, j}$
. So to simulate an unbounded multiplication gate, we need only an unbounded multiplication gate with a linear number of predecessors.
$x_{i, j}$
. So to simulate an unbounded multiplication gate, we need only an unbounded multiplication gate with a linear number of predecessors.
Corollary 54.
For all
![]() $i\in \mathbb{N}$
, we have
$i\in \mathbb{N}$
, we have
![]() $\mathrm{NC}_{\mathbb{R}}^{i}{=_{\mathrm{sim}}} \mathrm{NC}_{\mathbb{C}}^{i}$
and
$\mathrm{NC}_{\mathbb{R}}^{i}{=_{\mathrm{sim}}} \mathrm{NC}_{\mathbb{C}}^{i}$
and
![]() $\mathrm{AC}_{\mathbb{R}}^{i}{=_{\mathrm{sim}}} \mathrm{AC}_{\mathbb{C}}^{i}$
.
$\mathrm{AC}_{\mathbb{R}}^{i}{=_{\mathrm{sim}}} \mathrm{AC}_{\mathbb{C}}^{i}$
.
Proof.
Observe that
![]() ${\mathbb{C}} \cong{\mathbb{R}}[j_{(2)}]$
.
${\mathbb{C}} \cong{\mathbb{R}}[j_{(2)}]$
.
Lemma 55.
For all
![]() $i\in \mathbb{N}$
, we have
$i\in \mathbb{N}$
, we have
![]() $\mathrm{NC}_{\mathbb{Z}}^{i}{=_{\mathrm{sim}}} \mathrm{NC}_{\mathbb{Q}}^{i}$
and
$\mathrm{NC}_{\mathbb{Z}}^{i}{=_{\mathrm{sim}}} \mathrm{NC}_{\mathbb{Q}}^{i}$
and
![]() $\mathrm{AC}_{\mathbb{Z}}^{i}{=_{\mathrm{sim}}} \mathrm{AC}_{\mathbb{Q}}^{i}$
.
$\mathrm{AC}_{\mathbb{Z}}^{i}{=_{\mathrm{sim}}} \mathrm{AC}_{\mathbb{Q}}^{i}$
.
Proof.
For
![]() $\mathrm{NC}_{\mathbb{Z}}^{i}{\subseteq _{\mathrm{sim}}} \mathrm{NC}_{\mathbb{Q}}^{i}$
(resp.
$\mathrm{NC}_{\mathbb{Z}}^{i}{\subseteq _{\mathrm{sim}}} \mathrm{NC}_{\mathbb{Q}}^{i}$
(resp.
![]() $\mathrm{AC}_{\mathbb{Z}}^{i}{\subseteq _{\mathrm{sim}}} \mathrm{AC}_{\mathbb{Q}}^{i}$
), take
$\mathrm{AC}_{\mathbb{Z}}^{i}{\subseteq _{\mathrm{sim}}} \mathrm{AC}_{\mathbb{Q}}^{i}$
), take
![]() $f(x) \;:=\; x$
and for
$f(x) \;:=\; x$
and for
![]() $\mathrm{NC}_{\mathbb{Q}}^{i}{\subseteq _{\mathrm{sim}}} \mathrm{NC}_{\mathbb{Z}}^{i}$
(resp.
$\mathrm{NC}_{\mathbb{Q}}^{i}{\subseteq _{\mathrm{sim}}} \mathrm{NC}_{\mathbb{Z}}^{i}$
(resp.
![]() $\mathrm{AC}_{\mathbb{Q}}^{i}{\subseteq _{\mathrm{sim}}} \mathrm{AC}_{\mathbb{Z}}^{i}$
), take
$\mathrm{AC}_{\mathbb{Q}}^{i}{\subseteq _{\mathrm{sim}}} \mathrm{AC}_{\mathbb{Z}}^{i}$
), take
![]() $f(x) \;:=\; (a, b)$
, where
$f(x) \;:=\; (a, b)$
, where
![]() $x = \frac{a}{b}$
.
$x = \frac{a}{b}$
.
Lemma 56.
For all
![]() $i \in{\mathbb{N}}$
,
$i \in{\mathbb{N}}$
,
![]() $\mathrm{NC}_{\mathbb{Q}}^{i}{\subsetneq _{\mathrm{sim}}} \mathrm{NC}_{\mathbb{R}}^{i}$
and
$\mathrm{NC}_{\mathbb{Q}}^{i}{\subsetneq _{\mathrm{sim}}} \mathrm{NC}_{\mathbb{R}}^{i}$
and
![]() $\mathrm{AC}_{\mathbb{Q}}^{i}{\subsetneq _{\mathrm{sim}}} \mathrm{AC}_{\mathbb{R}}^{i}$
.
$\mathrm{AC}_{\mathbb{Q}}^{i}{\subsetneq _{\mathrm{sim}}} \mathrm{AC}_{\mathbb{R}}^{i}$
.
Proof.
We use the fact that
![]() $\mathbb{R}$
is a transcendental field extension of
$\mathbb{R}$
is a transcendental field extension of
![]() $\mathbb{Q}$
, that is there is no finite set of numbers
$\mathbb{Q}$
, that is there is no finite set of numbers
![]() $M$
which we can adjoin to
$M$
which we can adjoin to
![]() $\mathbb{Q}$
in order to get
$\mathbb{Q}$
in order to get
![]() ${\mathbb{Q}}[M] ={\mathbb{R}}$
. In our setting, this means that we cannot simulate all numbers
${\mathbb{Q}}[M] ={\mathbb{R}}$
. In our setting, this means that we cannot simulate all numbers
![]() $r \in{\mathbb{R}}$
by a set of finite tuples
$r \in{\mathbb{R}}$
by a set of finite tuples
![]() $(a_0, \ldots, a_n)$
of numbers where
$(a_0, \ldots, a_n)$
of numbers where
![]() $a_0,\ldots,a_n\in{\mathbb{Q}}$
.
$a_0,\ldots,a_n\in{\mathbb{Q}}$
.
6. Conclusion
In this paper, we introduced algebraic complexity classes with respect to algebraic circuits over integral domains. We showed a logical characterization for
![]() $\mathrm{AC}_{R}^{0}$
and further characterizations for the
$\mathrm{AC}_{R}^{0}$
and further characterizations for the
![]() $\mathrm{AC}_{R}$
and
$\mathrm{AC}_{R}$
and
![]() $\mathrm{NC}_R^{}$
hierarchies, using a generalization of the
$\mathrm{NC}_R^{}$
hierarchies, using a generalization of the
![]() $\mathrm{GPR}$
operator of Durand et al. (Reference Durand, Haak and Vollmer2018). We constructed a formalism to be able to compare the expressiveness of complexity classes with different underlying integral domains. We then showed that using this formalism, we obtain a hierarchy of sets of complexity classes, each set being able to “simulate” the complexity classes from the sets below.
$\mathrm{GPR}$
operator of Durand et al. (Reference Durand, Haak and Vollmer2018). We constructed a formalism to be able to compare the expressiveness of complexity classes with different underlying integral domains. We then showed that using this formalism, we obtain a hierarchy of sets of complexity classes, each set being able to “simulate” the complexity classes from the sets below.
For future work, it would be interesting to investigate the logical characterizations made in this paper in the uniform setting. We know that for the real numbers, the characterization
![]() ${\mathrm{AC}_{\mathbb{R}}^{0}} = \mathrm{FO}_{{\mathbb{R}}}[\mathrm{Arb}_{\mathbb{R}}] +{\textrm{SUM}_{{\mathbb{R}}}} +{\textrm{PROD}_{{\mathbb{R}}}}$
holds both non-uniformly and for uniformity criteria given by polynomial time computable circuits (
${\mathrm{AC}_{\mathbb{R}}^{0}} = \mathrm{FO}_{{\mathbb{R}}}[\mathrm{Arb}_{\mathbb{R}}] +{\textrm{SUM}_{{\mathbb{R}}}} +{\textrm{PROD}_{{\mathbb{R}}}}$
holds both non-uniformly and for uniformity criteria given by polynomial time computable circuits (
![]() $\mathrm{P}_{\mathbb{R}}$
uniform), logarithmic time computable circuits (
$\mathrm{P}_{\mathbb{R}}$
uniform), logarithmic time computable circuits (
![]() $\mathrm{LT}_{\mathbb{R}}$
uniform) and first-order definable circuits (
$\mathrm{LT}_{\mathbb{R}}$
uniform) and first-order definable circuits (
![]() $\mathrm{FO}_{{\mathbb{R}}}$
uniform) (Barlag and Vollmer, Reference Barlag and Vollmer2021). We believe that the results we presented here hold in analogous uniform settings as well, though this would need to be further examined. The case of
$\mathrm{FO}_{{\mathbb{R}}}$
uniform) (Barlag and Vollmer, Reference Barlag and Vollmer2021). We believe that the results we presented here hold in analogous uniform settings as well, though this would need to be further examined. The case of
![]() $\mathrm{P}_R$
uniformity seems like it should follow relatively directly with similar ideas as in the
$\mathrm{P}_R$
uniformity seems like it should follow relatively directly with similar ideas as in the
![]() $\mathrm{AC}_{\mathbb{R}}^{0}$
setting. For
$\mathrm{AC}_{\mathbb{R}}^{0}$
setting. For
![]() $\mathrm{LT}_R$
and
$\mathrm{LT}_R$
and
![]() $\mathrm{FO}_R$
uniformity, though, some more work would be required, since polylogarithmic depth can neither be trivially simulated in logarithmic time nor can it be simply encoded in fixed length gate numbers, which is how the proofs for the real cases go. However, the periodic nature of the circuits simulating
$\mathrm{FO}_R$
uniformity, though, some more work would be required, since polylogarithmic depth can neither be trivially simulated in logarithmic time nor can it be simply encoded in fixed length gate numbers, which is how the proofs for the real cases go. However, the periodic nature of the circuits simulating
![]() ${\mathrm{GFR}_{R}^i}$
extensions makes it plausible, and they are describable in a more compact way.
${\mathrm{GFR}_{R}^i}$
extensions makes it plausible, and they are describable in a more compact way.
Another open direction is to find interesting problems (potentially even complete) for these new complexity classes. This could even provide new insights for the classical case.
A promising approach to the separation of algebraic circuit complexity classes could be an adaption of the approach taken by Cucker, who showed that the problem
![]() $\mathrm{FER}$
, which essentially asks whether a point lies on a Fermat curve, separates the (logarithmic time uniform)
$\mathrm{FER}$
, which essentially asks whether a point lies on a Fermat curve, separates the (logarithmic time uniform)
![]() $\mathrm{NC}_{\mathbb{R}}^{i}$
classes (Cucker, Reference Cucker1992). The same proof could also hold for the
$\mathrm{NC}_{\mathbb{R}}^{i}$
classes (Cucker, Reference Cucker1992). The same proof could also hold for the
![]() $\mathrm{NC}_{\mathbb{C}}^{i}$
classes.
$\mathrm{NC}_{\mathbb{C}}^{i}$
classes.
Another model deserving of the name “algebraic circuit” is arithmetic circuits in the sense of Valiant (Reference Valiant1979). This model is similar to the model presented here, with the exception that generally, only addition and multiplication gates are permitted. Hence, there is no
![]() $sign$
or comparison function, which gives easy access to control flow constructions such as conditional statements and also allows for the study of functions which are not differentiable. Maybe the ideas presented in this paper can lead to further insights with regard to this model of computation as well.
$sign$
or comparison function, which gives easy access to control flow constructions such as conditional statements and also allows for the study of functions which are not differentiable. Maybe the ideas presented in this paper can lead to further insights with regard to this model of computation as well.
In the Boolean case, in addition to the
![]() $\mathrm{AC}$
and
$\mathrm{AC}$
and
![]() $\mathrm{NC}$
hierarchies, one commonly investigated hierarchy is the so-called
$\mathrm{NC}$
hierarchies, one commonly investigated hierarchy is the so-called
![]() $\mathrm{SAC}$
hierarchy. This hierarchy is defined by bounding the fan-in of only one gate type, that is either the conjunction or the disjunction gates. It is known that it does not make a difference in that setting which gate type is bounded. A possible next step is to define a sensible analogue of the SAC hierarchy in the algebraic setting or as a previous step in the real setting. We believe that in the algebraic case, it does make a difference which gate type we bound. The next step is to decide which version of bounded gates yields the more interesting class and afterwards one can relate it to any
$\mathrm{SAC}$
hierarchy. This hierarchy is defined by bounding the fan-in of only one gate type, that is either the conjunction or the disjunction gates. It is known that it does not make a difference in that setting which gate type is bounded. A possible next step is to define a sensible analogue of the SAC hierarchy in the algebraic setting or as a previous step in the real setting. We believe that in the algebraic case, it does make a difference which gate type we bound. The next step is to decide which version of bounded gates yields the more interesting class and afterwards one can relate it to any
![]() ${\mathrm{GPR}}^i$
like operator in the real or the algebraic setting. This model could then possibly be useful to investigate algebraic structures where the respective operations do not adhere to the same axioms.
${\mathrm{GPR}}^i$
like operator in the real or the algebraic setting. This model could then possibly be useful to investigate algebraic structures where the respective operations do not adhere to the same axioms.
Acknowledgements
We thank Sebastian Berndt and Anselm Haak for fruitful discussions.
Appendix
A. Bounding Circuit Depth
In this section, we show in general how to bind the depth of a circuit with a recursively defined constraint on the number of gates in the layers of the circuit.
Definition 57.
Let
![]() $C$
be a circuit and let
$C$
be a circuit and let
![]() $L_k$
be the set of all gates
$L_k$
be the set of all gates
![]() $g\in C$
with
$g\in C$
with
![]() $\textit{depth}(g) = k$
. Then, we call
$\textit{depth}(g) = k$
. Then, we call
![]() $L_k$
the
$L_k$
the
![]() $k$
th layer of
$k$
th layer of
![]() $C$
.
$C$
.
Lemma 58.
Let
![]() $\mathcal C = (C_n)_{n\in \mathbb N}$
be a circuit family,
$\mathcal C = (C_n)_{n\in \mathbb N}$
be a circuit family,
![]() $f$
a sublinear function and
$f$
a sublinear function and
![]() $g_C(k)$
the number of gates at layer
$g_C(k)$
the number of gates at layer
![]() $k$
for a circuit
$k$
for a circuit
![]() $C\in \mathcal C$
. Furthermore, let
$C\in \mathcal C$
. Furthermore, let
![]() $\alpha \;:=\; 2^{-\frac{\log _2 n}{f(n)}}$
.
$\alpha \;:=\; 2^{-\frac{\log _2 n}{f(n)}}$
.
A circuit
![]() $C$
has depth
$C$
has depth
![]() ${\mathcal{O}}(f(n))$
if we request that for every layer
${\mathcal{O}}(f(n))$
if we request that for every layer
![]() $k$
, the inequality
$k$
, the inequality
![]() $g_C(k) \le \lfloor \alpha \cdot g_C(k-1)\rfloor$
holds.
$g_C(k) \le \lfloor \alpha \cdot g_C(k-1)\rfloor$
holds.
Proof.
We want to bound the depth of the circuit (i.e., the number of layers
![]() $k$
) by the sublinear function
$k$
) by the sublinear function
![]() $f$
. For any input size
$f$
. For any input size
![]() $n$
, we therefore set
$n$
, we therefore set
![]() $k = f(n) \lt n$
. Furthermore, if we require that the inequality
$k = f(n) \lt n$
. Furthermore, if we require that the inequality
![]() $g_C(k) \le \lfloor \alpha \cdot g_C(k-1)\rfloor$
holds, the circuit reaches its maximum depth when
$g_C(k) \le \lfloor \alpha \cdot g_C(k-1)\rfloor$
holds, the circuit reaches its maximum depth when
![]() $n\alpha ^k\le 1$
holds, since the factor of
$n\alpha ^k\le 1$
holds, since the factor of
![]() $\alpha$
is applied
$\alpha$
is applied
![]() $k$
times, once for each layer. Substitution yields
$k$
times, once for each layer. Substitution yields
 \begin{align*} n\cdot \alpha ^k\le 1 &\Longleftrightarrow n\cdot{2^{-\frac{\log _2 n}{f(n)}}}^k\le 1\\[5pt] & \Longleftrightarrow n\cdot 2^{-\log _2 n}\le 1. \end{align*}
\begin{align*} n\cdot \alpha ^k\le 1 &\Longleftrightarrow n\cdot{2^{-\frac{\log _2 n}{f(n)}}}^k\le 1\\[5pt] & \Longleftrightarrow n\cdot 2^{-\log _2 n}\le 1. \end{align*}
Corollary 59.
A circuit
![]() $C$
has depth
$C$
has depth
![]() ${\mathcal{O}}((\log _2 n)^i)$
if we request that for every layer
${\mathcal{O}}((\log _2 n)^i)$
if we request that for every layer
![]() $k$
, the inequality
$k$
, the inequality
![]() $g_C(k) \le \left \lfloor 2^{-\frac{\log _2 n}{(\log _2 n)^i}} \cdot g_C(k-1)\right \rfloor$
holds.
$g_C(k) \le \left \lfloor 2^{-\frac{\log _2 n}{(\log _2 n)^i}} \cdot g_C(k-1)\right \rfloor$
holds.
B. Examples for the Sequence
 $d(n, c, i)$
$d(n, c, i)$
Here, we develop two examples of the sequence
![]() $d(n, c, i)$
from Definition 42. Table 3 shows the sequence
$d(n, c, i)$
from Definition 42. Table 3 shows the sequence
![]() ${d}(8, 1, 2)$
. Since
${d}(8, 1, 2)$
. Since
![]() $c \cdot \lfloor \log _2 8\rfloor - 1 = 2$
, each element of
$c \cdot \lfloor \log _2 8\rfloor - 1 = 2$
, each element of
![]() ${d}(8, 1, 2)$
contains
${d}(8, 1, 2)$
contains
![]() $i = 2$
tuples of length
$i = 2$
tuples of length
![]() $2$
. Each line is one element of the sequence, and the columns determine the tuples in the elements. This means that the first element here is the element
$2$
. Each line is one element of the sequence, and the columns determine the tuples in the elements. This means that the first element here is the element
![]() $(11, 11)$
, the second one is
$(11, 11)$
, the second one is
![]() $(11, 01)$
and so on.
$(11, 01)$
and so on.
Table 3. The sequence
![]() ${d}(8, 1, 2)$
${d}(8, 1, 2)$

Table 4. The sequence
![]() ${d}(8, 2, 2)$
${d}(8, 2, 2)$

Table 4 shows the sequence
![]() ${d}(8, 2, 2)$
. Since
${d}(8, 2, 2)$
. Since
![]() $c \cdot \lfloor \log _2 8\rfloor - 1 = 5$
, each element of
$c \cdot \lfloor \log _2 8\rfloor - 1 = 5$
, each element of
![]() ${d}(8, 2, 2)$
contains
${d}(8, 2, 2)$
contains
![]() $i = 2$
tuples of length
$i = 2$
tuples of length
![]() $5$
. Each line is one element of the sequence, and the columns determine the tuples in the elements. This means that the first element here is the element
$5$
. Each line is one element of the sequence, and the columns determine the tuples in the elements. This means that the first element here is the element
![]() $(11111, 11111)$
, the second one is
$(11111, 11111)$
, the second one is
![]() $(11111, 01111)$
and so on.
$(11111, 01111)$
and so on.
C. Proof of Lemma 46
Lemma 60.
Let
![]() $L$
be in
$L$
be in
![]() $\mathrm{AC}_{R}^{i}$
or
$\mathrm{AC}_{R}^{i}$
or
![]() $\mathrm{NC}_R^{i}$
via the circuit family
$\mathrm{NC}_R^{i}$
via the circuit family
![]() ${\mathcal{C}} = (C_n)_{n \in{\mathbb{N}}}$
. Then, there exists a circuit family
${\mathcal{C}} = (C_n)_{n \in{\mathbb{N}}}$
. Then, there exists a circuit family
![]() ${\mathcal{C}}' = (C'_n)_{n \in{\mathbb{N}}}$
deciding
${\mathcal{C}}' = (C'_n)_{n \in{\mathbb{N}}}$
deciding
![]() $L$
, such that for all
$L$
, such that for all
![]() $n \in{\mathbb{N}}$
and each gate
$n \in{\mathbb{N}}$
and each gate
![]() $g$
in
$g$
in
![]() $C'_n$
, each path from an input gate to
$C'_n$
, each path from an input gate to
![]() $g$
in
$g$
in
![]() $C'_n$
has the same length. We call
$C'_n$
has the same length. We call
![]() $C'_n$
a balanced DAG.
$C'_n$
a balanced DAG.
Proof.
Let
![]() $L$
be in
$L$
be in
![]() $\mathrm{AC}_{R}^{i}$
or
$\mathrm{AC}_{R}^{i}$
or
![]() $\mathrm{NC}_R^{i}$
via
$\mathrm{NC}_R^{i}$
via
![]() ${\mathcal{C}} = (C_n)_{n \in{\mathbb{N}}}$
. For each circuit
${\mathcal{C}} = (C_n)_{n \in{\mathbb{N}}}$
. For each circuit
![]() $C_n \in{\mathcal{C}}$
, we construct a circuit
$C_n \in{\mathcal{C}}$
, we construct a circuit
![]() $C'_n$
, such that
$C'_n$
, such that
![]() $f_{C_n} = f_{C'_n}$
and for each gate
$f_{C_n} = f_{C'_n}$
and for each gate
![]() $g$
in
$g$
in
![]() $C'_n$
, all input
$C'_n$
, all input
![]() $g$
paths in
$g$
paths in
![]() $C'_n$
have the same length. We transform
$C'_n$
have the same length. We transform
![]() $C_n$
into
$C_n$
into
![]() $C'_n$
by creating paths of dummy gates to replace edges that go over more than one level of depth.
$C'_n$
by creating paths of dummy gates to replace edges that go over more than one level of depth.
Let the depth of
![]() $C_n$
be bounded by
$C_n$
be bounded by
![]() $c_1 \cdot (\log _2 n)^i$
, and let its size be bounded by
$c_1 \cdot (\log _2 n)^i$
, and let its size be bounded by
![]() $c_2 \cdot n^{c_3}$
. We proceed by structural induction over the depth
$c_2 \cdot n^{c_3}$
. We proceed by structural induction over the depth
![]() $d$
of gates
$d$
of gates
![]() $g$
in
$g$
in
![]() $C_n$
, that is, the maximum length of paths from an input gate to
$C_n$
, that is, the maximum length of paths from an input gate to
![]() $g$
.
$g$
.
-
 $d = 1$
: Each gate
$d = 1$
: Each gate
 $g$
at depth
$g$
at depth
 $d$
is a direct successor of an input gate. Therefore, no changes need to be made, since all gates at depth
$d$
is a direct successor of an input gate. Therefore, no changes need to be made, since all gates at depth
 $d$
only have input
$d$
only have input
 $g$
paths of length
$g$
paths of length
 $1$
and therefore have the desired property.
$1$
and therefore have the desired property. -
 $d \to d + 1$
: For each gate at depth
$d \to d + 1$
: For each gate at depth
 $d+1$
, all predecessors are gates of depth
$d+1$
, all predecessors are gates of depth
 $\lt d+1$
for which it holds that all paths from input gates to them are of the same length. Keep all those predecessors at depth
$\lt d+1$
for which it holds that all paths from input gates to them are of the same length. Keep all those predecessors at depth
 $d$
as they are and replace the edge from predecessors of smaller depths
$d$
as they are and replace the edge from predecessors of smaller depths
 $d' \lt d$
to
$d' \lt d$
to
 $g$
by a path of dummy (unary addition) gates of length
$g$
by a path of dummy (unary addition) gates of length
 $d - d'$
. Now all paths from input gates to
$d - d'$
. Now all paths from input gates to
 $g$
have exactly length
$g$
have exactly length
 $d + 1$
, and we only added at most
$d + 1$
, and we only added at most
 $c_1 \cdot (\log _2 n)^i$
gates per predecessor of
$c_1 \cdot (\log _2 n)^i$
gates per predecessor of
 $g$
. In total, the number of dummy gates added for
$g$
. In total, the number of dummy gates added for
 $g$
is bounded by
$g$
is bounded by
 $c_2 \cdot n^{c_3} \cdot c_1 \cdot (\log _2 n)^i$
.
$c_2 \cdot n^{c_3} \cdot c_1 \cdot (\log _2 n)^i$
.
The resulting circuit is
![]() $C'_n$
. Since addition gates with only a singular predecessor are essentially identity gates, the value of each gate in any computation of
$C'_n$
. Since addition gates with only a singular predecessor are essentially identity gates, the value of each gate in any computation of
![]() $C'_n$
remains the same. Thus,
$C'_n$
remains the same. Thus,
![]() $f_{C_n} = f_{C'_n}$
.
$f_{C_n} = f_{C'_n}$
.
Additionally, for each gate in
![]() $C_n$
, we add at most
$C_n$
, we add at most
![]() $c_1 \cdot (\log _2 n)^i \cdot c_2 \cdot n^{c_3}$
gates to arrive at
$c_1 \cdot (\log _2 n)^i \cdot c_2 \cdot n^{c_3}$
gates to arrive at
![]() $C'_n$
. Therefore, the size of
$C'_n$
. Therefore, the size of
![]() $C'_n$
is bounded by
$C'_n$
is bounded by
![]() $c_1 \cdot (\log _2 n)^i \cdot c_2 \cdot n^{c_3} \cdot c_2 \cdot n^{c_3} = c_1 \cdot (\log _2 n)^i \cdot (c_2 \cdot n^{c_3})^2 \in{\mathcal{O}}(n^{{\mathcal{O}}(1)})$
. The depth of
$c_1 \cdot (\log _2 n)^i \cdot c_2 \cdot n^{c_3} \cdot c_2 \cdot n^{c_3} = c_1 \cdot (\log _2 n)^i \cdot (c_2 \cdot n^{c_3})^2 \in{\mathcal{O}}(n^{{\mathcal{O}}(1)})$
. The depth of
![]() $C'_n$
does not change, since we only ever add gates, when longer paths within
$C'_n$
does not change, since we only ever add gates, when longer paths within
![]() $C_n$
exist so that they end up at the same length.
$C_n$
exist so that they end up at the same length.
In total,
![]() $C'_n$
computes the same function as
$C'_n$
computes the same function as
![]() $C_n$
– and thus decides
$C_n$
– and thus decides
![]() $L$
– and has the property that for each of its gates
$L$
– and has the property that for each of its gates
![]() $g$
, all input
$g$
, all input
![]() $g$
paths have the same length.
$g$
paths have the same length.